natas level 8
This level looks fairly similar to one of the prior ones. We have to supply a passphrase, and we’re given the source code for the page on the server side so we can figure out what exactly it’s doing. Rather than importing the string from a file though, this one has the answer in an encoded form, so we can’t see the value immediately. What we can do, however, is look at the function that’s doing the encoding and try to devise a way to reverse the process.
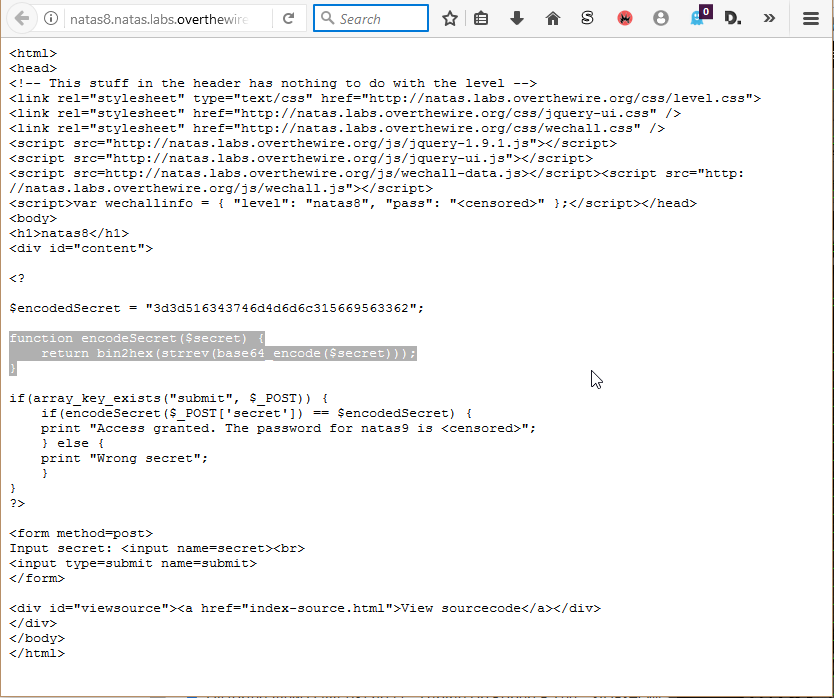
So, it looks like the string is being converted into base64, reversed, and then changed into a hexidecimal string. So, in order to determine the original value, we need to convert it back to decimal, reverse it, and then decode the base64 value. I’m sure that php probably has some kind of REPL, but I know from experience that there are various sites online that allow you run snippets of php code. I found one of those sites, reversed the order of the function calls, and then got the resulting string. Entering that value in the form back on natas8 produced the password for natas9.
natas level 7
Natas7 opens up with yet another sparse page, this time including a couple of links for home and about. Clicking on them doesn’t seem to reveal much of interest. Checking the source code, we’re offered a more explicit hint: <!-- hint: password for webuser natas8 is in /etc/natas_webpass/natas8 -->
Ok, with that in mind, the obvious intention is to somehow trick this page into giving us the contents of that file. We have to ask ourselves exactly what we have control over in the given situation. If we had been attentive while checking the home and about links, we might’ve noticed that instead of directing us to different pages, it appears to be passing different parameters back to the index page.
