My amazon account appears to be in serious trouble. At the time of this writing, if I don’t respond with roughly 24 hours, it’s going to be disabled. At least, that’s what my latest scam text has informed me of. Although this text scam isn’t exactly the same as my last one, it has a similar setup, utilizing multiple domains to try and accomplish whatever its evil motives are. Lets take a look and see what we can find.
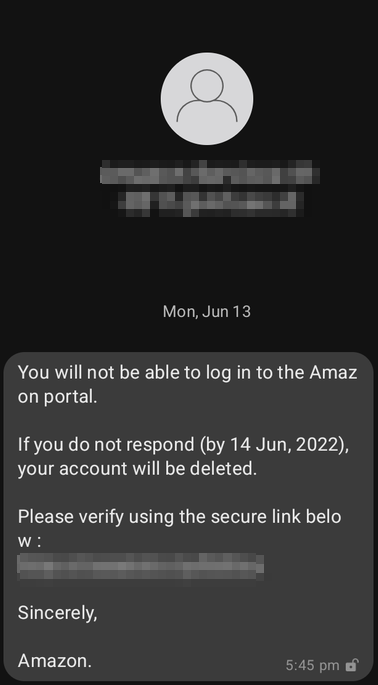
The initial text directed me here: https://masuksini.my/XXX
I have censored the full URL, but it’s pointless anyway because since the time I first recieved it, it appears to be inactive (I guess I really did have only 24 hours). But anyway, what is masuksini.my? A quick google makes it out to be a link shortener based in Malaysia.
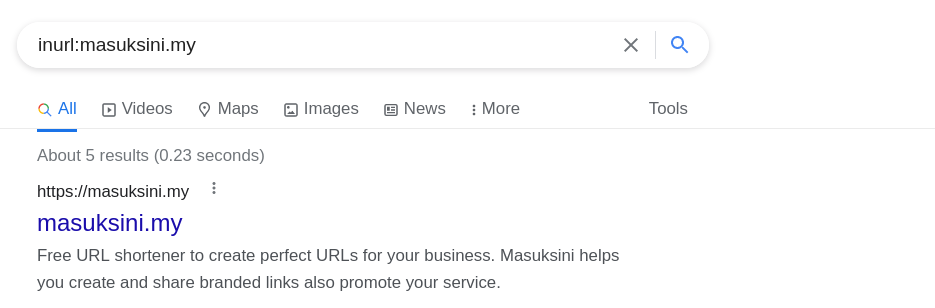
So, unlike the last scam that appeared to use a compromised domain, this one is using a shortener. Probably more convenient? Certainly less work and probably easier to replace if your initial link gets taken down.
Ok, so where did this go? Well, I can’t show you since I didn’t save the curl request from when it was active. That said, when it was active I got redirected to probably one of the worst domain names I could ever imagine using for phishing… https://webredir-scvrsecurepage.cocainespot.com/XXX
So… yeah. I mean, it’s attention grabbing, I’ll give it that.
└─$ whois cocainespot.com
Domain Name: COCAINESPOT.COM
Registry Domain ID: 2644511977_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.regtons.com
Registrar URL: http://regtons.com
Updated Date: 2021-10-05T15:54:53Z
Creation Date: 2021-09-29T19:11:22Z
Registry Expiry Date: 2022-09-29T19:11:22Z
...snip...
I didn’t see much of interest in the whois query, but just wanted to note that the domain was registered at least a little while ago. Based on the name of the site, I wouldn’t touch its ports through five different proxies. I guess the name might be a joke or something, but I really don’t want to take a chance and land my IP in some three letter agency’s database. However, we can always check the wayback machine and see if it has been crawled.
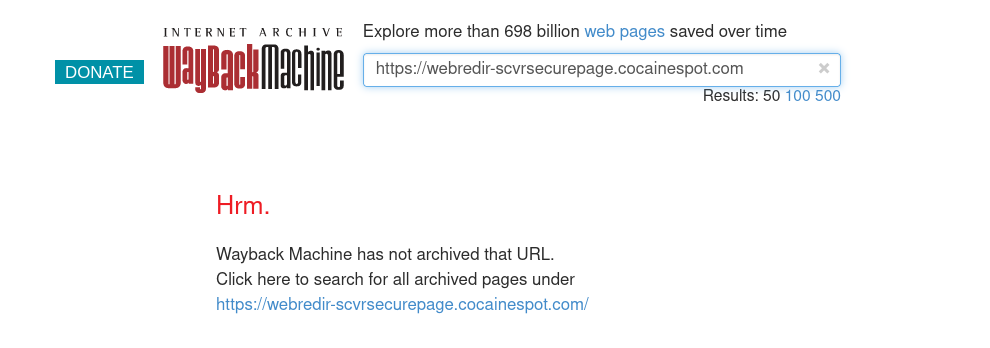
No luck. Checking for the main domain, does yield a hit though.
