I started looking at the other Krypton challenges, and while I plan to get around to them eventually, it’s not something that I want to work on at the moment. I’m done with Bandit, finished Leviathan, and still need to get back to SickOs and Natas. However, I’ve been wanting to learn more about Linux exploitation, and Protostar seemed like a good introduction to that. I also intend to start Narnia soon as I think it deals with similar material.
Protostar is vm that comes with various challenge binaries already on the box, so it feels kind of similar to overthewire. Instructions for each level are available at https://exploit-exercises.com/protostar/.
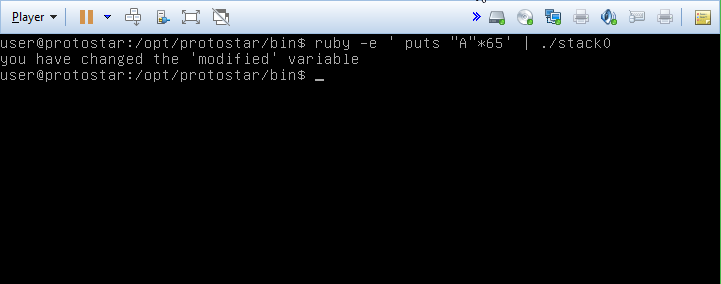
We’ll be starting with Stack0, which deals with memory corruption. The first challenge tasks us with modifying the variable “modified” in the following c program:
#include <stdlib.h>
#include <unistd.h>
#include <stdio.h>
int main(int argc, char **argv)
{
volatile int modified;
char buffer[64];
modified = 0;
gets(buffer);
if(modified != 0) {
printf("you have changed the 'modified' variable\n");
} else {
printf("Try again?\n");
}
}
This is possible for a couple of reasons. First, the order of the variables and how they’re declared. Second, the call to gets, which does not check the length of the string against the buffer it’s writing into. By abusing this fact, we can write past the end of the buffer and into the modified variable. In the following screenshot, I’ve printed out the addresses of the two variables.
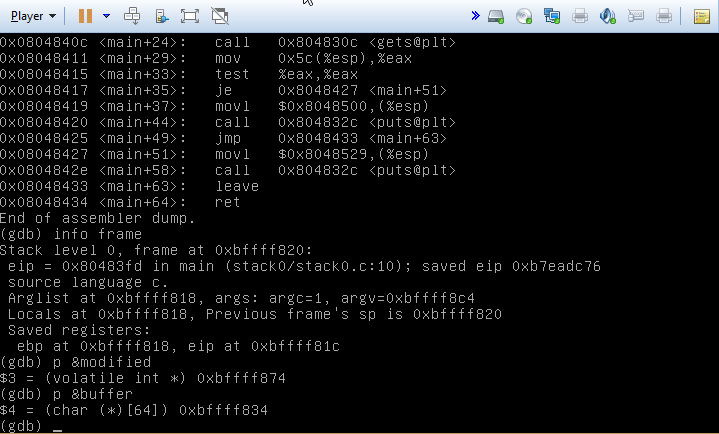
You can see that the stack is laid out something like this:
[0xbffff818] Stack base
| |
| |
[0xbffff834] char buffer[64]
| |
| |
| |
| |
| |
| |
[0xbfffff874] int modified
This makes it slightly easier to visual happens when we we feed more than 64 characters to the program.