In the midst of making my way through the overthewire challenges, I decided to also try some “boot to root” stuff, beacuse why not? I went browsing for some interesting targets, and settled for SickOS version 1.2. After powering on the VM, I brought up a seconday image running Kali. The obvious first step is to figure out the IP of the target. I’ve got both of the VMs set to run on a host only network, so after determining the IP of my Kali box, I can scan the appropriate range and look for the running instance of SickOs.
I used the -sn option with nmap, which specifies that we’re only doing host discovery, no port scanning. After a few seconds, I got back four addresses. One was my Kali box, and it seemed likely that the other address close to mine was my target.
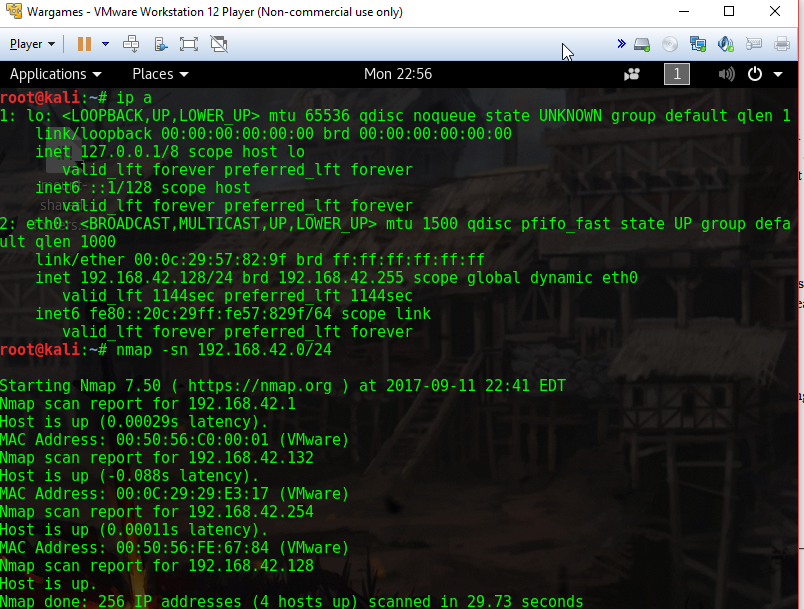
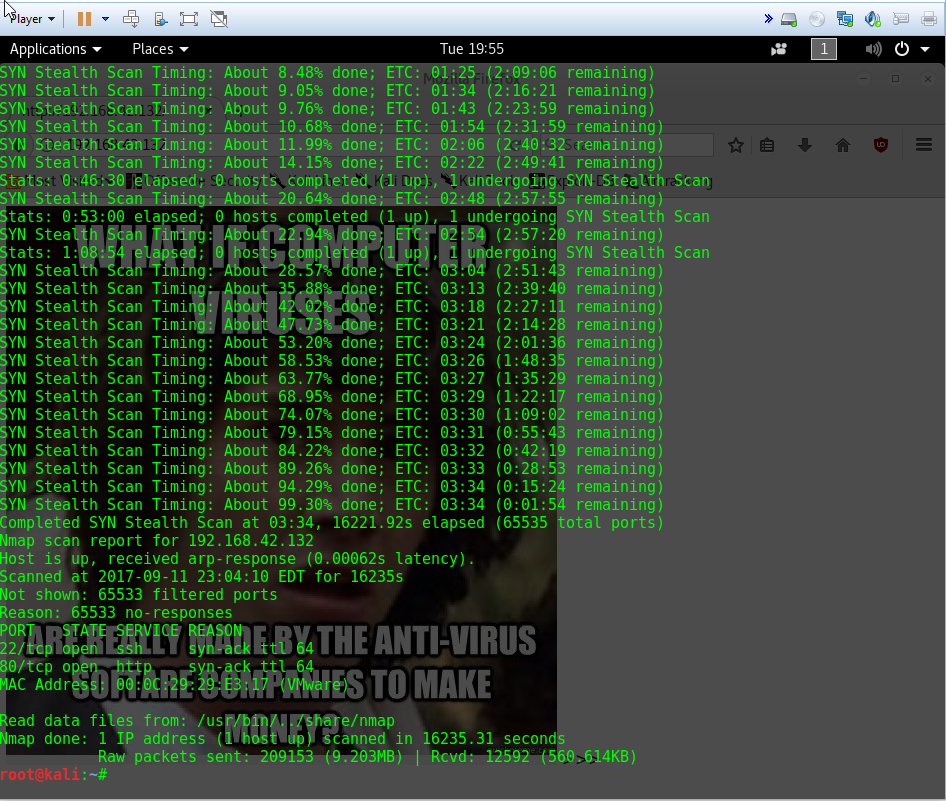
Now that I knew the IP, the next most logical step was to scan it. I used a syn scan (-sS), specified the entire range of ports (-p-), and asked nmap to be very verbose while it was scanning (-vvv). As per the steady updates, the scan was set to take over an hour, so I let it set while I went off to work on other challenges.
Unfortunately, after all of that time waiting, the only ports nmap detected as being open were 22 (ssh) and 80(http). Before I call it quits and investigate those two ports, I’m also going to try a UDP scan, because why not? I won’t know if anything is there unless I look.
I saved the results of the UDP scan to a file, and then grepped through it looking for no-response, using the -v flag to invert the matching logic and only showing me lines that don’t contain that text. Unfortunately, it seemed to have turned up bupkis. Oh well, at least we tried. Next time we’ll take a look at those open ports and see if anything interesting turns up.
root@kali:~# grep -v no-response 192.168.42.132_report
Starting Nmap 7.50 ( https://nmap.org ) at 2017-09-12 21:36 EDT
Initiating ARP Ping Scan at 21:36
Scanning 192.168.42.132 [1 port]
Completed ARP Ping Scan at 21:36, 0.22s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 21:36
Completed Parallel DNS resolution of 1 host. at 21:36, 13.01s elapsed
DNS resolution of 1 IPs took 13.01s. Mode: Async [#: 1, OK: 0, NX: 0, DR: 1, SF: 0, TR: 3, CN: 0]
Initiating UDP Scan at 21:36
Scanning 192.168.42.132 [65535 ports]
... progress text omitted...
Nmap scan report for 192.168.42.132
Host is up, received arp-response (0.00033s latency).
Scanned at 2017-09-12 21:36:37 EDT for 1335s
PORT STATE SERVICE REASON
MAC Address: 00:0C:29:29:E3:17 (VMware)
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 1335.79 seconds
Raw packets sent: 131071 (3.674MB) | Rcvd: 22 (1.540KB)