I love getting these texts now, it’s like a tiny Christmas morning. What domains will I find? What payload will scammers deliver to my browser? What personal information will I give to others such that they might pwn me? Lets find out.
For a nice change of pace, this text wasn’t amazon related. Maybe they aren’t paying off anymore, maybe scammers are just trying something new, who knows. I was informed that my postal service package could not be delivered because the address was wrong, please log into update it.
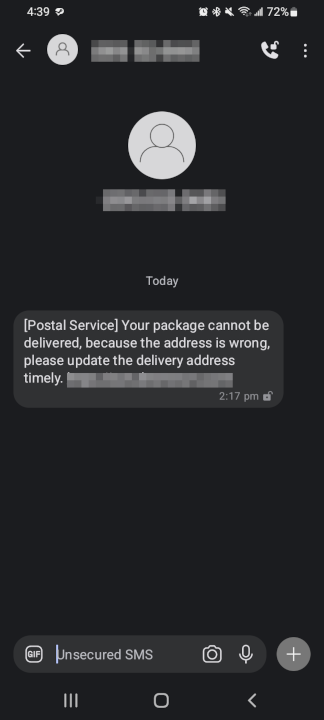
Lets do the standard stuff, like a basic whois lookup.
# whois XXX.com
Domain Name: XXX.COM
Registry Domain ID: 2713545092_DOMAIN_COM-VRSN
Registrar WHOIS Server: grs-whois.aliyun.com
Registrar URL: http://www.alibabacloud.com
Updated Date: 2022-07-25T09:14:16Z
Creation Date: 2022-07-25T09:13:03Z
Registry Expiry Date: 2023-07-25T09:13:03Z
Registrar: ALIBABA.COM SINGAPORE E-COMMERCE PRIVATE LIMITED
Registrar IANA ID: 3775
Registrar Abuse Contact Email: [email protected]
Registrar Abuse Contact Phone: +86.95187
Domain Status: ok https://icann.org/epp#ok
Name Server: NS1.ECPAGE.COM
Name Server: NS2.ECPAGE.COM
DNSSEC: unsigned
URL of the ICANN Whois Inaccuracy Complaint Form: https://www.icann.org/wicf/
Looks like this domain was literally registered today. Actually, wait… It says Singapore, which is undoubtedly in a different timezone from where I am… 🤔
I’ve looked it up, and apparently there’s somewhere around a 13 hour difference between myself and Singapore (look at me leaking personal info, gonna get doxed), so even if it wasn’t today, pretty darn recent.
One immediately noticeable difference in this scam is that the URL is pretty sparse, just the domain in fact. Not sure if that makes it better or worse. Like, will this completely USPS unrelated sounding domain be slightly more persuasive if I see a http://fakesite.com/USPS/evil/webpage/gonnastealyourinfo.html? Yet more social engineering questions for the ages. I imagine that if you’re not really paying attention and just scanning a URL quickly, having something recognizable in there would make it more successful, but maybe this is why I’m not running a professional phishing operating and these people are.
Fetching the source with curl, we’re met with a problem:
# curl https://XXX.com
<!DOCTYPE html><html lang=""><head><meta charset="utf-8"><meta http-equiv="X-UA-Compatible" content="IE=edge"><meta name="viewport" content="width=device-width,initial-scale=1"><link rel="icon" href="/favicon.ico"><link rel="stylesheet" href="/static/css/footer.css"><link rel="stylesheet" href="/static/css/bootstrap.min.css"><link rel="stylesheet" href="/static/css/calendar.css"><link rel="stylesheet" href="/static/css/datepicker3.css"><link rel="stylesheet" href="/static/css/main.css"><link rel="stylesheet" href="/static/css/tracking-cross-sell.css"><link rel="stylesheet" href="/static/css/jquery-ui.min.css"><link rel="stylesheet" href="/static/css/schedule-redelivery.css"><link rel="stylesheet" href="/static/css/megamenu-v2.css"><script>!function (p) { "use strict"; !function (t) { var s = window, e = document, i = p, c = "".concat("https:" === e.location.protocol ? "https://" : "http://", "sdk.51.la/js-sdk-pro.min.js"), n = e.createElement("script"), r = e.getElementsByTagName("script")[0]; n.type = "text/javascript", n.setAttribute("charset", "UTF-8"), n.async = !0, n.src = c, n.id = "LA_COLLECT", i.d = n; var o = function () { s.LA.ids.push(i) }; s.LA ? s.LA.ids && o() : (s.LA = p, s.LA.ids = [], o()), r.parentNode.insertBefore(n, r) }() }({ id: "JYSN0pGLOCKP4r90", ck: "JYSN0pGLOCKP4r90" });</script><title>Loading...</title><style>b
...snipping an obnoxious amount of inline css...