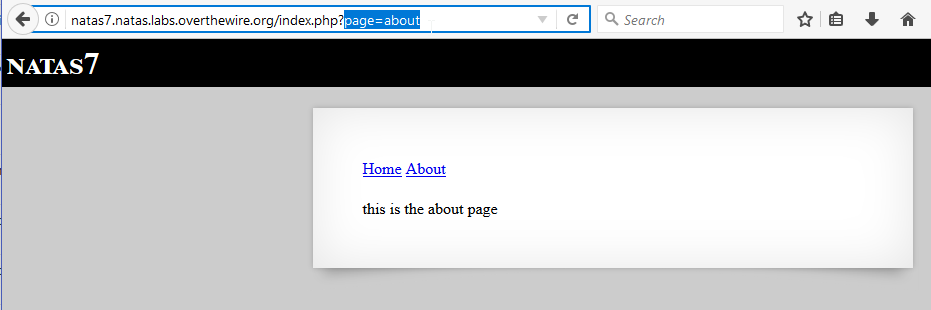
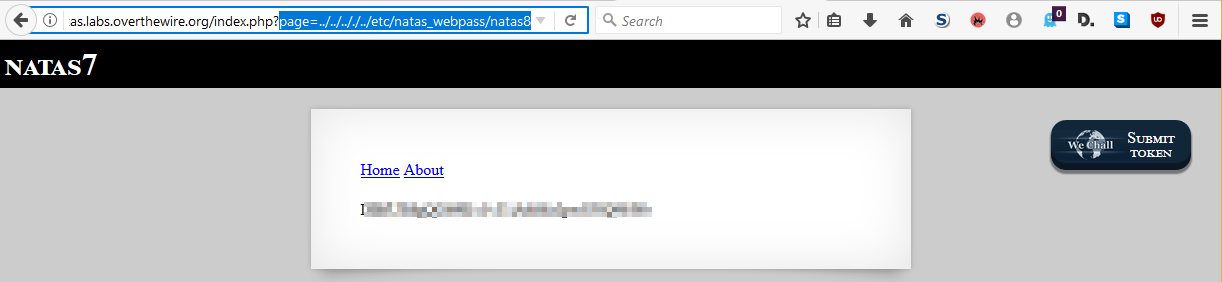
From this, we might make the assumption that the code on the server side is loading some kind of template based on the parameter being sent. At this point, it should be more clear what the intended solution is. If we can redirect the page to load the natas8 file instead, we can waltz into natas8 like we own the place. We don’t know where exactly the html is located on the server file system, but thankfully we can navigate to the root of the file server by throwing in as many parent directory references as we need.
natas level 6
When we load up level 6, we’re asked to input some kind of secret passphrase. Helpfully, there’s also a link to the source code for the php page on the server side. Taking a brief glance through the code, we can see that it’s checking some form parameters against a string presumably defined in includes/secret.inc. Can we investigate that file directly?
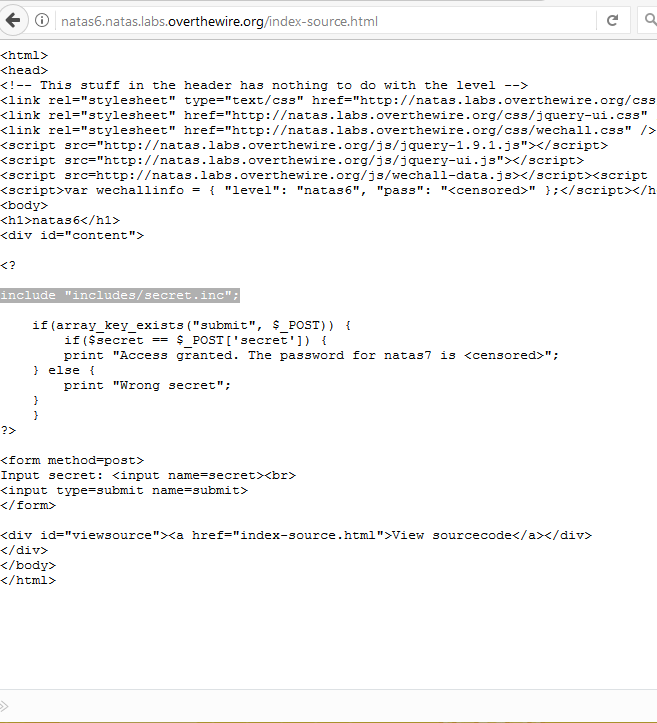
At first, we’re greeted with nothing but a blank screen. However, if we attempt to inspect the source of the page, we find the php code with the passphrase we’re looking for. Going back to the main screen and entering this value into the form gives us the password for natas7.