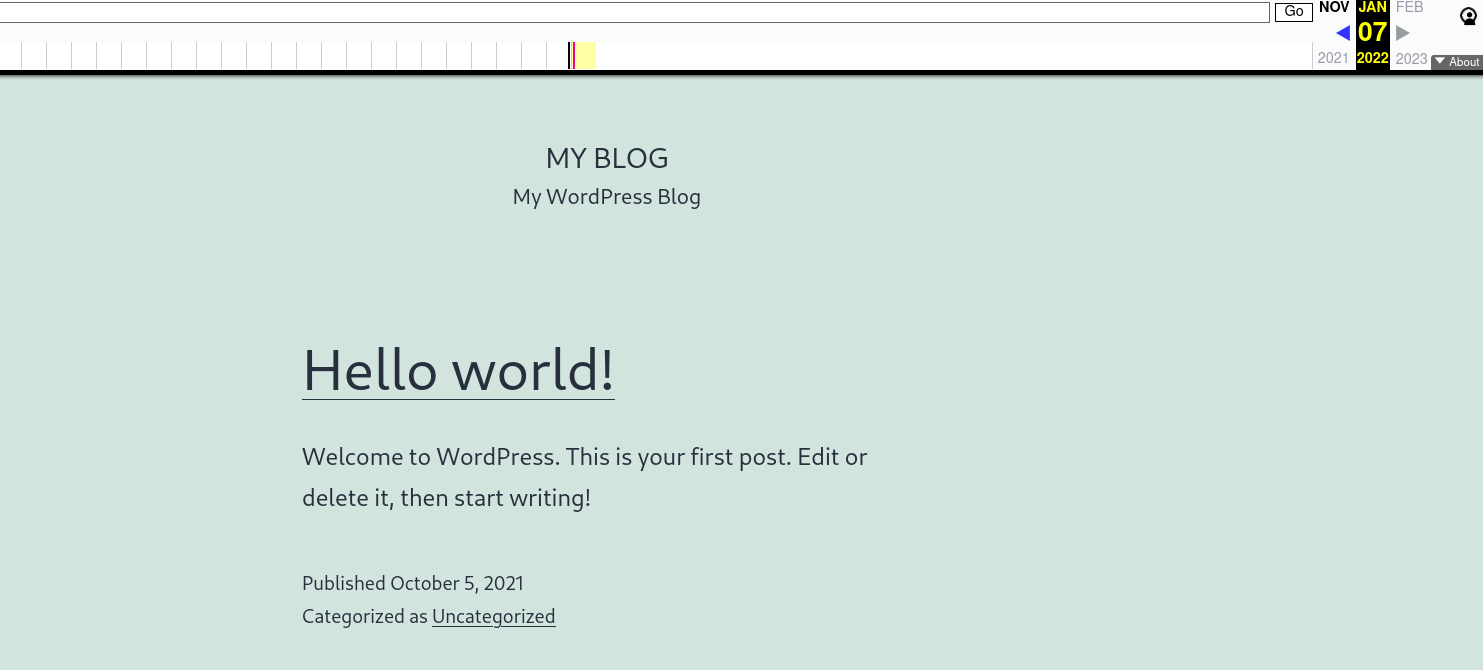
Ok, so in January of 2022, it looks like the site was just getting set up, and wouldn’t you know it, as a wordpress blog. If you’re going to be selling the kind of stuff that the name of this domain implies, wouldn’t you use something more secure than Wordpress?
I’m really curious about such an explicit domain. What else can we learn about it? I’m a novice (read: no experience whatsoever) with osint, but I did notice that we’re being directed to a subdomain. What other subdomains can we find? I was originally going to use sublist3r, but for whatever reason I was having a hard time compiling it from source, so instead I opted for amass, which I had much better luck with.
