The next exercise tasks us with jumping to a particular place in memory. Thankfully, there’s a function pointer that gets placed on the stack, so conceptually it’s fairly similar to what we’ve been doing. The real problem here is determing where the function is in memory. The directions for the challenge advise checking out objdump, and it proves to be useful.
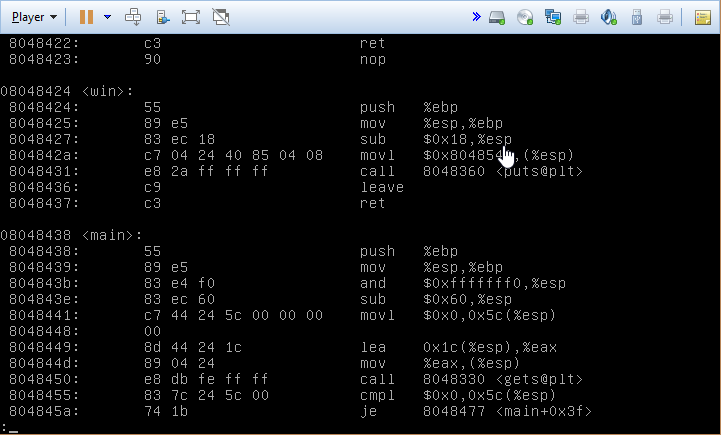
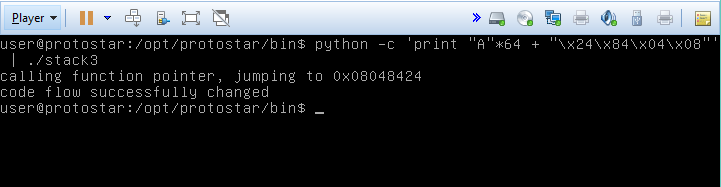
Using objdump -d, we get a dissasembly of the of the program, including the various functions. If we scroll down, we see the address defined for the win function 08048424. Using python for our one liner this time (why not?), we generate our string with the function address appended to the end, remembering that we have to write the bytes in reverse order due to the endianness of protostar.