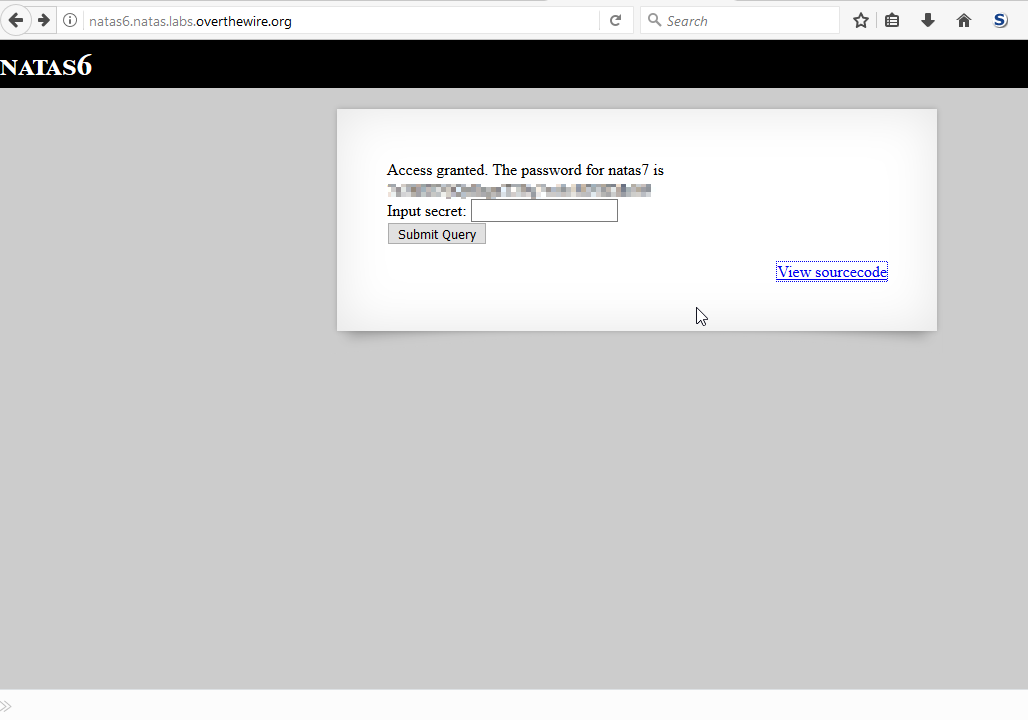
natas level 5
Natas 5 lets us know immediately that we’re not welcome by informing us that we’re not logged in. And how does it know that? Lets open up our cookies and take a look around.
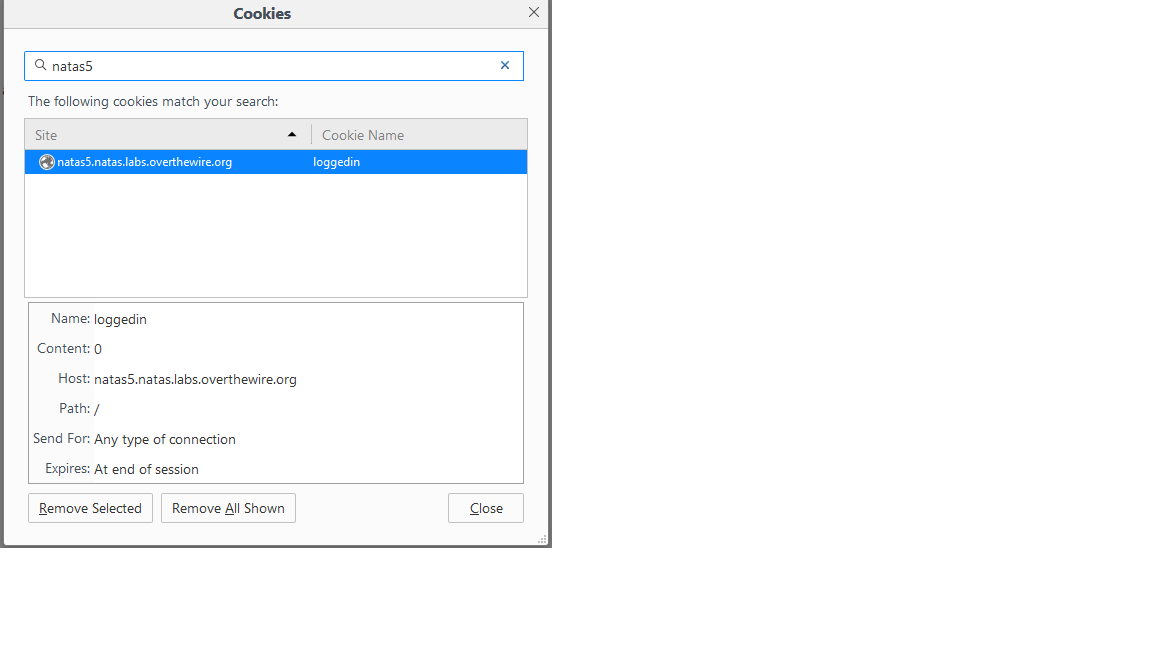
That looks interesting. It’s currently set at 0. What happens if we set it to one? There are probably various ways you can achieve this. Using a web proxy like the burp suite, or various add-ons depending on your browser. I’m using Firefox, so I used the developer toolbar to set the cookie (Shift+F2, cookie list, cookie set). With my cookie now set to its new value, I was able to reload the page and get the password for natas 6.
