Upon listing our home directory on this challenge, we’re met with a program called check. It appears to be setuid, so we can assume that this is our ticket to the next level somehow. When we try to run it, we’re asked for a password. As might be expected, entering something random results in a message telling us that it’s wrong.
leviathan1@leviathan:~$ ls
check
leviathan1@leviathan:~$ ./check
password: bleah
Wrong password, Good Bye ...
leviathan1@leviathan:~$ file check
check: setuid ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked (uses shared libs), for GNU/Linux 2.6.24, BuildID[sha1]=4c5a895c73faa38da165925e8c0deeded68f5c1d, not stripped
leviathan1@leviathan:~$
My instincts would be to fire up gdb and set a breakpoint on main and step through the code, but the leviathan description mentioned that it was designed to be completed without any programming knowledge. So, since we’re not meant to use a debugger, how else can we see what it’s comparing against? My first thought was the strings command, which reads a binary file and prints out the anything that falls within the normal printable range. Running this command does give what looks to be some helpful possibilities, but none of them checked out.
leviathan1@leviathan:~$ strings -d ./check
/lib/ld-linux.so.2
libc.so.6
_IO_stdin_used
puts
__stack_chk_fail
printf
getchar
system
strcmp
__libc_start_main
__gmon_start__
GLIBC_2.4
GLIBC_2.0
PTRh`
QVh-
D$,1
D$%secrf
D$)et
D$ love
T$,e3
[^_]
password:
/bin/sh
Wrong password, Good Bye ...
;*2$"
leviathan1@leviathan:~$ ./check
password: love
Wrong password, Good Bye ...
leviathan1@leviathan:~$ ./check
password: secrf
Wrong password, Good Bye ...
leviathan1@leviathan:~$
Wondering what I was missing, I opened the file in vim. Vim is not a hex editor, but I was just curious what would happen.
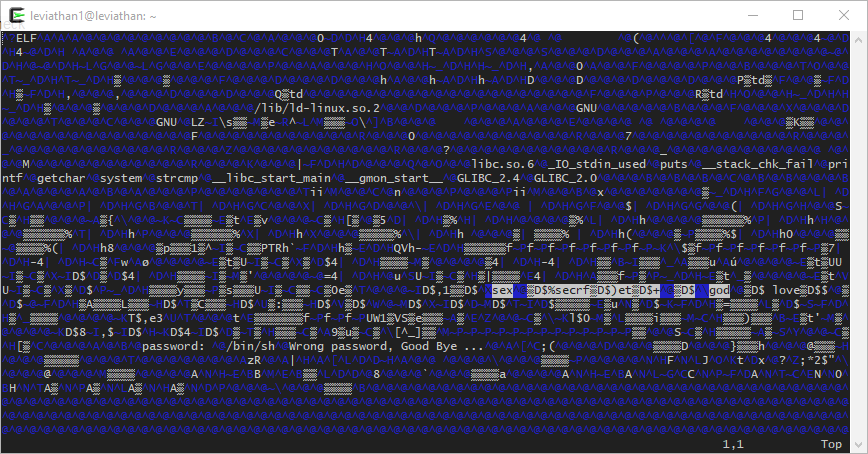
I noticed a couple of other strings through the vim window that I hadn’t seen before, namely sex and god. I wondered why the strings command hadn’t picked up on these, and so I checked the man pages. Apparently, strings looks for a minimum of four printable characters in a row, which explains why these got overlooked. This behavior can be changed through the -min-length flag though.
After trying them below, I was rewarded with a shell running as leviathan2.
leviathan1@leviathan:~$ ./check
password: god
Wrong password, Good Bye ...
leviathan1@leviathan:~$ ./check
password: sex
$ whoami
leviathan2
$ cat /etc/leviathan_pass/leviathan2
XXXXXXXXXX
$