└─$ amass enum -d cocainespot.com
cocainespot.com
www.magicmushroompharm.cocainespot.com
webredir-scvrsecurepage.cocainespot.com
www.crackdispensary.cocainespot.com
webmail.cocainespot.com
whm.cocainespot.com
www.psilocinmushroom.cocainespot.com
www.psychedelicssolutions.cocainespot.com
www.illuminaticoterie.cocainespot.com
cpcontacts.cocainespot.com
hippysociety.cocainespot.com
cpcalendars.cocainespot.com
crackdispensary.cocainespot.com
psilocinmushroom.cocainespot.com
www.hippysociety.cocainespot.com
cpanel.cocainespot.com
www.redirect.secureaccount.cocainespot.com
mail.cocainespot.com
redirect.secureaccount.cocainespot.com
www.cocainespot.com
webdisk.cocainespot.com
magicmushroompharm.cocainespot.com
psychedelicssolutions.cocainespot.com
autodiscover.cocainespot.com
illuminaticoterie.cocainespot.com
www.webredir-scvrsecurepage.cocainespot.com
cpcalendars.crackdispensary.cocainespot.com
autoconfig.cocainespot.com
cpcontacts.crackdispensary.cocainespot.com
ftp.cocainespot.com
autoconfig.illuminaticoterie.cocainespot.com
webmail.illuminaticoterie.cocainespot.com
webdisk.illuminaticoterie.cocainespot.com
cpcontacts.psychedelicssolutions.cocainespot.com
whm.crackdispensary.cocainespot.com
cpanel.psilocinmushroom.cocainespot.com
webdisk.psilocinmushroom.cocainespot.com
webdisk.crackdispensary.cocainespot.com
cpanel.illuminaticoterie.cocainespot.com
autoconfig.crackdispensary.cocainespot.com
cpcalendars.magicmushroompharm.cocainespot.com
webdisk.magicmushroompharm.cocainespot.com
cpanel.crackdispensary.cocainespot.com
autodiscover.psychedelicssolutions.cocainespot.com
webdisk.hippysociety.cocainespot.com
webmail.magicmushroompharm.cocainespot.com
whm.illuminaticoterie.cocainespot.com
autoconfig.magicmushroompharm.cocainespot.com
autoconfig.psychedelicssolutions.cocainespot.com
webmail.psilocinmushroom.cocainespot.com
whm.magicmushroompharm.cocainespot.com
webmail.psychedelicssolutions.cocainespot.com
cpanel.magicmushroompharm.cocainespot.com
webmail.hippysociety.cocainespot.com
cpcalendars.illuminaticoterie.cocainespot.com
cpanel.psychedelicssolutions.cocainespot.com
cpanel.hippysociety.cocainespot.com
cpcalendars.hippysociety.cocainespot.com
webdisk.psychedelicssolutions.cocainespot.com
webmail.crackdispensary.cocainespot.com
autodiscover.illuminaticoterie.cocainespot.com
autodiscover.crackdispensary.cocainespot.com
cpcalendars.psilocinmushroom.cocainespot.com
autodiscover.hippysociety.cocainespot.com
autodiscover.psilocinmushroom.cocainespot.com
whm.hippysociety.cocainespot.com
whm.psychedelicssolutions.cocainespot.com
cpcontacts.psilocinmushroom.cocainespot.com
cpcalendars.psychedelicssolutions.cocainespot.com
OWASP Amass v3.19.2 https://github.com/OWASP/Amass
--------------------------------------------------------------------------------
69 names discovered - cert: 25, scrape: 44
--------------------------------------------------------------------------------
...snip...
Wow… I thought the main domain was pretty out there, but Amass has found subdomains that somehow, beyond any expectation, make this seem so over the top that it honestly feels like it’s starting to glow in the dark.
But where does it go?
So when I said I wouldn’t touch the site, I lied. No, I didn’t go to main domain, or poke around at any of the extraordinarily suspicious subdomains, but my curiosity was such that I did try fetching the URL that the last site had forwarded me to.
root@kali:~# curl -v https://webredir-scvrsecurepage.cocainespot.com/XXX
...snip...
> GET /XXX HTTP/1.1
> Host: webredir-scvrsecurepage.cocainespot.com
> User-Agent: curl/7.83.0
> Accept: */*
>
* TLSv1.3 (IN), TLS handshake, Newsession Ticket (4):
* TLSv1.3 (IN), TLS handshake, Newsession Ticket (4):
* old SSL session ID is stale, removing
* Mark bundle as not supporting multiuse
< HTTP/1.1 302 Found
< Server: nginx
< Date: Tue, 21 Jun 2022 03:16:44 GMT
< Content-Type: text/html; charset=UTF-8
< Content-Length: 0
< Connection: keep-alive
< Expires: Thu, 19 Nov 1981 08:52:00 GMT
< Cache-Control: no-store, no-cache, must-revalidate
< Pragma: no-cache
< location: https://google.com
<
* Connection #0 to host webredir-scvrsecurepage.cocainespot.com left intact
Alas, we get a redirected to google. This appears to be running theme in my amateur research into how these things operate. Site sees a request it doesn’t like? Redirect to something legitimate. I did a little manual probing with various user agents, but no joy. In a bit of serendipity, I accidentally submitted a blank user agent before pasting a value in, and weirdly, I get a location in the redirect that is not google.com.
root@kali:~# curl -A '' -v https://webredir-scvrsecurepage.cocainespot.com/XXX
> GET /XXX HTTP/1.1
> Host: webredir-scvrsecurepage.cocainespot.com
> Accept: */*
...snip...