</style><link href="/css/chunk-6534330d.d577f886.css" rel="prefetch"><link href="/css/chunk-6c7911a2.068366b3.css" rel="prefetch"><link href="/css/chunk-7dc8a417.7074b3f4.css" rel="prefetch"><link href="/css/chunk-bc475d3c.206c8af0.css" rel="prefetch"><link href="/js/chunk-2d230676.334e6b3e.js" rel="prefetch"><link href="/js/chunk-6534330d.81965d6f.js" rel="prefetch"><link href="/js/chunk-6c7911a2.4b0647fb.js" rel="prefetch"><link href="/js/chunk-7dc8a417.e76f2c24.js" rel="prefetch"><link href="/js/chunk-bc475d3c.38297553.js" rel="prefetch"><link href="/css/app.26ea219b.css" rel="preload" as="style"><link href="/js/app.c90cd867.js" rel="preload" as="script"><link href="/js/chunk-vendors.fa93833a.js" rel="preload" as="script"><link href="/css/app.26ea219b.css" rel="stylesheet"></head><body><noscript><strong>We're sorry but smbv-sync-web-v3 doesn't work properly without JavaScript enabled. Please enable it to continue.</strong></noscript><div id="app"></div><script src="/js/chunk-vendors.fa93833a.js"></script><script src="/js/app.c90cd867.js"></script></body></html>
The numerous /js/chunk-*.js files make it seem like this is an actual js app that’s being executed. Unless we’re going to manually download those files and attempt to deobfuscate them, it seems like we’re going to need to do some dynamic analysis. I could’ve spun up a quick Linux or Windows VM, but instead I thought that since this came in text form, they’re probably expecting a mobile browser. I’m not an android dev, but figured there should be some way to do this from Google’s Android SDK. After spending some time poking around Android Studio’s UI, I eventually got an emulator running. Additionally, I had Android Studio itself configured to use a VM out in the cloud as a web proxy, both helping to obscure my IP and giving me a potentially useful log of HTTP traffic.
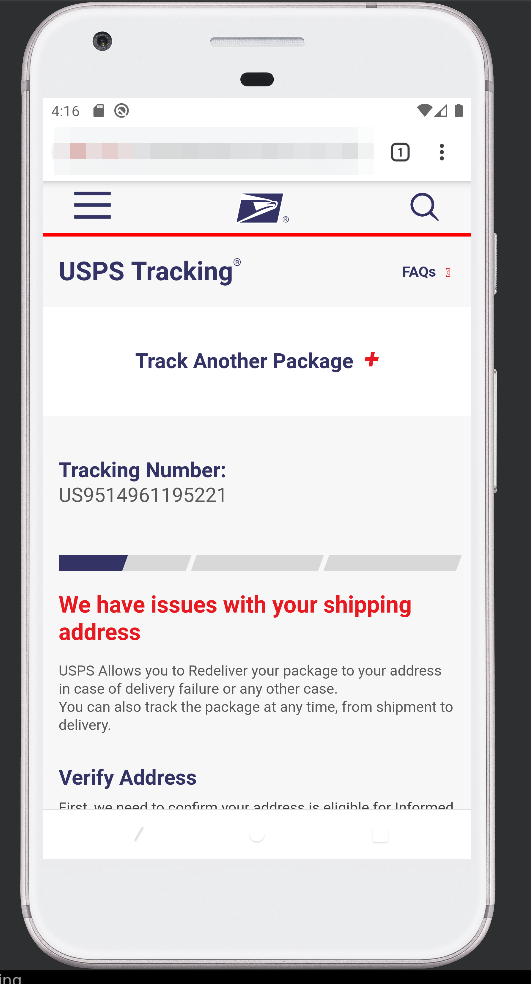
This is definitely the most impressive looking scam page I’ve seen. I would be hard pressed to spot any major differences between this and the actual USPS page. It gives me a little form that allows me to update my problematic shipping address, which I proceeded to populate with very real and extremely legitimate details about my physical location.
