When we load up level 6, we’re asked to input some kind of secret passphrase. Helpfully, there’s also a link to the source code for the php page on the server side. Taking a brief glance through the code, we can see that it’s checking some form parameters against a string presumably defined in includes/secret.inc. Can we investigate that file directly?
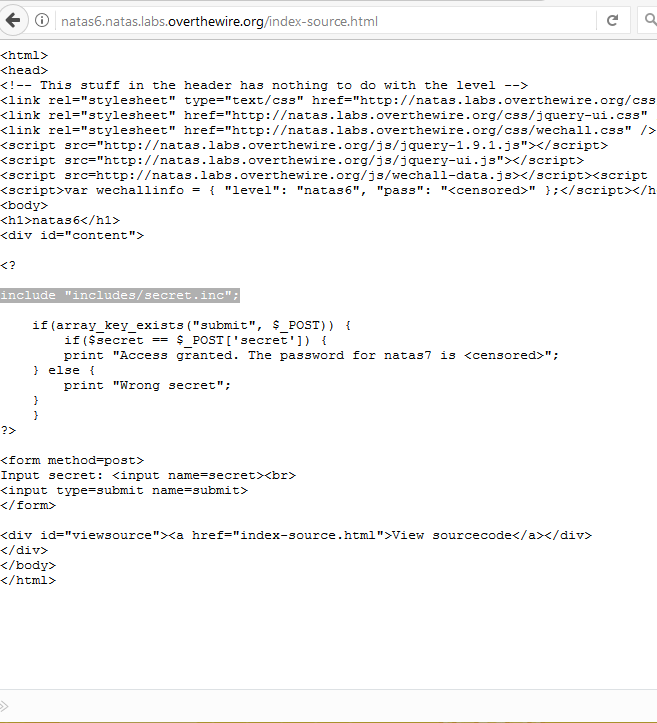
At first, we’re greeted with nothing but a blank screen. However, if we attempt to inspect the source of the page, we find the php code with the passphrase we’re looking for. Going back to the main screen and entering this value into the form gives us the password for natas7.