<h1>natas5</h1>
<div id="content">
Access granted. The password for natas6 is XXXXXXXXXXXXXXXXXXXXXXX</div>
natas level 4
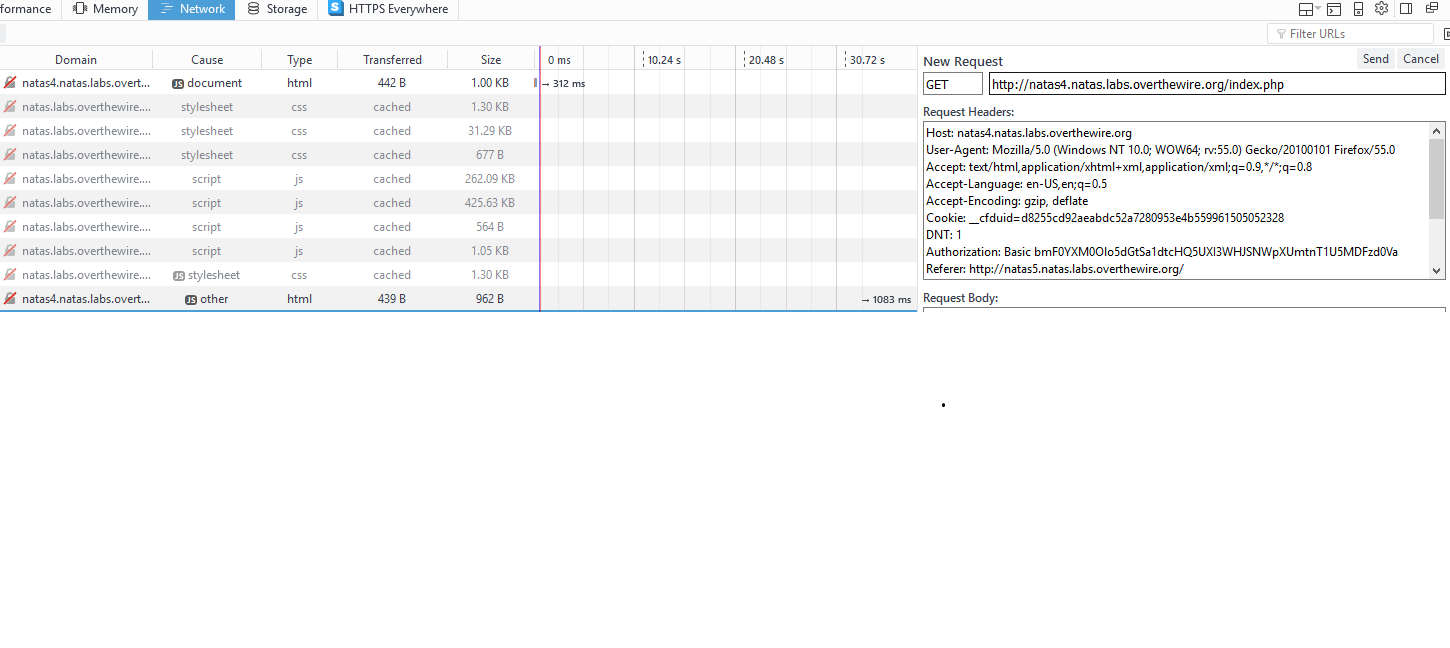
Upon loading level 4, we’re met with a message that tells us we’re denied access. Valid vistors should be coming from natas5. Obviously, we can’t access that URL yet, lacking either the ability to see the future or a handy time machine. So how does the page know where we’re coming from? That would be the referer attribute in the HTTP request header. Modern browsers being as developer friendly as they are, we can hit F12 and load up the console. In firefox, I can navigate over the network tab and look at the various requests used to load the page. Identifying the request for index.php, we can edit the headers and then resend the request. Adding Referer
http://natas5.natas.labs.overthewire.org/ to the header gives a response with the desired effect, the password for natas5.
