This level looks fairly similar to one of the prior ones. We have to supply a passphrase, and we’re given the source code for the page on the server side so we can figure out what exactly it’s doing. Rather than importing the string from a file though, this one has the answer in an encoded form, so we can’t see the value immediately. What we can do, however, is look at the function that’s doing the encoding and try to devise a way to reverse the process.
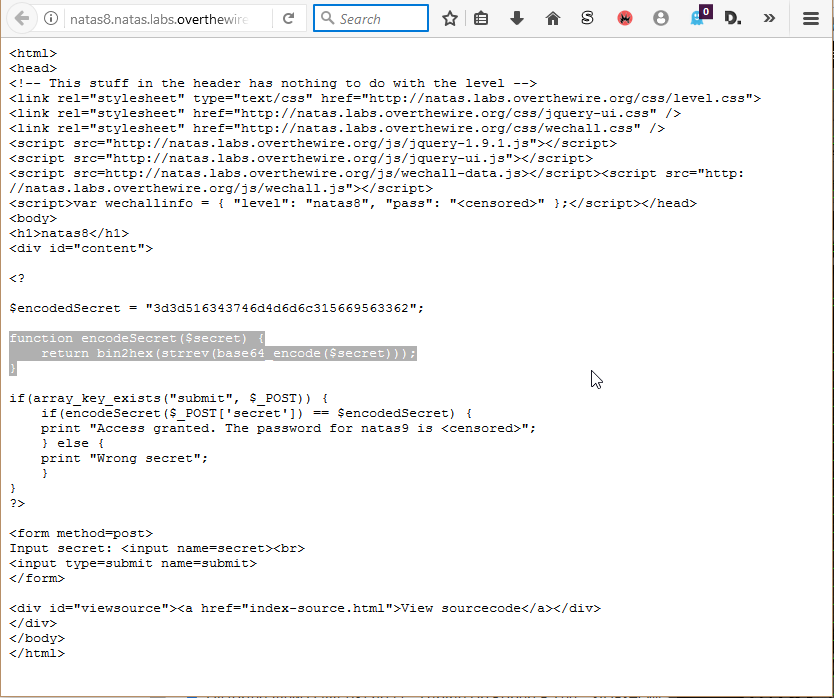
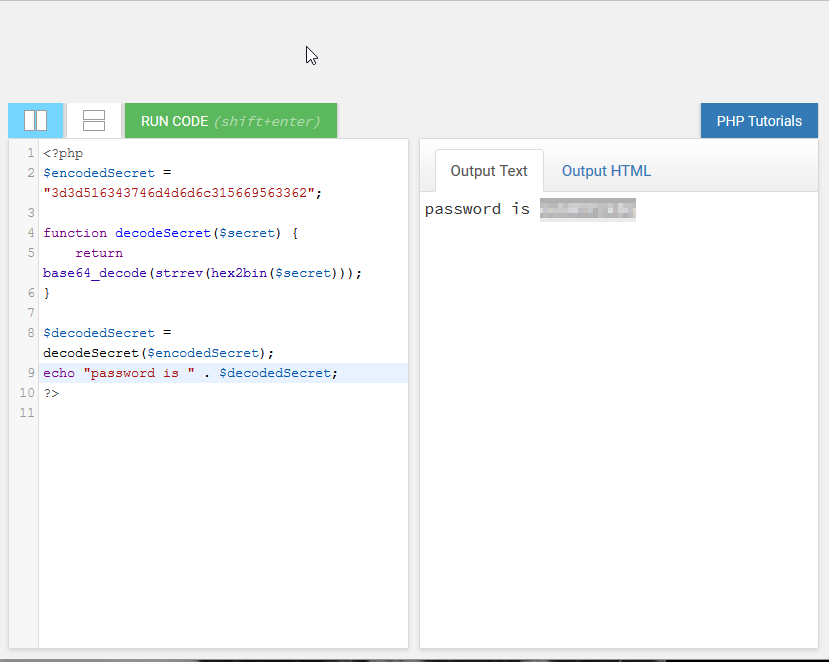
So, it looks like the string is being converted into base64, reversed, and then changed into a hexidecimal string. So, in order to determine the original value, we need to convert it back to decimal, reverse it, and then decode the base64 value. I’m sure that php probably has some kind of REPL, but I know from experience that there are various sites online that allow you run snippets of php code. I found one of those sites, reversed the order of the function calls, and then got the resulting string. Entering that value in the form back on natas8 produced the password for natas9.