< HTTP/1.1 302 Found
< Server: nginx
< Date: Tue, 21 Jun 2022 03:15:43 GMT
< Content-Type: text/html; charset=UTF-8
< Content-Length: 0
< Connection: keep-alive
< Expires: Thu, 19 Nov 1981 08:52:00 GMT
< Cache-Control: no-store, no-cache, must-revalidate
< Pragma: no-cache
< Set-Cookie: PHPSESSID=XXX; path=/
< location: https://intli-srvcsamzn.crabdance.com/?XXX
<
* Connection #0 to host webredir-scvrsecurepage.cocainespot.com left intact
The interesting thing here is that the command above is my most recent attempt. Earlier last week, I was getting redirected to https://site-rediramz.nerdpol.ovh/?XXX. Both of these sites appear to be dynamic DNS forwarders. You can see in the example below where I manually fetched the output from crabdance, these are services (which given that crabdance takes payments in bitcoin, are probably catering to criminals) that allow for updating DNS records on the fly. I’m most familiar with them being used for doing something like redirecting a domain to your home computer (which likely has an unstable IP given that your ISP can change it when it deems fit), but here the use appears to be more sinister.
root@kali:~# curl -v http://crabdance.com/ | tidy -i
...snip...
<!DOCTYPE html>
<html>
<head>
<meta name="generator" content=
"HTML Tidy for HTML5 for Linux version 5.6.0">
<title>Free domain sharing - Site not yet configured</title>
</head>
<body bgcolor="cornflowerblue">
<center>
<table width="75%" height="100%">
<tr>
<td align="middle">
<table cellpadding="10" cellspacing="10" bgcolor="white">
<tr>
<td>
<table border="0">
<tr>
<td><img src="/images/tree3.jpg"></td>
<td>
<font face="verdana, helvetica">Welcome!<br>
<br>
<b>crabdance.com</b> is being shared via
<a href="http://freedns.afraid.org/">Free
DNS</a>, a dynamic DNS domain sharing project
where members can setup, and administrate
their dns entries on their own remote
internet connected systems in real time.<br>
<br>
To create a free subdomain from any shared
domain, you can visit the <a href=
"http://freedns.afraid.org/domain/registry/">shared
domain list</a>.<br></font>
<hr>
<font face="verdana, helvetica">For any dns
related inquiries, questions, support,
comments, or misuse contact <a href=
"mailto:[email protected]?subject=dns%20question%20(via%20crabdance.com)">
[email protected]</a> for a quick
response.</font>
<hr>
<font face="verdana, helvetica"><a href=
"http://freedns.afraid.org/">Free DNS</a> is
serving 90,000+ domains, 3.7 million
subdomains, and processing 2,000+ dns queries
per second.<br></font>
</td>
</tr>
</table>
</td>
</tr>
</table>
</td>
</tr>
</table>
</center>
</body>
</html>
When I try the domain from the most recent response, dig say it’s pointing at 127.0.0.2, which is a loopback address. Not sure what this means exactly? I’m guessing either the attackers have temporarily/permanently disabled it, or it was flagged by the dynamic DNS provider and taken down.
root@kali:~# dig intli-srvcsamzn.crabdance.com
; <<>> DiG 9.18.1-1-Debian <<>> intli-srvcsamzn.crabdance.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 26033
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 512
;; QUESTION SECTION:
;intli-srvcsamzn.crabdance.com. IN A
;; ANSWER SECTION:
intli-srvcsamzn.crabdance.com. 1393 IN A 127.0.0.2
;; Query time: 8 msec
;; WHEN: Tue Jun 21 03:37:59 UTC 2022
;; MSG SIZE rcvd: 74
Given that I can’t get a response from the address in the last step, I guess this is where the trail goes cold. At some point I hope to be able to follow one of these scams to the point where I can actually get a response (a login form, some malware, something). I eagerly await the next suspicious text that comes my way.
Makes me wonder, is there a good way to get more these phishing attempts? In the past, I’ve set up honeypot servers to get samples of malware. Maybe it would be possible to get a voip number where I can recieve texts and start spamming it around the internet? Might be an interesting way to get more sample data.