natas level 3
We’re met with the same message this time, nothing on this page. Checking the source, there’s a comment taunting us that not even google will be able to find the answer this time. So, that should give us a hint. How would google find the answer? It would probably spider all of the links. So, how would that be stopped? By telling google (or its spidery minions) to take a hike. Lets check the robots.txt file.
/robots.txt
User-agent: *
Disallow: /s3cr3t/
Huh, that looks pretty suspicious. Checking this directory gives us another directory listing, complete with another user.txt file containing the password for natas4.
/s3cr3t/users.txt
natas4:XXXXXXXXXXXXXXXXXXXXXXXXXXXX
natas level 2
Natas 2 tells us that there’s nothing on the page. After we check the source, we find that’s not exactly true though. There’s a tiny one pixel image, which in itself is not very interesting. However, if we look at the URL (files/pixel.png), that appears much more promising. Checking /files shows there’s an entry called users.txt, which contains several passwords, the relevant one being for user natas3.
<body>
<h1>natas2</h1>
<div id="content">
There is nothing on this page
<img src="files/pixel.png">
</div>
</body>
Directory listing for files
Passwords:
# username:password
alice:BYNdCesZqW
bob:jw2ueICLvT
charlie:G5vCxkVV3m
natas3:XXXXXXXXXXXXXXXXXXXXXXXX
eve:zo4mJWyNj2
mallory:9urtcpzBmH
natas level 1
Same challenge, however we’ve been told that right clicking has been blocked. I guess I unknowingly solved this one with the first stage. Although one can get the source by right clicking, using ctrl+u is a quick shortcut which achieves the same effect.
<body oncontextmenu="javascript:alert('right clicking has been blocked!');return false;">
<h1>natas1</h1>
<div id="content">
You can find the password for the
next level on this page, but rightclicking has been blocked!
<!--The password for natas2 is XXXXXXXXXXXXXXXXXXXXXXXXX -->
</div>
</body>
natas level 0
Ok, I lied. I was going to tackle these completely in order, but just for some variety I decided to start Natas to see what kind of challenges it had. After some investigation, these appear to be web based. The first challenge tells us that the password can be found on the page itself. A quick ctrl+u, and we see that the password is embedded in the source.
<body>
<h1>natas0</h1>
<div id="content">
You can find the password for the next level on this page.
<!--The password for natas1 is XXXXXXXXXXXXXXXXXXXX -->
</div>
</body>
bandit level 24
We’re told that there’s a program listening on port 30002 that wants us to feed it the current level 24 password appended with a secret four digit pin. There’s a number of ways we could accomplish this (the box appears to have perl, ruby and python installed), but I went with a shell script. Bash is not a strong suite for me, so I hoped to maybe benefit a little from solving this exercise with a shell script.
The main problems are being able to format the pin correctly (we could need leading zeros), and to be able to pipe the results to the listening program. After some googling and man page reading, bash supports printf, so the formatting is easy enough. We can also use netcat to handle the network connections. Below is my solution:
#!/bin/bash
n="0"
bandit24="XXXXXXXXXXXXXXXXXXXXX"
while [ $n -lt 10000 ]
do
counter=$(printf "%04d" "$n")
((n=n+1))
echo "$bandit24 $counter"
echo "$bandit24 $counter" | nc 127.0.0.1 30002
done