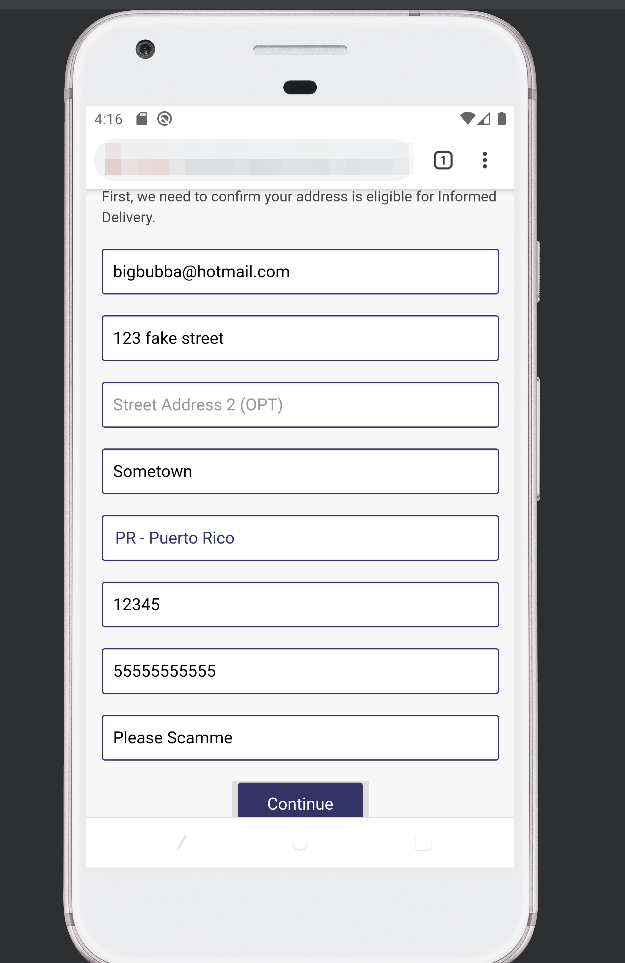
After filling out my details (as an aside, I wonder if this information is also being harvested and sold?), we finally get to the heart of this scam.
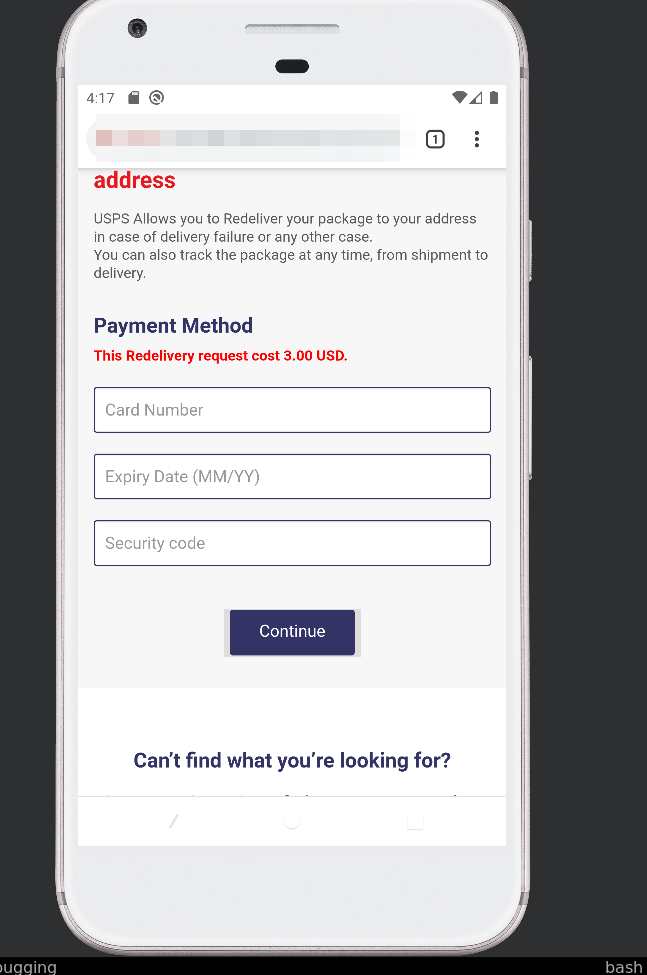
Excellent, a place to enter payment information to, I guess, compensate Uncle Sam for having failed to deliver the package the first time. I wish I had one of those temp “refillable” credit cards handy. I’d be really curious to see if they only do try to charge you the three dollars or if the number is even used immediately. Maybe these are aggregated together and sold in bulk? I’m not really sure how these thing are typically bought and sold.
That brings this one to an end though. I feel like I made some progress here. The last couple of scams I couldn’t get to properly complete, but taking the dynamic approach certainly seemed to make things easier. Maybe need to look into seeing if sandboxes for this kind of analysis could be automated to help track these things down.